Homeland Security Department shuts down as Democrats and Trump negotiate changes



©

©


© Courtesy of family

© Eric Gay

© Brenda Bazán

© Courtesy of family

Read more of this story at Slashdot.
January was a busy month for Haiku, with their monthly report listing a metric ton of smaller fixes, changes, and improvements. Perusing the list, a few things stand out to me, most notably continued work on improving Haiku’s touchpad support.
The remainder of samuelrp84’s patchset implementing new touchpad functionality was merged, including two-finger scrolling, edge motion, software button areas, and click finger support; and on the hardware side, driver support for Elantech “version 4” touchpads, with experimental code for versions 1, 2, and 3. (Version 2, at least, seems to be incomplete and had to be disabled for the time being.)
↫ Haiku’s January 2026 activity report
On a related note, the still-disabled I2C-HID saw a number of fixes in January, and the rtl8125 driver has been synced up with OpenBSD. I also like the changes to kernel_version, which now no longer returns some internal number like BeOS used to do, instead returning B_HAIKU_VERSION; the uname command was changed accordingly to use this new information. There’s some small POSIX compliance fixes, a bunch of work was done on unit tests, and a ton more.
Read more of this story at Slashdot.
We often lament Microsoft’s terrible stewardship of its Windows operating system, but that doesn’t mean that they never do anything right. In a blog post detailing changes and improvements coming to the Microsoft Store, the company announced something Windows users might actually like?
A new command-line interface for the Microsoft Store brings app discovery, installation and update management directly to your terminal. This enables developers and users with a new way to discover and install Store apps, without needing the GUI. The Store CLI is available only on devices where Microsoft Store is enabled.
↫ Giorgio Sardo at the Windows Blogs
Of course, this new command-line frontend to the Microsoft Store comes with commands to install, update, and search for applications in the store, but sadly, it doesn’t seem to come with an actual TUI for browsing and discovery, which is a shame. I sometimes find it difficult to use dnf to find applications, as it’s not always obvious which search terms to use, which exact spelling packagers are using, which words they use in the description, and so on. In other words, it may not always be clear if the search terms you’re using are the correct ones to find the application you need.
If package managers had a TUI to enable browsing for applications instead of merely searching for them, the process of using the command line to find and install applications would be much nicer. Arch has this third-party TUI called pacseek for its package manager, and it looks absolutely amazing. I’ve run into a rudimentary dnf TUI called dnfseek, but it’s definitely not as well-rounded as pacseek, and it also hasn’t seen any development since its initial release. I couldn’t find anything for apt, but there’s always aptitude, which uses ncurses and thus fulfills a similar role.
To really differentiate this new Microsoft Store command-line tool from winget, the company could’ve built a proper TUI, but instead it seems to just be winget with nicer formatted output that is limited to just the Microsoft Store. Nice, I guess.
Read more of this story at Slashdot.

©


© Victor J. Blue for The New York Times
The World Health Organization on Friday released a formal statement blasting a US-funded vaccine trial as "unethical," because it would withhold an established, safe, and potentially lifesaving vaccine against hepatitis B from some newborns in Guinea-Bissau, Africa.
"In its current form, and based on publicly available information, the trial is inconsistent with established ethical and scientific principles," the WHO concluded, after providing a bullet-point list of reasons the trial was harmful and low quality.
The trial has drawn widespread condemnation from health experts since notice of the US funding was published in the Federal Register in December. The notice revealed that the Centers for Disease Control and Prevention—under anti-vaccine Health Secretary Robert F. Kennedy Jr.—had awarded $1.6 million to Danish researchers for their non-competitive, unsolicited proposal to conduct the trial.


© Getty | BSIP
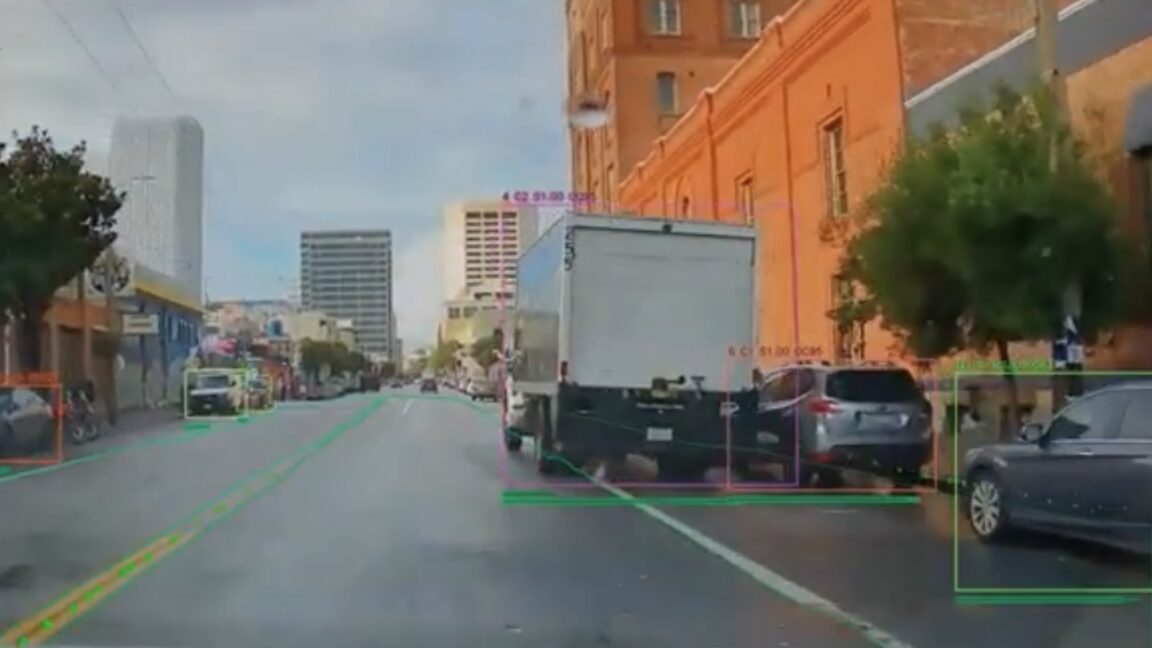
This spring, a Southern California beach town will become the first city in the country where municipal parking enforcement vehicles will use an AI system looking for potential bike lane violations.
Beginning in April, the City of Santa Monica will bring Hayden AI’s scanning technology to seven cars in its parking enforcement fleet, expanding beyond similar cameras already mounted on city buses.
“The more we can reduce the amount of illegal parking, the safer we can make it for bike riders,” Charley Territo, chief growth officer at Hayden AI, told Ars.

