TCE Cyberwatch: Weekly Roundup Highlights AI Risks, Data Breaches, and Legal Battles



 Source: NIST NVD Status Updates[/caption]
"Our goal is to build a program that is sustainable for the long term and to support the automation of vulnerability management, security measurement and compliance," the institute said.
NIST reaffirmed its commitment to maintaining and modernizing the NVD, stating, "NIST is fully committed to preserving and updating this vital national resource, which is crucial for building trust in information technology and fostering innovation."
Source: NIST NVD Status Updates[/caption]
"Our goal is to build a program that is sustainable for the long term and to support the automation of vulnerability management, security measurement and compliance," the institute said.
NIST reaffirmed its commitment to maintaining and modernizing the NVD, stating, "NIST is fully committed to preserving and updating this vital national resource, which is crucial for building trust in information technology and fostering innovation."

"To date, we do not believe this activity is caused by any vulnerability, misconfiguration, or malicious activity within the Snowflake product," the cloud storage giant said in a statement today.Snowflake's AI Data Cloud platform serves more than 9,000 customers, including major companies such as Adobe, AT&T, Capital One, DoorDash, HP, JetBlue, Mastercard, Micron, NBC Universal, Nielsen, Novartis, Okta, PepsiCo, Siemens, US Foods, Western Union, and Yamaha, among others.
"We believe this is the result of ongoing industry-wide, identity-based attacks with the intent to obtain customer data. Research indicates that these types of attacks are performed with our customers’ user credentials that were exposed through unrelated cyber threat activity.Snowflake has notified the "limited" number of customers about these attacks and urged them to enhance their account security by enabling multi-factor authentication (MFA).

 Source: Carrier Product Security Advisory[/caption]
Successful compromise could allow an attacker to install programs, view, edit, modify data, delete data from the platform or create new user accounts with full privileges. However, this depends on the access level of accounts that had been compromised in the event of an attack. The impact of a potential attack could be lower on systems configured with low level of user access.
The vulnerabilities affect all LenelS2 NetBox versions prior to 5.6.2. The identified vulnerabilities are as follows:
Source: Carrier Product Security Advisory[/caption]
Successful compromise could allow an attacker to install programs, view, edit, modify data, delete data from the platform or create new user accounts with full privileges. However, this depends on the access level of accounts that had been compromised in the event of an attack. The impact of a potential attack could be lower on systems configured with low level of user access.
The vulnerabilities affect all LenelS2 NetBox versions prior to 5.6.2. The identified vulnerabilities are as follows:
 Source: cisecurity.org[/caption]
Source: cisecurity.org[/caption]


 Apache Tomcat compromised to spread malware by Andariel APT. (Credit: Ahnlab)[/caption]
Apache Tomcat compromised to spread malware by Andariel APT. (Credit: Ahnlab)[/caption]



 Source: Hawk Eye App on Android[/caption]
Source: Hawk Eye App on Android[/caption]
 What is noteworthy about the above examples is that all these users had filed complaints only in May 2024, which suggests that the data from the Hawk Eye App was hacked this month.
What is noteworthy about the above examples is that all these users had filed complaints only in May 2024, which suggests that the data from the Hawk Eye App was hacked this month.

As per recent reports a new social engineering attack attributed to the North Korea-linked Kimsuky hacking group is targeting human rights activists using fake Facebook accounts. This tactic, involving fictitious identities, marks a significant shift from their typical email-based spear-phishing strategies. According to a report by South Korean cybersecurity firm Genians, the attackers pose as […]
The post Alert: Kimsuky Hacking Group Targets Human Rights Activists appeared first on TuxCare.
The post Alert: Kimsuky Hacking Group Targets Human Rights Activists appeared first on Security Boulevard.

