
Rizwan Patel, Global Head Cloud, InfoSec and Emerging Technologies, Altimetrik
Global commerce no longer pauses between festivals; it moves continuously across markets, moments, and geographies. India's Diwali and Navratri have passed, yet the digital intensity they generated merely sets the stage for what comes next. Christmas shopping surges are building momentum across global markets, followed closely by fiscal closures and Lunar New Year preparations across Asia. What was once a sequence of seasonal events has become a single, continuous stress test of enterprise infrastructure and
digital trust.
Adversarial AI operates inside this same cycle, and it never takes holidays. While technology leaders finalize year-end campaigns, automated threat networks run relentless reconnaissance against digital platforms, learning transaction patterns, mapping authentication architectures, and calculating optimal breach windows.
The asymmetry is significant: enterprises expand transaction capacity during high-volume periods but rarely scale detection capabilities at the same speed. Adversarial systems adapt instantly, while human teams operate on predictable shifts.
Every vendor integration, partner
API, or cross-border payment is now part of a shared attack surface. Reliability and trust are no longer defined by uptime alone but by resilience under pressure. The next breach may not strike when systems are weakest—it may strike when commerce is strongest. The real question for technology leaders is no longer when adversarial AI will test their systems, but whether their defenses can keep pace when it does.
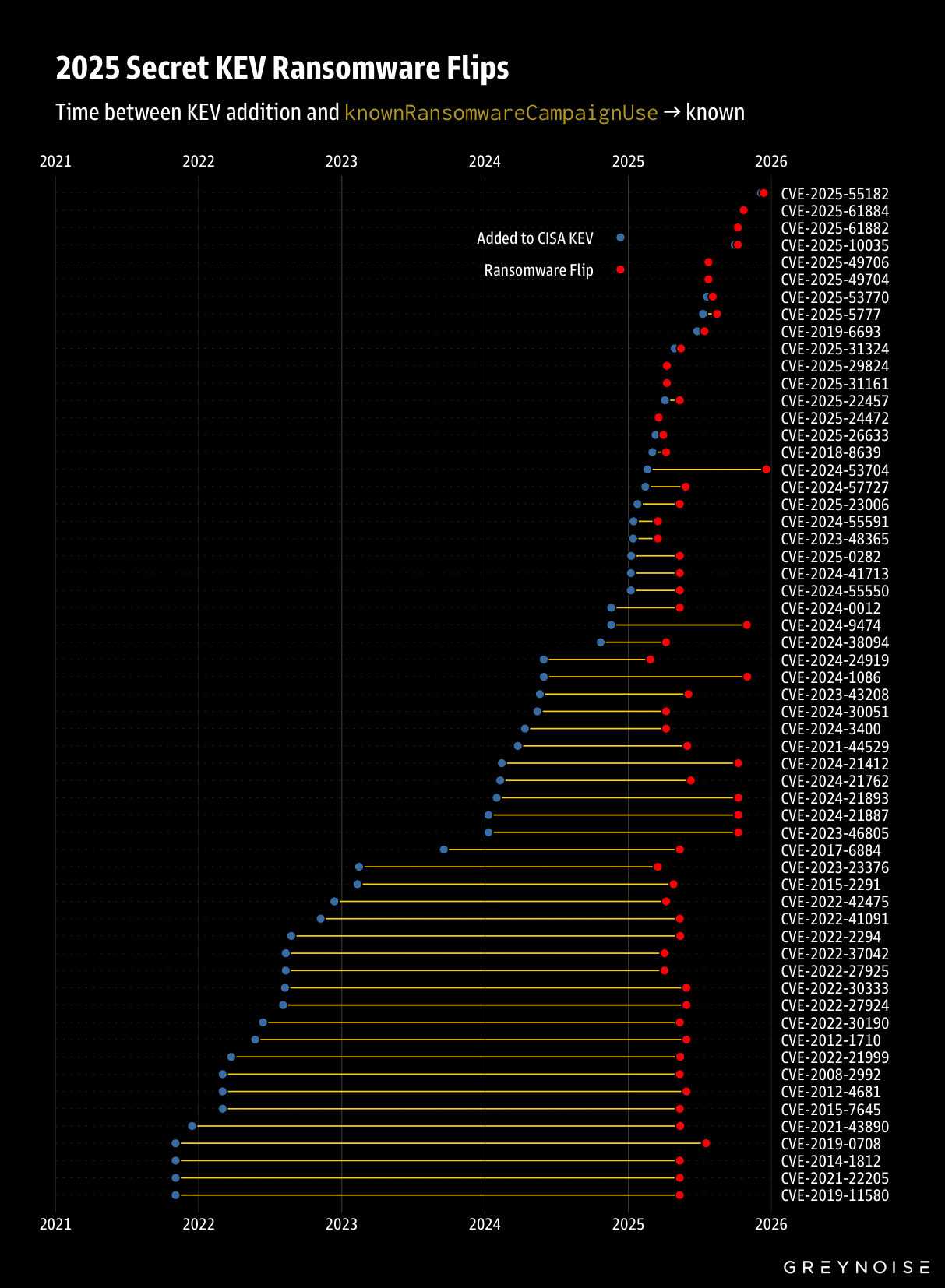
The Global Commerce Vulnerability Window
High-volume shopping periods create a concentrated attack surface that threat actors
exploit with precision. During the 2024
holiday season, December recorded 574 ransomware incidents, the highest monthly volume since monitoring began in 2021 according to
NCC Group's Threat Pulse report. The trend overturns historical patterns where December once saw slower attack activity during year-end breaks.