© Hayden AI
Verizon this week imposed a new roadblock for people who want to pay off device installment plans early in order to get their phones unlocked. The latest version of Verizon's device unlocking policy for postpaid customers imposes a 35-day waiting period when a customer pays off their device installment plan online or in the Verizon app.
Payments made over the phone also trigger a 35-day waiting period, as do payments made at Verizon Authorized Retailers. Getting an immediate unlock apparently requires paying off the device plan at a Verizon corporate store.
Unlocking a phone allows it to be used on another network, letting customers switch from one carrier to another. Previously, the 35-day waiting period for unlocks was only applied when a customer paid off the plan with a Verizon gift card.


© Aurich Lawson | Getty Images
Amazon and Flock Safety have ended a partnership that would've given law enforcement access to a vast web of Ring cameras.
The decision came after Amazon faced substantial backlash for airing a Super Bowl ad that was meant to be warm and fuzzy, but instead came across as disturbing and dystopian.
The ad begins with a young girl surprised to receive a puppy as a gift. It then warns that 10 million dogs go missing annually. Showing a series of lost dog posters, the ad introduces a new "Search Party" feature for Ring cameras that promises to revolutionize how neighbors come together to locate missing pets.


© Jagoda Matejczuk / 500px | 500px Prime
You might have noticed some reporting a few days ago that Android 17 was rolling out in beta form, but that didn't happen. For reasons Google still has not explained, the release was canceled. Two days later, Android 17 is here for real. If you've got a recent Pixel device, you can try the latest version today, but don't expect big changes just yet—there's still a long way to go before release.
Google will probably have more to say about feature changes for Android 17 in the coming months, but this first wide release is aimed mostly at testing system and API changes. One of the biggest changes in the beta is expanded support for adaptive apps, which ensures that apps can scale to different screen sizes. That makes apps more usable on large-screen devices like tablets and foldables with multiple displays.
We first saw this last year in Android 16, but developers were permitted to opt out of support. The new adaptive app roadmap puts an end to that. Any app that targets Android 17 (API level 37) must support resizing and windowed multitasking. Apps can continue to target the older API for the time being, but Google filters apps from the Play Store if they don't keep up.


© Ryan Whitwam
Spending time in a sauna can feel good, but it can also entail a little bit of suffering; after all, if the weather outside were the same as the temperature in a sauna, you’d probably want to hide out in the air conditioning all day. There’s something about unpleasant bodily experiences that makes us think they must be good for us, somehow, and so the sauna has gained a healthful reputation that it doesn’t entirely deserve. Here’s a rundown of what a sauna can and can’t do for you.
It is technically true that you can lose weight by sitting in a sauna, but that’s not because your body is torching fat; it’s because you’re sweating, and sweat is made of water, and water weighs something. As soon as you rehydrate—which you should—the scale will go right back to where it was at the beginning. After all, as I've discussed in the context of exercise, sweating doesn’t mean that you got a good workout or that you burned calories. It just means you were hot.
People who sell saunas and sauna services like to talk up their calorie-burning benefits, but there’s no evidence to suggest you burn significantly more calories sitting in a hot room than you would sitting on your couch at home. Some more skeptical websites cite a modest figure of 1.5 to 2 times as many calories as you would burn sitting at room temperature, but without a citation. If true, that’s about the same as the difference between sitting and standing—so you can skip that trip to the sauna and just spend half an hour standing around.
So why does your fitness tracker say you burned a ton of calories in the sauna? First of all, don't bring your phone in the sauna, it's bad for the battery. But since you did anyway, I'll explain. The calorie-burning algorithms on your watch are built to estimate your calorie burn from your heart rate under the assumption that you are exercising. If your heart rate increases but you are not exercising, the calculations aren't correct. The calorie burn during exercise comes from the fact that muscles all over your body are contracting over and over again. That is simply not what's happening when you sit in the sauna.
It’s 2026 and we as a society should be over this “detox” concept, which has been debunked time and time again. Ordinary inconveniences like being tired sometimes aren’t due to some secret toxins that are constantly poisoning you, and even if you do have health issues due to toxins, you should seek medical treatment and not expect smoothies or saunas to cure you.
Saunas and exercise both heat up your body and make you sweat, but there aren’t many similarities aside from that. Remember, exercise makes us stronger and improves our cardiovascular endurance (giving us a higher VO2max, for example). Sweating in a hot room doesn’t do that.
Even this rundown from an exercise science researcher, whose headline draws parallels between running and sitting in a sauna, includes the following disclaimer: "Before you contemplate cancelling your gym membership and investing the savings in a Jacuzzi, know that regular saunas or baths are unable to replicate all the health benefits of exercise training, such as promoting fat loss and increasing muscle mass. Using hot baths or saunas shouldn’t be considered as a substitute for exercise."
What that researcher does point out, after the disclaimer, is that there are a few lesser-known benefits of exercise that seem to be related to the increase in body heat and heart rate, rather than from the more obvious strain on our lungs or muscles.
When your body temperature rises, blood vessels near the surface of your skin dilate (get wider) and this process may help cell growth and repair. In other words, simply raising body temperature may be good for your blood vessels. That's not something we normally think about, but healthy blood vessels are a part of a healthy cardiovascular system.
If you find saunas relaxing—and many of us do—that can be a health benefit in itself. Now, this isn’t as concrete a benefit as it’s sometimes made out to be. You’re not going to cure your depression or reverse your heart disease just by relaxing in a sauna every now and then. But if you enjoy your sauna sessions, they could certainly contribute to lowering your stress levels and improving your mental health. Pro tip: If you don't have access to a sauna, a hot bath may have a lot of these effects as well.
For other medical conditions and athletic uses, the pros and cons of a sauna come down to the pros and cons of heat itself. If you have sore muscles, heat often feels good, so athletes often enjoy sauna sessions.
Some skin conditions respond well to the dry air of a sauna, while others can be exacerbated by dry air but could feel better with the humid air of a steam room. Use common sense and check with your medical provider if you want to use a sauna to manage a health condition.
If we’re talking about health benefits, it’s only fair to discuss risks as well. Saunas are reasonably safe, but people with medical conditions are often advised to steer clear, or to talk to a doctor before deciding to spend time in a sauna. This may include you if you are pregnant, have unusually high or low blood pressure, have epilepsy, or are taking stimulants, tranquilizers, or mind-altering drugs. Spending time in a sauna has also been linked to temporarily lowered fertility because heat impairs the production of sperm.
The main danger of a sauna is that you could overheat or dehydrate; severe heat illness and dehydration can both be life threatening, and people have died in saunas. Alcohol makes you more susceptible; half of the people who died in saunas, according to a Finnish study, were under the influence of alcohol. (The authors argue that the biggest danger is not alcohol itself, but allowing a drunk person to be in a sauna alone.) So if you choose to spend time in a sauna, be smart about it. Hydrate well, don’t go alone, and don’t expect the sauna to do things that saunas can’t do.