 Source: SEC[/caption]
Source: SEC[/caption]


 LilacSquid Initial Access and Activity. (Credit: Cisco Talos)[/caption]
Once a system is compromised through exploiting vulnerabilities on internet facing devices, LilacSquid deploys multiple access tools, including MeshAgent, SSF, InkLoader, and PurpleInk.
[caption id="attachment_73286" align="aligncenter" width="1024"]
LilacSquid Initial Access and Activity. (Credit: Cisco Talos)[/caption]
Once a system is compromised through exploiting vulnerabilities on internet facing devices, LilacSquid deploys multiple access tools, including MeshAgent, SSF, InkLoader, and PurpleInk.
[caption id="attachment_73286" align="aligncenter" width="1024"] LilacSquid's Lateral Movement via RDP. (Credit: Cisco Talos)[/caption]
MeshAgent, downloaded using bitsadmin utility, connects to its command and control (C2) server, conducts reconnaissance, and activates other implants.
On the other hand InkLoader, a .NET-based malware loader, is used when RDP credentials are compromised. It persists across reboots and executes PurpleInk, with the infection chain tailored for remote desktop sessions.
LilacSquid's Lateral Movement via RDP. (Credit: Cisco Talos)[/caption]
MeshAgent, downloaded using bitsadmin utility, connects to its command and control (C2) server, conducts reconnaissance, and activates other implants.
On the other hand InkLoader, a .NET-based malware loader, is used when RDP credentials are compromised. It persists across reboots and executes PurpleInk, with the infection chain tailored for remote desktop sessions.
"Although QuasarRAT has been available to threat actors since at least 2014, we observed PurpleInk being actively developed starting in 2021 and continuing to evolve its functionalities separate from its parent malware family."It features robust remote access capabilities, including process enumeration, file manipulation, system information gathering, remote shell access, and proxy server communication. Different variants of PurpleInk exhibit varying functionalities, with some stripped-down versions retaining core capabilities to evade detection. InkBox, an older loader used by LilacSquid, reads from a hardcoded file path on disk, decrypts its contents, and runs PurpleInk. Since 2023, LilacSquid has modularized the infection chain, with PurpleInk running as a separate process via InkLoader. [caption id="attachment_73282" align="aligncenter" width="1024"]
 PurpleInk Activation Chain (Credit: Cisco Talos)[/caption]
Post-exploitation, MeshAgent activates other tools like SSF and PurpleInk. MeshAgent, configured with MSH files, allows operators to control infected devices extensively, managing files, viewing and controlling desktops, and gathering device information.
PurpleInk Activation Chain (Credit: Cisco Talos)[/caption]
Post-exploitation, MeshAgent activates other tools like SSF and PurpleInk. MeshAgent, configured with MSH files, allows operators to control infected devices extensively, managing files, viewing and controlling desktops, and gathering device information.
PurpleInk: 2eb9c6722139e821c2fe8314b356880be70f3d19d8d2ba530adc9f466ffc67d8
Network IOCs
67[.]213[.]221[.]6 192[.]145[.]127[.]190 45[.]9[.]251[.]14 199[.]229[.]250[.]142




“There is no evidence that any of this information has been or will be publicly disclosed, or that any information was or will be misused for fraudulent purposes as a result of this incident, but we are communicating this so that affected individuals can take the steps outlined below to protect yourself.”The Leash Group is offering free credit monitoring and remediation services to affected individuals, and additional guidance on dealing with suspected breaches of personal information. No perpetrator has been identified or named as being responsible for the attack, and the potential impact of the breach is still being assessed. Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
Media reports claim that cybersecurity experts have recently unveiled new details about a remote access trojan (RAT) named Deuterbear, employed by the China-linked hacking group BlackTech. This sophisticated Deuterbear RAT malware is part of a broader cyber espionage operation targeting the Asia-Pacific region throughout the year. Advancements Over Waterbear Deuterbear exhibits notable advancements over […]
The post Deuterbear RAT: China-Linked Hackers’ Cyber Espionage Tool appeared first on TuxCare.
The post Deuterbear RAT: China-Linked Hackers’ Cyber Espionage Tool appeared first on Security Boulevard.


