Law enforcement agencies in the United States and Europe today announced Operation Endgame, a coordinated action against some of the most popular cybercrime platforms for delivering ransomware and data-stealing malware. Dubbed “the largest ever operation against botnets,” the international effort is being billed as the opening salvo in an ongoing campaign targeting advanced malware “droppers” or “loaders” like IcedID, Smokeloader and Trickbot.
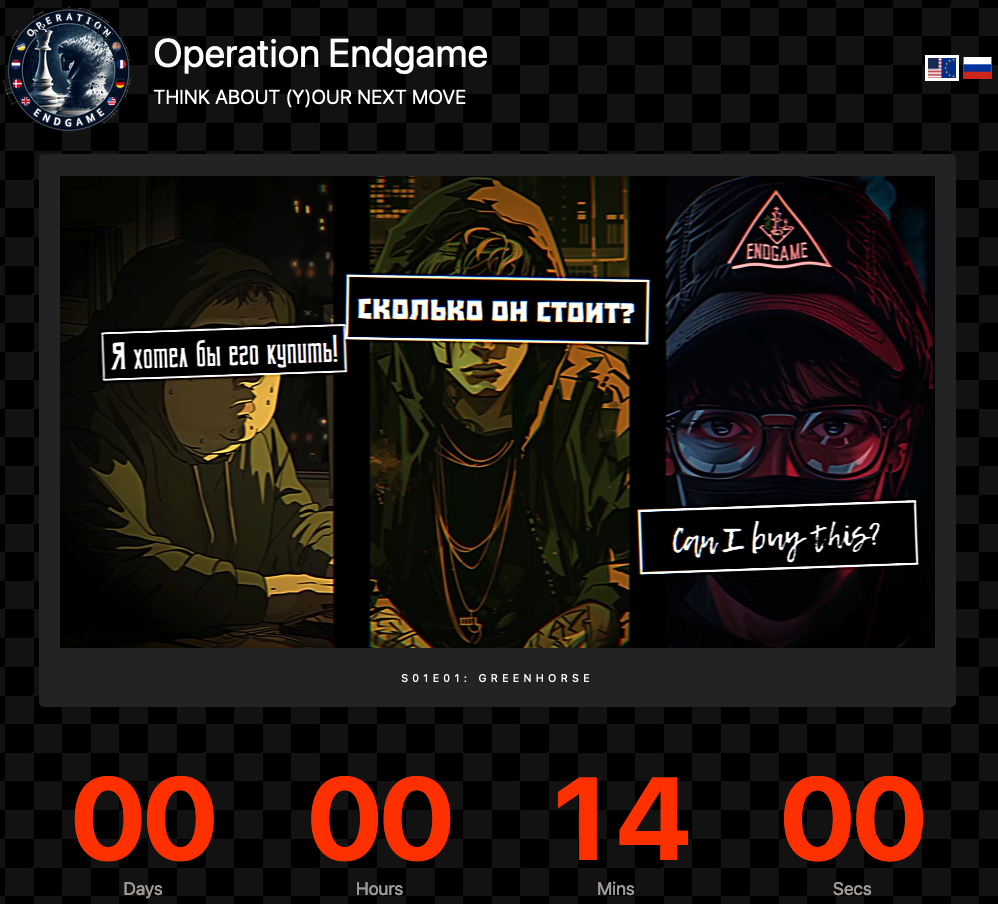
A frame from one of three animated videos released today in connection with Operation Endgame.
Operation Endgame targets the cybercrime ecosystem supporting droppers/loaders, slang terms used to describe tiny, custom-made programs designed to surreptitiously install malware onto a target system. Droppers are typically used in the initial stages of a breach, and they allow cybercriminals to bypass security measures and deploy additional harmful programs, including viruses, ransomware, or spyware.
Droppers like IcedID are most often deployed through email attachments, hacked websites, or bundled with legitimate software. For example, cybercriminals have long used paid ads on Google to trick people into installing malware disguised as popular free software, such as Microsoft Teams, Adobe Reader and Discord. In those cases, the dropper is the hidden component bundled with the legitimate software that quietly loads malware onto the user’s system.
Droppers remain such a critical, human-intensive component of nearly all major cybercrime enterprises that the most popular have turned into full-fledged cybercrime services of their own. By targeting the individuals who develop and maintain dropper services and their supporting infrastructure, authorities are hoping to disrupt multiple cybercriminal operations simultaneously.
According to a statement from the European police agency Europol, between May 27 and May 29, 2024 authorities arrested four suspects (one in Armenia and three in Ukraine), and disrupted or took down more than 100 Internet servers in Bulgaria, Canada, Germany, Lithuania, the Netherlands, Romania, Switzerland, the United Kingdom, United States and Ukraine. Authorities say they also seized more than 2,000 domain names that supported dropper infrastructure online.
In addition, Europol released information on eight fugitives suspected of involvement in dropper services and who are wanted by Germany; their names and photos were added to Europol’s “Most Wanted” list on 30 May 2024.

A “wanted” poster including the names and photos of eight suspects wanted by Germany and now on Europol’s “Most Wanted” list.
“It has been discovered through the investigations so far that one of the main suspects has earned at least EUR 69 million in cryptocurrency by renting out criminal infrastructure sites to deploy ransomware,” Europol wrote. “The suspect’s transactions are constantly being monitored and legal permission to seize these assets upon future actions has already been obtained.”
There have been numerous such coordinated malware takedown efforts in the past, and yet often the substantial amount of coordination required between law enforcement agencies and cybersecurity firms involved is not sustained after the initial disruption and/or arrests.
But a new website erected to detail today’s action — operation-endgame.com — makes the case that this time is different, and that more takedowns and arrests are coming. “Operation Endgame does not end today,” the site promises. “New actions will be announced on this website.”

A message on operation-endgame.com promises more law enforcement and disruption actions.
Perhaps in recognition that many of today’s top cybercriminals reside in countries that are effectively beyond the reach of international law enforcement, actions like Operation Endgame seem increasingly focused on mind games — i.e., trolling the hackers.
Writing in this month’s issue of Wired, Matt Burgess makes the case that Western law enforcement officials have turned to psychological measures as an added way to slow down Russian hackers and cut to the heart of the sweeping cybercrime ecosystem.
“These nascent psyops include efforts to erode the limited trust the criminals have in each other, driving subtle wedges between fragile hacker egos, and sending offenders personalized messages showing they’re being watched,” Burgess wrote.
When authorities in the U.S. and U.K. announced in February 2024 that they’d infiltrated and seized the infrastructure used by the infamous LockBit ransomware gang, they borrowed the existing design of LockBit’s victim shaming website to link instead to press releases about the takedown, and included a countdown timer that was eventually replaced with the personal details of LockBit’s alleged leader.

The feds used the existing design on LockBit’s victim shaming website to feature press releases and free decryption tools.
The Operation Endgame website also includes a countdown timer, which serves to tease the release of several animated videos that mimic the same sort of flashy, short advertisements that established cybercriminals often produce to promote their services online. At least two of the videos include a substantial amount of text written in Russian.
The coordinated takedown comes on the heels of another law enforcement action this week against what the director of the FBI called “likely the world’s largest botnet ever.” On Wednesday U.S. Department of Justice (DOJ) announced the arrest of YunHe Wang, the alleged operator of the ten-year-old online anonymity service 911 S5. The government also seized 911 S5’s domains and online infrastructure, which allegedly turned computers running various “free VPN” products into Internet traffic relays that facilitated billions of dollars in online fraud and cybercrime.