They actually did it. OpenAI officially deprecated GPT-4o on Friday, despite the model's particularly passionate fan base. This news shouldn't have been such a surprise. In fact, the company announced that Feb. 13 would mark the end of GPT-4o—as well as models like GPT-4.1, GPT-4.1 mini, and o4-mini—just over two weeks ago. However, whether you're one of the many who are attached to this model, or you simply know how dedicated 4o's user base is, you might be surprised OpenAI actually killed its most agreeable AI.
This isn't the first time the company depreciated the model, either. OpenAI previously shut down GPT-4o back in August, to coincide with the release of GPT-5. Users quickly revolted against the company, some because they felt GPT-5 was a poor upgrade compared to 4o, while others legitimately mourned connections they had developed with the model. The backlash was so strong that OpenAI relented, and rereleased the models it had deprecated, including 4o.
If you're a casual ChatGPT user, you might just use the app as-is, and assume the newest version tends to be the best, and wonder what all the hullabaloo surrounding these models is all about. After all, whether it's GPT-4o, or GPT-5.2, the model spits out generations that read like AI, complete with flowery word choices, awkward similes, and constant affirmations. 4o, however, does tend to lean even more into affirmations than other models, which is what some users love about it. But critics accuse it of being too agreeable: 4o is at the center of lawsuits accusing ChatGPT of enabling delusional thinking, and, in some cases, helping users take their own lives. As TechCrunch highlights, 4o is OpenAI's highest-scoring model for sycophancy.
I'm not sure where 4o's most devoted fans go from here, nor do I know how OpenAI is prepared to deal with the presumed backlash to this deprecation. But I know it's not a good sign that so many people feel this attached to an AI model.
Disclosure: Ziff Davis, Mashable’s parent company, in April 2025 filed a lawsuit against OpenAI, alleging it infringed Ziff Davis copyrights in training and operating its AI systems.

AI-powered browser extensions continue to be a popular vector for threat actors looking to harvest user information. Researchers at security firm LayerX have analyzed multiple campaigns in recent months involving malicious browser extensions, including the widespread GhostPoster scheme targeting Chrome, Firefox, and Edge. In the latest one—dubbed AiFrame—threat actors have pushed approximately 30 Chrome add-ons that impersonate well-known AI assistants, including Claude, ChatGPT, Gemini, Grok, and "AI Gmail." Collectively, these fakes have more than 300,000 installs.
The Chrome extensions identified as part of AiFrame look like legitimate AI tools commonly used for summarizing, chat, writing, and Gmail assistance. But once installed, they grant attackers wide-ranging remote access to the user's browser. Some of the capabilities observed include voice recognition, pixel tracking, and email content readability. Researchers note that extensions are broadly capable of harvesting data and monitoring user behavior.
Though the extensions analyzed by LayerX used a variety of names and branding, all 30 were found to have the same internal structure, logic, permissions, and backend infrastructure. Instead of implementing functionality locally on the user's device, they render a full-screen iframe that loads remote content as the extension's interface. This allows attackers to push changes silently at any time without a requiring Chrome Web Store update.
LayerX has a complete list of the names and extension IDs to refer to. Because threat actors use familiar and/or generic branding, such as "Gemini AI Sidebar" and "ChatGPT Translate," you may not be able to identify fakes at first glance. If you have an AI assistant installed in Chrome, go to chrome://extensions, toggle on Developer mode in the top-right corner, and search for the ID below the extension name. Remove any malicious add-ons and reset passwords.
As BleepingComputer reports, some of the malicious extensions have already been removed from the Chrome Web Store, but others remain. Several have received the "Featured" badge, adding to their legitimacy. Threat actors have also been able to quickly republish add-ons under new names using the existing infrastructure, so this campaign and others like it may persist. Always vet extensions carefully—don't just rely on a familiar name like ChatGPT—and note that even AI-powered add-ons from trusted sources can be highly invasive.



Read more of this story at Slashdot.
Read more of this story at Slashdot.

© Jim Wilson/The New York Times
Read more of this story at Slashdot.
Longtime fans of the cult TV show Mystery Science Theater 3000 know that the series’ one constant is change (well, that and bad movies).
The show’s cast and crew were in a near-constant state of flux, a byproduct of the show's existence as a perennial bubble show produced in the Twin Cities rather than a TV-and-comedy hub like New York or LA. It was rare, especially toward the middle of its 10-season original run on national TV, for the performers in front of the camera (and the writers’ room, since they were all the same people) to stay the same for more than a season or two.
Series creator Joel Hodgson embraced that spirit of change for the show's Kickstarter-funded, Netflix-aired revival in the mid-2010s, featuring a brand-new cast and mostly new writers. And that change only accelerated in the show's brief post-Netflix "Gizmoplex" era, which featured a revolving cast of performers that could change from episode to episode. Hodgson leaned into the idea that as long as there were silhouettes and puppets talking in front of a bad movie, it didn't matter much who was doing the talking.


© MST3K/RiffTrax
Read more of this story at Slashdot.
There are plenty of unanswered questions about the origin of life on Earth. But the research community has largely reached consensus that one of the key steps was the emergence of an RNA molecule that could replicate itself. RNA, like its more famous relative DNA, can carry genetic information. But it can also fold up into three-dimensional structures that act as catalysts. These two features have led to the suggestion that early life was protein-free, with RNA handling both heredity and catalyzing a simple metabolism.
For this to work, one of the reactions that the early RNAs would need to catalyze is the copying of RNA molecules, without which any sort of heritability would be impossible. While we've found a number of catalytic RNAs that can copy other molecules, none have been able to perform a key reaction: making a copy of themselves. Now, however, a team has found an incredibly short piece of RNA—just 45 bases long—that can make a copy of itself.
We have identified a large number of catalytic RNAs (generically called ribozymes, for RNA-based enzymes), and some of them can catalyze reactions involving other RNAs. A handful of these are ligases, which link together two RNA molecules. In some cases, they need these molecules to be held together by a third RNA molecule that base pairs with both of them. We've only identified a few that can act as polymerases, which add RNA bases to a growing molecule, one at a time, with each new addition base pairing with a template molecule.
© Laguna Design
There are tears in the audience as Patrick Darling’s song begins to play. It’s a heartfelt song written for his great-grandfather, whom he never got the chance to meet. But this performance is emotional for another reason: It’s Darling’s first time on stage with his bandmates since he lost the ability to sing two years ago.
The 32-year-old musician was diagnosed with amyotrophic lateral sclerosis (ALS) when he was 29 years old. Like other types of motor neuron disease (MND), it affects nerves that supply the body’s muscles. People with ALS eventually lose the ability to control their muscles, including those that allow them to move, speak, and breathe.
Darling’s last stage performance was over two years ago. By that point, he had already lost the ability to stand and play his instruments and was struggling to sing or speak. But recently, he was able to re-create his lost voice using an AI tool trained on snippets of old audio recordings. Another AI tool has enabled him to use this “voice clone” to compose new songs. Darling is able to make music again.
“Sadly, I have lost the ability to sing and play my instruments,” Darling said on stage at the event, which took place in London on Wednesday, using his voice clone. “Despite this, most of my time these days is spent still continuing to compose and produce my music. Doing so feels more important than ever to me now.”
Darling says he’s been a musician and a composer since he was around 14 years old. “I learned to play bass guitar, acoustic guitar, piano, melodica, mandolin, and tenor banjo,” he said at the event. “My biggest love, though, was singing.”
He met bandmate Nick Cocking over 10 years ago, while he was still a university student, says Cocking. Darling joined Cocking’s Irish folk outfit, the Ceili House Band, shortly afterwards, and their first gig together was in April 2014. Darling, who joined the band as a singer and guitarist, “elevated the musicianship of the band,” says Cocking.