“This is the largest ever operation against botnets, which play a major role in the deployment of ransomware,” Europol said.Botnets are used for different types of cybercrime including ransomware, identity theft, credit card scams, and several other financial crimes. “The dismantled botnets consisted of millions of infected computer systems,” a joint press statement from the Operation Endgame team said. Led by France, Germany, and the Netherlands, and supported by Eurojust, the operation involved countries including Denmark, the United Kingdom, the United States, Armenia, Bulgaria, Lithuania, Portugal, Romania, Switzerland, and Ukraine. Operation Endgame resulted in:
“All of them are now being used to deploy ransomware and are seen as the main threat in the infection chain,” Europol said.[caption id="attachment_72953" align="aligncenter" width="1920"]
 Operation Endgame seizure notice (Credit: Europol)[/caption]
Operation Endgame seizure notice (Credit: Europol)[/caption]
“This is Season 1 of operation Endgame. Stay tuned. It sure will be exciting. Maybe not for everyone though. Some results can be found here, others will come to you in different and unexpected ways,” the authorities said.“Feel free to get in touch, you might need us. Surely, we could both benefit from an openhearted dialogue. You would not be the first one, nor will you be the last. Think about (y)our next move.” Future actions will be announced on the Operation Endgame website, possibly targeting suspects and users, and ensuring accountability. The news of this massive botnet takedown operation comes a day after the announcement of the dismantling of “likely the world’s largest botnet ever” – the 911 S5 botnet. The botnet’s alleged administrator Yunhe Wang, was arrested last week and a subsequent seizure of infrastructure and assets was announced by the FBI. The recent law enforcement actions represent a historic milestone in combating cybercrime, dealing a significant blow to the dropper malware ecosystem that supports ransomware and other malicious activities. The operation's success underscores the importance of international cooperation and the need for robust cybersecurity measures to tackle evolving threats.


“Working with our international partners, the FBI conducted a joint, sequenced cyber operation to dismantle the 911 S5 Botnet—likely the world’s largest botnet ever,” said FBI Director Christopher Wray.“We arrested its administrator, Yunhe Wang, seized infrastructure and assets, and levied sanctions against Wang and his co-conspirators,” Wray added. Wang and two of his associates, along with three Thailand-based businesses linked to the botnet, were sanctioned by the U.S. Treasury Department on Tuesday. Wang faces up to 65 years in prison on charges that include computer fraud, wire fraud, and money laundering.
“Using the dedicated servers, Wang was able to deploy and manage applications, command and control the infected devices, operate his 911 S5 service and provide to paying customers access to the proxied IP addresses associated with the infected devices,” Wang's indictment said.The residential proxy service that Wang developed and operated allowed subscribers to access the more than 19 million compromised IP addresses, which helped them mask their online activities. This service generated approximately $99 million for Wang. The 911 S5 botnet facilitated a range of cybercrimes, including cyberattacks, large-scale fraud, child exploitation, harassment, bomb threats, and export violations, Garland said. One such example is that of customers using the botnet's services for fraudulently filing 560,000 unemployment insurance claims that resulted in a confirmed loss of $5.9 billion from federal pandemic relief programs. In another instance, the 911 S5 botnet customers used the service to file more than 47,000 Economic Injury Disaster Loan applications, which again resulted in the loss of millions of dollars.
“Although approximately 2,525 fraudulent orders valued at $5.5 million were submitted, credit card fraud detection systems and federal investigators were able to thwart the bulk of the attempted purchases, reducing the actual loss to approximately $254,000,“ the Justice Department said.The latest takedown is part of a broader effort of the Justice Department to combat nation-state hacking and international cybercrime. At the beginning of the year, the Justice Department dismantled botnets linked to the China-affiliated hacking group Volt Typhoon, followed by the disruption of botnet controlled by the Russian APT28 group associated with the Russian military intelligence, the GRU. Google-owned cybersecurity firm Mandiant also warned last week that Chinese state hackers are increasingly using vast proxy server networks, built from compromised online devices and virtual private servers, to evade detection during their cyberespionage campaigns. Garland highlighted the global collaboration in this operation, underscoring the Justice Department's commitment to disrupting cybercrime networks that pose a significant threat to individuals and national security. Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.