Cybersecurity experts increasingly refer to these periods as the Global Commerce
Vulnerability Window, marked by intense transaction volumes and limited human oversight across regions that shift like moving targets. As one market reaches its festive peak, adversarial networks redirect focus to the next, maintaining continuous pressure on enterprise systems.
The exposure extends deep into B2B ecosystems that enable these surges. Breaches on consumer-facing platforms can cascade through partner networks, exposing critical dependencies across cloud, financial, and logistics systems. A single incident during a client’s key revenue window can erode partner confidence, delay renewals, and weaken market standing while competitors seize the opportunity to advance.
The Strategic Leadership Playbook
Enterprise leaders navigating perpetual threat cycles must architect their
security posture around three interdependent capabilities that operate as integrated systems rather than isolated functions.
Intelligent Trust transforms security from an invisible assumption into a tangible asset. Explainable AI systems must demonstrate their decision-making logic to both technical teams and business stakeholders. Real-time consent management platforms show customers exactly how their
data moves through your infrastructure. During high-volume integrations, visible trust indicators such as verified credentials, anomaly alerts, and transparent data workflows help sustain confidence across partners. Trust becomes an operational metric, tracked and improved with the same rigor as uptime or throughput.
Dynamic Compliance treats regulatory adherence as a living system rather than a periodic audit exercise. Laws such as the EU’s GDPR, the U.S. CCPA, India’s DPDP Act, and the EU AI Act emphasize consent, accountability, and transparency across data and AI systems. Additionally, consent-first APIs, continuous monitoring, and automated audit trails ensure alignment across jurisdictions. Treating compliance as a living system builds trust and resilience in an environment where both regulations and
risks advance continuously.
Autonomous Resilience represents the frontier where agentic systems deliver measurable business value. Guardian Agents operate as intelligent, goal-oriented systems that function within defined governance boundaries. These agents continuously scan transaction patterns for data anomalies, detect adversarial behavior through behavioral analysis, and initiate mitigation protocols automatically. They coordinate with human oversight teams to escalate critical decisions or accept override commands. Most importantly, they evolve through machine learning as threat patterns shift, ensuring your defense posture adapts faster than manual processes allow.
This shift from reactive monitoring to self-governed prevention reduces both detection time and response resource requirements, allowing security teams to focus on architecture and strategy rather than tactical firefighting.
The AI Paradox Driving Next-Generation Defense
AI now defines both sides of the
cybersecurity equation. According to
The IBM 2025 Cost of a Data Breach Report while AI-enabled defenses save organizations nearly $1.9 million per breach, 13% of enterprises faced breaches in AI models or applications often owing to weak access controls.
This paradox defines today’s leadership challenge. Autonomous systems deliver measurable advantage, but must remain adaptive, governed, and accountable. Guardian Agents exemplify this evolution through continuous behavioural learning, establishing baselines for normal activity and detecting deviations before traditional defenses respond.
Their orchestration model allows coordination across distributed endpoints, sharing intelligence while preserving local decision authority. Each automated response is mapped through audit trails to the specific anomaly that triggered it, enabling transparency and human validation. This alignment of machine precision and human oversight ensures accountability even as response speeds surpass human reaction times.
As enterprises expand across jurisdictions and regulatory frameworks, this transition from autonomous to adaptive defense defines the next frontier.
The real test of leadership now lies in redefining what resilience means in an era where intelligence itself is the battlefield. AI will not wait for regulation, nor will adversaries wait for readiness. The future belongs to enterprises that can operationalize foresight, building systems that anticipate change, adapt without instruction, and uphold trust even under attack. Those that succeed will not only secure their data but shape the digital order that follows.
(This article reflects the author’s analysis and personal viewpoints and is intended for informational purposes only. It should not be construed as legal or regulatory advice.)






















 Source: Salesforce[/caption]
Source: Salesforce[/caption]