But a few years ago, Cocking and his other bandmates started noticing changes in Darling. He became clumsy, says Cocking. He recalls one night when the band had to walk across the city of Cardiff in the rain: “He just kept slipping and falling, tripping on paving slabs and things like that.”
He didn’t think too much of it at the time, but Darling’s symptoms continued to worsen. The disease affected his legs first, and in August 2023, he started needing to sit during performances. Then he started to lose the use of his hands. “Eventually he couldn’t play the guitar or the banjo anymore,” says Cocking.
By April 2024, Darling was struggling to talk and breathe at the same time, says Cocking. For that performance, the band carried Darling on stage. “He called me the day after and said he couldn’t do it anymore,” Cocking says, his voice breaking. “By June 2024, it was done.” It was the last time the band played together.
Darling was put in touch with a speech therapist, who raised the possibility of “banking” his voice. People who are losing the ability to speak can opt to record themselves speaking and use those recordings to create speech sounds that can then be activated with typed text, whether by hand or perhaps using a device controlled by eye movements.
Some users have found these tools to be robotic sounding. But Darling had another issue. “By that stage, my voice had already changed,” he said at the event. “It felt like we were saving the wrong voice.”
Then another speech therapist introduced him to a different technology. Richard Cave is a speech and language therapist and a researcher at University College London. He is also a consultant for ElevenLabs, an AI company that develops agents and audio, speech, video, and music tools. One of these tools can create “voice clones”—realistic mimics of real voices that can be generated from minutes, or even seconds, of a person’s recorded voice.
Last year, ElevenLabs launched an impact program with a promise to provide free licenses to these tools for people who have lost their voices to ALS or other diseases, like head and neck cancer or stroke.
The tool is already helping some of those users. “We’re not really improving how quickly they’re able to communicate, or all of the difficulties that individuals with MND are going through physically, with eating and breathing,” says Gabi Leibowitz, a speech therapist who leads the program. “But what we are doing is giving them a way … to create again, to thrive.” Users are able to stay in their jobs longer and “continue to do the things that make them feel like human beings,” she says.
Cave worked with Darling to use the tool to re-create his lost speaking voice from older recordings.
“The first time I heard the voice, I thought it was amazing,” Darling said at the event, using the voice clone. “It sounded exactly like I had before, and you literally wouldn’t be able to tell the difference,” he said. “I will not say what the first word I made my new voice say, but I can tell you that it began with ‘f’ and ended in ‘k.’”

Re-creating his singing voice wasn’t as easy. The tool typically requires around 10 minutes of clear audio to generate a clone. “I had no high-quality recordings of myself singing,” Darling said. “We had to use audio from videos on people’s phones, shot in noisy pubs, and a couple of recordings of me singing in my kitchen.” Still, those snippets were enough to create a “synthetic version of [Darling’s] singing voice,” says Cave.
In the recordings, Darling sounded a little raspy and “was a bit off” on some of the notes, says Cave. The voice clone has the same qualities. It doesn’t sound perfect, Cave says—it sounds human.
“The ElevenLabs voice that we’ve created is wonderful,” Darling said at the event. “It definitely sounds like me—[it] just kind of feels like a different version of me.”
ElevenLabs has also developed an AI music generator called Eleven Music. The tool allows users to compose tracks, using text prompts to choose the musical style. Several well-known artists have also partnered with the company to license AI clones of their voices, including the actor Michael Caine, whose voice clone is being used to narrate an upcoming ElevenLabs documentary. Last month, the company released an album of 11 tracks created using the tool. “The Liza Minnelli track is really a banger,” says Cave.
Eleven Music can generate a song in a minute, but Darling and Cave spent around six weeks fine-tuning Darling’s song. Using text prompts, any user can “create music and add lyrics in any style [they like],” says Cave. Darling likes Irish folk, but Cave has also worked with a man in Colombia who is creating Colombian folk music. (The ElevenLabs tool is currently available in 74 languages.)
Last month, Cocking got a call from Cave, who sent him Darling’s completed track. “I heard the first two or three words he sang, and I had to turn it off,” he says. “I was just in bits, in tears. It took me a good half a dozen times to make it to the end of the track.”
Darling and Cave were making plans to perform the track live at the ElevenLabs summit in London on Wednesday, February 11. So Cocking and bandmate Hari Ma each arranged accompanying parts to play on the mandolin and fiddle. They had a couple of weeks to rehearse before they joined Darling on stage, two years after their last performance together.
“I wheeled him out on stage, and neither of us could believe it was happening,” says Cave. “He was thrilled.” The song was played as Darling remained on stage, and Cocking and Ma played their instruments live.
Cocking and Cave say Darling plans to continue to use the tools to make music. Cocking says he hopes to perform with Darling again but acknowledges that, given the nature of ALS, it is difficult to make long-term plans.
“It’s so bittersweet,” says Cocking. “But getting up on stage and seeing Patrick there filled me with absolute joy. I know Patrick really enjoyed it as well. We’ve been talking about it … He was really, really proud.”