 'No Defender' Windows Defender bypass[/caption]
The GitHub project, simply called “No Defender,” is billed as “A fun way to disable windows defender + firewall.”
In a note on the project, repository owner “es3n1n” said they essentially reverse-engineered the API that antivirus vendors use to disable Windows Defender.
“There's a WSC (Windows Security Center) service in Windows which is used by antiviruses to let Windows know that there's some other antivirus in the hood and it should disable Windows Defender,” the note states.
“This WSC API is undocumented and furthermore requires people to sign an NDA with Microsoft to get its documentation, so I decided to take an interesting approach for such a thing and used an already existing antivirus called Avast. This AV engine includes a so-called wsc_proxy.exe service, which essentially sets up the WSC API for Avast. With a little bit of reverse engineering, I turned this service into a service that could add my own stuff there.”
One limitation noted by es3n1n is that “to keep this WSC stuff even after reboot, no-defender adds itself (not really itself but rather Avast's module) to the autorun. Thus, you would need to keep the no-defender binaries on your disk.”
'No Defender' Windows Defender bypass[/caption]
The GitHub project, simply called “No Defender,” is billed as “A fun way to disable windows defender + firewall.”
In a note on the project, repository owner “es3n1n” said they essentially reverse-engineered the API that antivirus vendors use to disable Windows Defender.
“There's a WSC (Windows Security Center) service in Windows which is used by antiviruses to let Windows know that there's some other antivirus in the hood and it should disable Windows Defender,” the note states.
“This WSC API is undocumented and furthermore requires people to sign an NDA with Microsoft to get its documentation, so I decided to take an interesting approach for such a thing and used an already existing antivirus called Avast. This AV engine includes a so-called wsc_proxy.exe service, which essentially sets up the WSC API for Avast. With a little bit of reverse engineering, I turned this service into a service that could add my own stuff there.”
One limitation noted by es3n1n is that “to keep this WSC stuff even after reboot, no-defender adds itself (not really itself but rather Avast's module) to the autorun. Thus, you would need to keep the no-defender binaries on your disk.”

 Source: Cyble[/caption]
However, Baphomet later announced that he would be working on a new domain and resuming forum operations. The forum soon returned with regular facilitation of data leak sharing and discussion.
A year later, Baphomet himself faced arrest after a joint operation from law enforcement, which also seized the BreachForums domain and official Telegram channel. The administrator ShinyHunters emerged as the successor, confirming Baphomet's arrest.
However, the domain seizure was short-lived, and was soon redirecting users to a new Telegram channel. An allegedly leaked conversation from an FBI operative to BreachForum's previous domain name registrar and hosting provider NiceNic also appeared to indicate that ShinyHunters had regained control over domain ownership despite its court-ordered seizure.
[caption id="attachment_72579" align="alignnone" width="326"]
Source: Cyble[/caption]
However, Baphomet later announced that he would be working on a new domain and resuming forum operations. The forum soon returned with regular facilitation of data leak sharing and discussion.
A year later, Baphomet himself faced arrest after a joint operation from law enforcement, which also seized the BreachForums domain and official Telegram channel. The administrator ShinyHunters emerged as the successor, confirming Baphomet's arrest.
However, the domain seizure was short-lived, and was soon redirecting users to a new Telegram channel. An allegedly leaked conversation from an FBI operative to BreachForum's previous domain name registrar and hosting provider NiceNic also appeared to indicate that ShinyHunters had regained control over domain ownership despite its court-ordered seizure.
[caption id="attachment_72579" align="alignnone" width="326"] Source: Telegram[/caption]
After a period of dysfunction, BreachForums has now resumed operations, with threat actors already claiming new victims on its forum postings.
Source: Telegram[/caption]
After a period of dysfunction, BreachForums has now resumed operations, with threat actors already claiming new victims on its forum postings.

"The 911 S5 botnet compromised approximately 19 million IP addresses and facilitated the submission of tens of thousands of fraudulent applications related to the Coronavirus Aid, Relief, and Economic Security Act programs by its users, resulting in the loss of billions of dollars to the U.S. government."911 S5 is a residential proxy botnet that allows its paying users, often cybercriminals, to select the IP addresses they can use to connect to the internet using intermediary, internet-connected computers that have been compromised without the computer owners’ knowledge. 911 S5 essentially enables cybercriminals to conceal their originating location, effectively defeating fraud detection systems, the U.S. Treasury explained. The 911 S5 botnet was also implicated in a series of bomb threats made in July 2022, according to the Treasury. Investigators found links of IP addresses within the proxy botnet network being used in this incident. The network was connected to 911 S5, a residential proxy service that allowed users to mask their IP addresses by routing their web activity through compromised devices. The 911 S5 service went offline in July 2022, following a purported hacking incident that damaged essential data. The disruption was reported by independent journalist Brian Krebs. Despite its shutdown, the impacts of its previous operations continued to reverberate, leading to the current sanctions.