Read more of this story at Slashdot.
Autonomous vehicles have a lot of potential. As long as you program them right, they won't speed, won't break traffic laws, and won't get drunk, high, abusive, or violent. And the technology has been getting much more capable, even as some of the hype has died down, taking some of the related companies with it. Waymo still easily leads the field and is already operating commercially in six cities across America, with a dozen more (plus London) coming soon. Waymos can even drop you off and pick you up at the airport in Phoenix and San Francisco.
Soon, Waymo will begin deploying its sixth-generation Waymo Driver, using upfitted Zeekr Ojai minivans, adding to the Jaguar I-Paces that have become so common on San Francisco streets and to its fleet of Hyundai Ioniq 5 electric vehicles. It has upgraded the cameras, lidar, and radar, meaning the cars can better sense their environments at night and in inclement weather. There are even microphones that can pick up sounds like sirens to better inform the robotaxi of the direction the emergency vehicle(s) are coming from.
But even with all these advances since the pod-like two-seater that predates even the Waymo name, there are still a few things that remain beyond a robotaxi's capabilities. Like closing a door a passenger left open on their way out. All the sophisticated sensors and high-powered computer processing in the world are useless if the car can't move until the door closes and there's no one there to give it a hand.


© Waymo
The founder of Amazon, Jeff Bezos, does not often post on the social media site owned by his rival Elon Musk. But on Monday, Bezos did, sharing a black-and-white image of a turtle emerging from the shadows on X.
The photo, which included no text, may have stumped some observers. Yet for anyone familiar with Bezos' privately owned space company, Blue Origin, the message was clear. The company’s coat of arms prominently features two turtles, a reference to one of Aesop’s Fables, "The Tortoise and the Hare," in which the slow and steady tortoise wins the race over a quicker but overconfident hare.
Bezos' foray into social media turtle trolling came about 12 hours after Musk made major waves in the space community by announcing that SpaceX was pivoting toward the Moon, rather than Mars, as a near-term destination. It represented a huge shift in Musk's thinking, as the SpaceX founder has long spoken of building a multi-planetary civilization on Mars.


© Jeff Bezos/X
We may earn a commission from links on this page. Deal pricing and availability subject to change after time of publication.
Augmented reality smart glasses blend digital content directly with the physical world, enabling hands-free device use, but a persistent pain point remains: Low brightness can make them unusable in certain settings. Many models max out at 400 to 600 nits, but a rare few exceed that, making them more practical in different conditions—like the Viture Luma Pro AR glasses, which can hit 1,000 nits of brightness.
Right now, the Viture Luma Pro AR glasses are over $200 off during Amazon's early President’s Day sale, bringing them to an an all-time low of $424 (originally $629).
The Viture Luma Pro glasses earned high marks from PCMag, which labeled them the “brightest smart glasses [we've] ever seen.” This higher peak brightness makes the glasses more functional in well-lit settings. They boast a 52-degree field of view (which translates to a 152-inch virtual screen) and have a 1200p (1920×1200 per eye) resolution with up to a 120Hz refresh rate. Along with a bright picture, they have dimmable lenses and focus adjustment dials for nearsighted users. In real-life testing at max resolution, some blurry edges can occur, these specs deliver deliver a bright, crisp, and sizable digital picture overall.
On the audio side, the built-in Harman-tuned speakers perform well but may struggle in a very noisy environment. The glasses don’t have integrated head-tracking features, but you can enable 3DOF with the brand’s free SpaceWalker software available for desktop and mobile and compatible with iOS, Android, Windows, and MacOS.
For those seeking a visually impressive monitor or virtual workstation that they can wear on their face (and reliance on software for motion-tracking isn’t a dealbreaker), the Viture Luma Pro AR glasses excel in most areas.

We may earn a commission from links on this page. Deal pricing and availability subject to change after time of publication.
Presidents' Day sales are around the corner, and the deals are coming in early; right now, Amazon has the latest Kindle Paperwhite from 2024 in "Like-New" conditions for $114.99 (originally $143.99). This Paperwhite in new condition would cost you $159.99, making the refurbished version a much cheaper choice to get while it lasts (discounted Kindle Paperwhites usually sell out quickly).
The Kindle Paperwhite is the most popular reading tablet from Amazon, and it's the best for most people, according to PCMag's "outstanding" review. It offers many improvements over the 11th-generation version from 2021—mainly a larger seven-inch display and a much faster boost in performance. It still retains all of the great attributes that made the previous version great, like a fully waterproof design with an IPX8 rating, enough storage to hold more than 10,000 books, and unlimited cloud storage. If you want an ad-free experience with some better features, get the Signature Edition.
If you're not sure if this is the right Kindle for you, check out the Colorsoft version—it offers color, so it can make reading manga or comics more lively. We also have a breakdown of every kind of Kindle to help you decide. If you already own the 11th generation, there might not be enough here to warrant an upgrade, unless you just want the latest Amazon has to offer. However, any devices older than that may be worth an upgrade for features like Bluetooth compatibility, which is great for audiobooks.
The screen features a 300 ppi (pixels per inch) display with 16 levels of background lighting, and optional warm lighting as well. I use this feature to read before bed and not strain my eyes. I also love the absurdly long battery life. This one is estimated at up to 12 weeks on a single charge, depending on your use and brightness settings.

We may earn a commission from links on this page.
If you own a home with an unfinished attic, you’ve probably thought about all that precious space and how you might make it more useful. Your attic already serves an important purpose in temperature and moisture regulation in the house, of course, but that doesn’t mean it can’t do more. If you’ve got the budget, you can transform an attic into a bedroom or office space, or a crisp, well-lit storage option.
If you don’t have the budget to really build out your attic, though, you can still make it into a more useful space, even if it’s small or slightly scary. With just a few modest purchases (and possibly some sweat equity), you can make your attic an ideal storage space.
Your first step towards making your attic useful is to make it safe to walk around. Even if your attic is shallow and standing up straight is impossible, having a stable surface will reduce your chances of falling through the ceiling.
Putting down plywood or oriented strand board (OSB) is a cheap and relatively easy option, but it’s also labor-intensive and pretty permanent. If you want a faster solution, floor panels like these from Attic Dek are sized to fit most standard joist spacings and are designed to just snap together, allowing you to quickly drop a floor into place without needing to cut them. They come with screws, and it’s a good idea to secure them in place, but if you just need a temporary floor that can bear weight (up to 250 pounds) you can just click them into place and bolt them down later.
If your attic isn’t wired up or lacks light fixtures, you don’t need to hire an electrician and spend a mountain of cash. Just pick up one or two of these rechargeable ceiling lights and stick them to the ceiling or overhead joist (literally—you place a magnetic sticker on the ceiling and that holds the light in place—no screws required). It’s motion-activated, so every time you haul yourself up into the attic, the light will come on and save you from stumbling about in the dark.
Once you have a sturdy, safe floor in your attic, you can start installing storage options. You could, of course, just pile up some boxes or bins and call it a day, but you can do a lot better than that without breaking the bank:
Installing some hanging rods designed for slanted surfaces (like an attic ceiling or rafters) will give you the option of hanging clothing or storage bags without cluttering up the floor.
A few cheap, adjustable shelving units like this one can add all the shelf space you need to keep bins of stuff organized and off the floor, making it easy to store or retrieve items.
If your attic is tight and trusses make it difficult to store anything, you can install some truss-friendly shelving. This can be a relatively easy DIY job involving screwing some support brackets into the trusses (as seen here). If you don’t have a floor in your attic, you have to avoid placing heavy storage boxes or bins directly on insulation—compressed insulation isn’t very effective. You can purchase some truss brackets that support plastic bins or other storage boxes off the floor.
Once you’ve got storage, you need a way to get stuff up into the attic, which can be more challenging than you expect. Carrying awkward, heavy boxes up flimsy, pull-down attic stairs is a recipe for accidents, so consider rigging up some mechanical assistance. You can spend a fair amount of money on a fancy lift system that will make bringing stuff up to your attic pretty easy, but if that’s too rich for your blood, you could opt for a simpler winch system that will allow you to haul up to 440lbs of stuff up there at a time. If that’s still a little too much, you could also opt for a classic pulley system, using good old-fashioned mechanical advantage to get your stuff up into the attic.

We may earn a commission from links on this page.
Who among us has not looked at a newly framed picture, then looked at their wall and thought, "Eh, surely I can eye-ball it this time." Hanging pictures should be an easy feat, but so often they end up uncentered or slightly crooked, causing us to add more holes the wall than intended or desired. The next time you hang pictures or artwork in your home, use one of these 10 hacks so they're level and evenly spaced on the first try.
A level is essential when hanging art—a frame that’s even slightly crooked will be an eyesore, and if you’re hanging multiple pieces in a group, it’s even more important that everything be level. If you forgot to grab your level, or you don’t have one, you can use a small ball, like a ping pong ball or a marble. Place it on top of the frame and adjust until the ball sits still, then mark it on the wall.
If your frame has two widely spaced hooks, knowing where to insert your nail, screw, or other fastener on the wall can be a mind-bending challenge. But if you have some painter’s tape on hand, it’s easy: Place a piece of tape across the back of the frame, with the top of the tape lined up with the top of the hooks. Mark the position of the hooks with a marker or pen, then remove the tape and place it on the wall at the desired height. Using a level, adjust the tape until it’s placed correctly. Then drive your nails right through the tape at the marked locations, remove the tape, and hang your picture. Here's a visual tutorial.
An alternative to the painter’s tape method is to use some toothpaste (or any gooey, sticky stuff that will wash off your wall easily). Mark the hooks on the back of the frame with a gob of toothpaste, check that it's level and at the desired height on your wall, then press the frame against the wall. The toothpaste will mark the precise spot where you need to drive your nails to hang the frame. Insert your fasteners, clean everything up, and hang that picture in the perfect spot. Here's a visual tutorial.
If you have spare cardboard (a cereal box will do) and a pin or thumbtack, you can make a little DIY tool that will make marking the spot for a hook or nail easy. Cut out a rectangle of cardboard, then cut a tab at the bottom that’s narrow enough to fit through the hook on the back of the frame. Slide the tab through, and push a pin or tack through from the back. Then push the picture into the wall at the right spot, and the pin will create a tiny hole where your hook or nail needs to be. Here's a visual tutorial.
Got the nail in the wall, but can’t seem to catch the hook on the picture frame? Get a piece of string and loop it around the nail, then adjust so the ends are even. Take both ends together and run them through the hook, then pull the string tight as you bring the frame toward the wall. The string will guide the hook right onto the nail, no guesswork required. Here's a visual tutorial.
If your frame uses a wire across the back to catch a nail or hook in the wall, you know that sometimes you question your own perception of reality as you repeatedly fail to catch the hook on the wire. There’s an easy hack: Grab a fork from the kitchen and place it on the nail or hook in the wall so it leans outward. Then hook the wire onto the stem of the fork and slide the frame down, letting the fork guide the wire down. When it’s hooked, remove the fork and admire your work. (And wash the fork, probably.) Here's a visual tutorial.
Hanging art on drywall and dread all the mess and trouble of drilling or nailing? Skip it by using Monkey Hooks instead. These are self-drilling pieces of wire—you just poke them through the wall with a tiny bit of elbow grease—that spin around and provide strong, secure hooks that can hold up to 50 pounds of weight, all without a single tool. Here's a visual tutorial.
If you’re going to be hanging multiple frames on the wall, grab some paper and create a template first. You can use wrapping paper, butcher paper or any kind of paper you have lying around or can get your hands on cheap (you can also use cardboard if that’s what you have on hand). Lay your frames out on the paper and trace them carefully. Then use the toothpaste or cardboard/nail hacks described above to mark where the nails need to be placed. Hang the template on the wall (ensuring it’s level), hammer in your nails, remove the template, and hang your frames. Here's a visual tutorial.
If you’re going to drill or nail into your walls to hang pictures, you’re going to get a lot of annoying dust all over the place, unless you use a very simple hack: Tape an envelope to the wall underneath where you’ll be drilling. It will catch all that dust and save you the extra step of vacuuming afterward. If you don’t have any envelopes (or tape), some Post-it Notes will do in a pinch—just fold one in half and stick it to the wall under the spot where you’ll be drilling, and it will catch that dust. You can combine more than one Post-it if you need to. Here's a visual tutorial.
If all else fails, and you need to hang a framed picture but you are short on time or patience, there’s a simple solution: Lick the back of your finger, curl it over the hanging hook on the back of the frame, and place it against the wall at the desired height (typically around 57-60 inches from the floor). Your own saliva will leave a faint, temporary mark on the wall where you can confidently place your hook without fuss or delay.