 Source: /r/BringMeTheHorizon subreddit[/caption]
The M8 Artificial Reality domain then instructed users to enter a hidden serial code, which fans discovered through the use of several other clues. The site contained unreleased tracks, password-protected files, and various mysteries for fans to uncover.
[caption id="attachment_72432" align="alignnone" width="2800"]
Source: /r/BringMeTheHorizon subreddit[/caption]
The M8 Artificial Reality domain then instructed users to enter a hidden serial code, which fans discovered through the use of several other clues. The site contained unreleased tracks, password-protected files, and various mysteries for fans to uncover.
[caption id="attachment_72432" align="alignnone" width="2800"] Source: multidimensionalnavigator8.help[/caption]
As news of the hidden website spread, fans swiftly set up a dedicated Discord server and collaborated using a Google Doc to unearth all the site’s secrets.
However, their excitement was brief. Hackers soon tried to extract further secrets from the website using unconventional methods, leading developers to temporarily shut down the site and issue a warning to fans.
Source: multidimensionalnavigator8.help[/caption]
As news of the hidden website spread, fans swiftly set up a dedicated Discord server and collaborated using a Google Doc to unearth all the site’s secrets.
However, their excitement was brief. Hackers soon tried to extract further secrets from the website using unconventional methods, leading developers to temporarily shut down the site and issue a warning to fans.
 Source: archive.org[/caption]
[caption id="attachment_72448" align="alignnone" width="276"]
Source: archive.org[/caption]
[caption id="attachment_72448" align="alignnone" width="276"] Source: BringMeTheHorizon ARG Discord[/caption]
The developers appeared to indirectly condemn these attempts through the creative use of the M8 character, without specifying the nature of the intrusion or identifying the perpetrators.
Some fans however, upon receiving the email after their explorations, found the message warnings unexpected for what they believed were legitimate interactions.
The community believed that these selective few hackers ruined the experience for others, with it's discord server noting the downtime in it's FAQ.
0
Source: BringMeTheHorizon ARG Discord[/caption]
The developers appeared to indirectly condemn these attempts through the creative use of the M8 character, without specifying the nature of the intrusion or identifying the perpetrators.
Some fans however, upon receiving the email after their explorations, found the message warnings unexpected for what they believed were legitimate interactions.
The community believed that these selective few hackers ruined the experience for others, with it's discord server noting the downtime in it's FAQ.
0 Bring Me The Horizon's foray into alternate reality gaming showcases the creative potential of digital media in music and album promotion. As fans continue to work together to unravel the remaining mysteries and solve the puzzles within the ARG, it remains to be seen what other surprises await them on the hidden website.
The hacking attempts and the subsequent warnings serves as a reminder that while ARGs can be an engaging and immersive experience, it is essential to respect the developers' intentions and play fair to ensure everyone can enjoy the journey together.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
Bring Me The Horizon's foray into alternate reality gaming showcases the creative potential of digital media in music and album promotion. As fans continue to work together to unravel the remaining mysteries and solve the puzzles within the ARG, it remains to be seen what other surprises await them on the hidden website.
The hacking attempts and the subsequent warnings serves as a reminder that while ARGs can be an engaging and immersive experience, it is essential to respect the developers' intentions and play fair to ensure everyone can enjoy the journey together.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information. 
“Microsoft assesses that Moonstone Sleet’s objective in deploying the ransomware is financial gain, suggesting the actor conducts cyber operations for both intelligence collection and revenue generation.”FakePenny ransomware demands exorbitant ransoms, with recent demands reaching $6.6 million in Bitcoin. “This is in stark contrast to the lower ransom demands of previous North Korea ransomware attacks, like WannaCry 2.0 and H0lyGh0st,” Microsoft said. Notably, the ransom note used by FakePenny ransomware closely resembles the one employed in the infamous NotPetya ransomware attack, which is attributed to the North Korean group Seashell Blizzard. This continuity in tactics highlights the interconnected nature of North Korean cyber operations.
“Despite being new, Moonstone Sleet has demonstrated that it will continue to mature, develop, and evolve, and has positioned itself to be a preeminent threat actor conducting sophisticated attacks on behalf of the North Korean regime.”