We may earn a commission from links on this page. Deal pricing and availability subject to change after time of publication.
The Insta360 Ace Pro 2 isn’t trying to win you over with just flashy specs, though it has plenty of those. It’s currently on sale (see more President’s Day sale here) for $489.99 on Amazon (down from $579.99), which also happens to be its lowest tracked price to date, according to price trackers.
This particular bundle includes some solid extras: two batteries, a flip screen hood, a leather case, a grip kit, and even a pocket printer to turn your favorite captures into prints. What you’re really getting, though, is a rugged, compact camera that delivers impressive 4K video, stable footage, and solid low-light performance—all in a body that’s waterproof, durable, and lightweight enough to clip onto your shirt or bike.
While Insta360 advertises 8K recording at 30fps, most people will likely stick to its excellent 4K modes, which go up to 120fps for smooth slow motion. It also offers a log profile (I-Log) for anyone who wants to color grade their footage later. The 2.5-inch flip-up screen is a standout—bigger than what you get on front-facing GoPro or DJI screens—making framing easier whether you're filming yourself or setting up a shot. The flip mechanism can be a bit clunky if you're constantly switching angles, but it doubles as a mount or even a POV bite grip in a pinch. Unlike its rivals, it doesn’t have built-in storage, so a microSD card (up to 1TB supported, sold separately) is a must-have from day one.
In daily use, the Ace Pro 2 delivers. The footage is sharp, the stabilization keeps things steady, and the built-in mics offer better-than-expected audio. There’s Bluetooth, Wi-Fi, USB-C 3.0, and solid app integration for both iOS and Android, making edits and uploads quick. Battery life is solid, and the included extras in this Flash Print Bundle add good value. It’s not leagues ahead of the GoPro Hero 13 or DJI Osmo Action 5 Pro, but it brings enough to the table—like the larger flip screen, smart mounting system, and polished app experience—to make it worth considering. If you’re in the market for a flagship action cam and prefer editing clean 4K footage over fiddling with massive 8K files, this is a smart pickup at its current price.

Ring isn't having the week it probably thought it would have. The Amazon-owned company aired an ad on Super Bowl Sunday for "Search Party," its new feature that turns a neighborhood's collective Ring cameras into one network, with the goal of locating lost dogs. Viewers, however, saw this as a major privacy violation—it doesn't take much to imagine using this type of surveillance tech to locate people, not pets.
The backlash wasn't just isolated to the ad, however. The controversy reignited criticisms of the company's partnership with Flock Safety, a security company that sells security cameras that track vehicles, notably for license plate recognition. But the partnership with Ring wasn't about tracking vehicles: Instead, Flock Safety's role was to make it easier for law enforcement agencies that use Flock Safety software to request Ring camera footage from users. Agencies could put in a request to an area where a crime supposedly took place, and Ring users would be notified about the request. They didn't have to agree to share footage, however.
Law enforcement could already request footage from Ring users, through the platform's existing "Community Requests" feature. But this partnership would let agencies make these requests directly through Flock Safety's software. If a user submitted footage following a request, Ring said that data would be "securely packaged" by Flock Safety and share to the agency through FlockOS or Flock Nova.
That partnership is officially over. On Friday, Ring published a blog post announcing the end of its relationship with Flock Safety. The company said, after a review, the integration "would require significantly more time and resources than anticipated." As such, both parties have agree to cancel the partnership.
Importantly, Ring says that since the integration never actually launched, no user footage was ever sent to Flock Safety—despite the company announcing the partnership four months ago. Social media influencers had spread the false claim that Flock Safety was seeding Ring footage directly to law enforcement agencies, such as ICE. While those claims are inaccurate, they were likely fueled by reporting from 404 Media that ICE has been able to access Flock Safety's data in its investigations. Had Ring's partnership with Flock Safety gone ahead, there would be legitimate cause to believe that agencies like ICE could tap into the footage Ring users had shared—even if those users were under the impression they were only sharing footage with local agencies to solve specific cases.
While privacy advocates will likely celebrate this news, the cancelled partnership has no effect on Community Requests. Law enforcement agencies will still be able to request footage from Ring users, and those users will still have a say in whether or not they send that footage. Ring sees the feature as an objective good, allowing users to voluntarily share footage that could help law enforcement solve important cases. In its announcement on Friday, Ring cited the December 2025 Brown University shooting, in which seven users shared 168 video clips with law enforcement. According to Ring, one of those videos assisted police in identifying the suspect's car, which, in turn, solved the case.

We may earn a commission from links on this page. Deal pricing and availability subject to change after time of publication.
The Sony HT-Z9F is down to $419.99 on Woot, a steep drop from its original price of $899.99. At this price, it becomes a far more accessible way to upgrade your TV audio without committing to a full AV receiver and multi-speaker setup. The deal is available for the next 16 days or until it sells out, whichever happens first. Prime members receive free standard shipping, while non-Prime customers pay $6. That said, shipping is not available to Alaska, Hawaii, APO addresses, or PO Boxes, and the purchase includes a 90-day Woot limited warranty. Discover more President's Day Sale deals and the best Tech deals during the early President's Day Sale here.
It’s a 3.1-channel soundbar, meaning it has left, right, and center speakers built in, plus a wireless subwoofer. That dedicated center channel is especially helpful for dialogue—it keeps voices clear and easy to follow, even during action scenes or loud background scores (meaning you do not need to ride the volume during conversations, then scramble to lower it when explosions hit). And then, there’s the wireless sub, which adds weight to action movies and bass-heavy playlists. It is not room-shaking, but it gives enough low-end punch to feel cinematic in a living room setting.
Sony markets the HT-Z9F as Dolby Atmos-enabled, but it does not have upward-firing drivers or rear satellite speakers. Instead, it relies on Sony’s S-Force Pro Front Surround and Vertical Surround Engine to simulate height and surround effects. That processing does create a wider sound field than basic stereo, but everything still feels anchored to the front of the room. Overhead effects lack the distinct placement you would get from true Atmos speakers bouncing sound off the ceiling. If you are upgrading from built-in TV speakers, the improvement will be obvious. But if you expect a fully immersive surround with objects flying above and behind you, this will not deliver that experience.
As for its connectivity, you get two full HDMI inputs that handle all major audio formats, plus HDMI ARC for TV connection. You also get Bluetooth, wifi, and built-in Chromecast for streaming music directly from your phone or apps. The design looks premium and feels sturdy, which helps it blend into a midrange or high-end setup. The tradeoff is limited sound customization. There are preset EQ modes, but no detailed treble or bass adjustments. At $419.99, the HT-Z9F makes sense for someone who values clear dialogue and solid bass, with wide-format support. Those chasing a true Atmos surround setup with discrete height channels may want to look elsewhere.

The team behind Tyr started 2025 with little to show in our quest to produce a Rust GPU driver for Arm Mali hardware, and by the end of the year, we were able to play SuperTuxKart (a 3D open-source racing game) at the Linux Plumbers Conference (LPC). Our prototype was a joint effort between Arm, Collabora, and Google; it ran well for the duration of the event, and the performance was more than adequate for players. Thankfully, we picked up steam at precisely the right moment: Dave Airlie just announced in the Maintainers Summit that the DRM subsystem is only “
↫ Daniel Almeida at LWN.netabout a year away” from disallowing new drivers written in C and requiring the use of Rust. Now it is time to lay out a possible roadmap for 2026 in order to upstream all of this work.
A very detailed look at what the team behind Tyr is trying to achieve with their Rust GPU driver for Arm Mali chips.
Read more of this story at Slashdot.
Read more of this story at Slashdot.

©
Read more of this story at Slashdot.
This is today’s edition of The Download, our weekday newsletter that provides a daily dose of what’s going on in the world of technology.
US deputy health secretary: Vaccine guidelines are still subject to change
Over the past year, Jim O’Neill has become one of the most powerful people in public health. As the US deputy health secretary, he holds two roles at the top of the country’s federal health and science agencies. He oversees a department with a budget of over a trillion dollars. And he signed the decision memorandum on the US’s deeply controversial new vaccine schedule.
He’s also a longevity enthusiast. In an exclusive interview with MIT Technology Review earlier this month, O’Neill described his plans to increase human healthspan through longevity-focused research supported by ARPA-H, a federal agency dedicated to biomedical breakthroughs. Fellow longevity enthusiasts said they hope he will bring attention and funding to their cause.
At the same time, O’Neill defended reducing the number of broadly recommended childhood vaccines, a move that has been widely criticized by experts in medicine and public health. Read the full story.
—Jessica Hamzelou
The myth of the high-tech heist
Making a movie is a lot like pulling off a heist. That’s what Steven Soderbergh—director of the Ocean’s franchise, among other heist-y classics—said a few years ago. You come up with a creative angle, put together a team of specialists, figure out how to beat the technological challenges, rehearse, move with Swiss-watch precision, and—if you do it right—redistribute some wealth.
But conversely, pulling off a heist isn’t much like the movies. Surveillance cameras, computer-controlled alarms, knockout gas, and lasers hardly ever feature in big-ticket crime. In reality, technical countermeasures are rarely a problem, and high-tech gadgets are rarely a solution. Read the full story.
—Adam Rogers
This story is from the next print issue of MIT Technology Review magazine, which is all about crime. If you haven’t already, subscribe now to receive future issues once they land.
RFK Jr. follows a carnivore diet. That doesn’t mean you should.
Americans have a new set of diet guidelines. Robert F. Kennedy Jr. has taken an old-fashioned food pyramid, turned it upside down, and plonked a steak and a stick of butter in prime positions.
Kennedy and his Make America Healthy Again mates have long been extolling the virtues of meat and whole-fat dairy, so it wasn’t too surprising to see those foods recommended alongside vegetables and whole grains (despite the well-established fact that too much saturated fat can be extremely bad for you).
Some influencers have taken the meat trend to extremes, following a “carnivore diet.” A recent review of research into nutrition misinformation on social media found that a lot of shared diet information is nonsense. But what’s new is that some of this misinformation comes from the people who now lead America’s federal health agencies. Read the full story.
—Jessica Hamzelou
This article first appeared in The Checkup, MIT Technology Review’s weekly biotech newsletter. To receive it in your inbox every Thursday, and read articles like this first, sign up here.
The must-reads
I’ve combed the internet to find you today’s most fun/important/scary/fascinating stories about technology.
1 The Trump administration has revoked a landmark climate ruling
In its absence, it can erase the limits that restrict planet-warming emissions. (WP $)
+ Environmentalists and Democrats have vowed to fight the reversal. (Politico)
+ They’re seriously worried about how it will affect public health. (The Hill)
2 An unexplained wave of bot traffic is sweeping the web
Sites across the world are witnessing automated traffic that appears to originate from China. (Wired $)
3 Amazon’s Ring has axed its partnership with Flock
Law enforcement will no longer be able to request Ring doorbell footage from its users. (The Verge)
+ Ring’s recent TV ad for a dog-finding feature riled viewers. (WSJ $)
+ How Amazon Ring uses domestic violence to market doorbell cameras. (MIT Technology Review)
4 Americans are taking the hit for almost all of Trump’s tariffs
Consumers and companies in the US, not overseas, are shouldering 90% of levies. (Reuters)
+ Trump has long insisted that his tariffs costs will be borne by foreign exporters. (FT $)
+ Sweeping tariffs could threaten the US manufacturing rebound. (MIT Technology Review)
5 Meta and Snap say Australia’s social media ban hasn’t affected business
They’re still making plenty of money amid the country’s decision to ban under-16s from the platforms. (Bloomberg $)
+ Does preventing teens from going online actually do any good? (Economist $)
6 AI workers are selling their shares before their firms go public
Cashing out early used to be a major Silicon Valley taboo. (WSJ $)
7 Elon Musk posted about race almost every day last month
His fixation on a white racial majority appears to be intensifying. (The Guardian)
+ Race is a recurring theme in the Epstein emails, too. (The Atlantic $)
8 The man behind a viral warning about AI used AI to write it
But he stands behind its content.. (NY Mag $)
+ How AI-generated text is poisoning the internet. (MIT Technology Review)
9 Influencers are embracing Chinese traditions ahead of the New Year 
On the internet, no one knows you’re actually from Wisconsin. (NYT $)
10 Australia’s farmers are using AI to count sheep 
No word on whether it’s helping them sleep easier, though. (FT $)
Quote of the day
“Ignoring warning signs will not stop the storm. It puts more Americans directly in its path.”
—Former US secretary of state John Kerry takes aim at the US government’s decision to repeal the key rule that allows it to regulate climate-heating pollution, the Guardian reports.
One more thing

The Vera C. Rubin Observatory is ready to transform our understanding of the cosmos
High atop Chile’s 2,700-meter Cerro Pachón, the air is clear and dry, leaving few clouds to block the beautiful view of the stars. It’s here that the Vera C. Rubin Observatory will soon use a car-size 3,200-megapixel digital camera—the largest ever built—to produce a new map of the entire night sky every three days.
Findings from the observatory will help tease apart fundamental mysteries like the nature of dark matter and dark energy, two phenomena that have not been directly observed but affect how objects are bound together—and pushed apart.
A quarter-century in the making, the observatory is poised to expand our understanding of just about every corner of the universe. Read the full story.
—Adam Mann
We can still have nice things
A place for comfort, fun and distraction to brighten up your day. (Got any ideas? Drop me a line or skeet ’em at me.)
+ Why 2026 is shaping up to be the year of the pop comeback.
+ Almost everything we thought we knew about Central America’s Maya has turned out to be completely wrong.
+ The Bigfoot hunters have spoken!
+ This fun game puts you in the shoes of a distracted man trying to participate in a date while playing on a GameBoy.


© Getty Images

© Yuri Kadobnov

© International Skating Union via Getty Images

© Matthew Stockman

©