 For those seeking guidance or further assistance, Murphy Law Firm can be reached directly via email at abm@murphylegalfirm.com or by phone at (405) 389-4989. Protecting the rights and interests of individuals affected by the TRC Staffing data breach is important, and Murphy Law Firm represents the victims with a legal process.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
For those seeking guidance or further assistance, Murphy Law Firm can be reached directly via email at abm@murphylegalfirm.com or by phone at (405) 389-4989. Protecting the rights and interests of individuals affected by the TRC Staffing data breach is important, and Murphy Law Firm represents the victims with a legal process.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information. 

"A first task of the Safety and Security Committee will be to evaluate and further develop OpenAI’s processes and safeguards over the next 90 days."The committee's initial task is to evaluate and further develop OpenAI’s existing processes and safeguards. They are expected to make recommendations to the board within 90 days. OpenAI has committed to publicly releasing the recommendations it adopts in a manner that aligns with safety and security considerations. The establishment of the safety and security committee is a significant step by OpenAI to address concerns about AI safety and maintain its leadership in AI innovation. By integrating a diverse group of experts and stakeholders into the decision-making process, OpenAI aims to ensure that safety and security remain paramount as it continues to develop cutting-edge AI technologies.

 Anatsa Banking Trojan Attack Chain (Source: Zscaler)[/caption]
The Anatsa banking trojan is increasing in prevalence and infiltrates the Google Play store disguised as benign applications. Using advanced techniques such as overlay and accessibility, it stealthily exfiltrates sensitive banking credentials and financial data. By injecting malicious payloads and employing deceptive login pages, Anatsa poses a significant threat to mobile banking security.
Anatsa Banking Trojan Attack Chain (Source: Zscaler)[/caption]
The Anatsa banking trojan is increasing in prevalence and infiltrates the Google Play store disguised as benign applications. Using advanced techniques such as overlay and accessibility, it stealthily exfiltrates sensitive banking credentials and financial data. By injecting malicious payloads and employing deceptive login pages, Anatsa poses a significant threat to mobile banking security.

Source: securityboulevard.com – Author: Wajahat Raja Recent reports claim that the Microsoft Threat Intelligence team stated that a cybercriminal group, identified as Storm-1811, has been exploiting Microsoft’s Quick Assist tool in a series of social engineering attacks. This group is known for deploying the Black Basta ransomware attack. On May 15, 2024, Microsoft released details […]
La entrada Black Basta Ransomware Attack: Microsoft Quick Assist Flaw – Source: securityboulevard.com se publicó primero en CISO2CISO.COM & CYBER SECURITY GROUP.



 Source: Shutterstock (MEP Anna-Michelle Asimakopoulou)[/caption]
On receiving the unsolicited emails to their private accounts, several Greek diaspora voters living abroad expressed their surprise on social media and accused the New Democracy MEP of violating the European Union’s General Data Protection Regulation (GDPR). The expats questioned how the addresses were obtained by the MEP for use in the email campaigns.
Asimakopoulou earlier attempted to refute allegations of violating these data protection laws but was found to provide contradictory explanations regarding the source from which these addresses were obtained for usage in the mass email campaign.
As a result, the Ministry of Interior faces a 400,000-euro fine, while Asimakopoulou faces a 40,000-euro fine. The authority also postponed its verdict on Theodoropoulos and the New Democracy party to examine new claims related to the investigation.
The PDPA stated in its investigation that the use of the emails, “was in violation of the basic principle of legality, objectivity and transparency of processing, as it was in violation of a series of provisions of the electoral legislation and furthermore could not reasonably be expected.”
The ministry said it will "thoroughly study" the authority's decision to consider further legal actions. The "email-gate" scandal has led to significant consequences, including the resignation of the general secretary of the Interior Ministry, Michalis Stavrianoudakis, and the dismissal of Theodoropoulos by New Democracy.
Asimakopoulou has announced she will not run in the European Parliament elections. Asimakopoulou is also facing 75 lawsuits by citizens and over 200 lawsuits from the Interior Ministry, over the scandal.
Source: Shutterstock (MEP Anna-Michelle Asimakopoulou)[/caption]
On receiving the unsolicited emails to their private accounts, several Greek diaspora voters living abroad expressed their surprise on social media and accused the New Democracy MEP of violating the European Union’s General Data Protection Regulation (GDPR). The expats questioned how the addresses were obtained by the MEP for use in the email campaigns.
Asimakopoulou earlier attempted to refute allegations of violating these data protection laws but was found to provide contradictory explanations regarding the source from which these addresses were obtained for usage in the mass email campaign.
As a result, the Ministry of Interior faces a 400,000-euro fine, while Asimakopoulou faces a 40,000-euro fine. The authority also postponed its verdict on Theodoropoulos and the New Democracy party to examine new claims related to the investigation.
The PDPA stated in its investigation that the use of the emails, “was in violation of the basic principle of legality, objectivity and transparency of processing, as it was in violation of a series of provisions of the electoral legislation and furthermore could not reasonably be expected.”
The ministry said it will "thoroughly study" the authority's decision to consider further legal actions. The "email-gate" scandal has led to significant consequences, including the resignation of the general secretary of the Interior Ministry, Michalis Stavrianoudakis, and the dismissal of Theodoropoulos by New Democracy.
Asimakopoulou has announced she will not run in the European Parliament elections. Asimakopoulou is also facing 75 lawsuits by citizens and over 200 lawsuits from the Interior Ministry, over the scandal.
 Source: Shuttertock (Interior Minister Niki Kerameos)[/caption]
The main opposition party SYRIZA released a statement asserting that “private data were being passed around for months among the Interior Ministry, ND, and at least one election candidate,” questioning whether the email list had been leaked to other New Democracy candidates by the Interior Ministry.
While the Interior Minister might not have been directly involved, SYRIZA claimed that “Kerameos did not have the guts to show up at the Committee on Institutions and Transparency.” The Socialist PASOK Party also demanded Kerameos’ resignation, adding that the violation demonstrates the government as “incapable of fulfilling the self-evident, as proven by the high fines.”
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
Source: Shuttertock (Interior Minister Niki Kerameos)[/caption]
The main opposition party SYRIZA released a statement asserting that “private data were being passed around for months among the Interior Ministry, ND, and at least one election candidate,” questioning whether the email list had been leaked to other New Democracy candidates by the Interior Ministry.
While the Interior Minister might not have been directly involved, SYRIZA claimed that “Kerameos did not have the guts to show up at the Committee on Institutions and Transparency.” The Socialist PASOK Party also demanded Kerameos’ resignation, adding that the violation demonstrates the government as “incapable of fulfilling the self-evident, as proven by the high fines.”
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information. Recent reports claim that the Microsoft Threat Intelligence team stated that a cybercriminal group, identified as Storm-1811, has been exploiting Microsoft’s Quick Assist tool in a series of social engineering attacks. This group is known for deploying the Black Basta ransomware attack. On May 15, 2024, Microsoft released details about how this financially motivated group […]
The post Black Basta Ransomware Attack: Microsoft Quick Assist Flaw appeared first on TuxCare.
The post Black Basta Ransomware Attack: Microsoft Quick Assist Flaw appeared first on Security Boulevard.

 Source: ONEKEY[/caption]
After collaborative efforts and validation processes, TP-Link shared a beta version of 1.1.7p1 on April 10 for further testing, culminating in the confirmation and release of the patch by ONEKEY on May 27, 2024.
The vulnerability exposed a critical flaw in the TP-Link Archer C5400X gaming router, rendering it susceptible to remote command execution. This exploit granted unauthorized users the ability to execute arbitrary commands on the device, posing security risks to users' data and network integrity.
“It seems the need to provide a wireless device configuration API at TP-Link had to be answered either fast or cheap, which ended up with them exposing a supposedly limited shell over the network that clients within the router could use as a way to configure wireless devices”, said OneKey in the advisory.
Source: ONEKEY[/caption]
After collaborative efforts and validation processes, TP-Link shared a beta version of 1.1.7p1 on April 10 for further testing, culminating in the confirmation and release of the patch by ONEKEY on May 27, 2024.
The vulnerability exposed a critical flaw in the TP-Link Archer C5400X gaming router, rendering it susceptible to remote command execution. This exploit granted unauthorized users the ability to execute arbitrary commands on the device, posing security risks to users' data and network integrity.
“It seems the need to provide a wireless device configuration API at TP-Link had to be answered either fast or cheap, which ended up with them exposing a supposedly limited shell over the network that clients within the router could use as a way to configure wireless devices”, said OneKey in the advisory.
 Source: TP-Link[/caption]
Central to this TP-Link Archer C5400X vulnerability is the rftest binary, launched during the device's initialization sequence. This binary, responsible for wireless interface self-assessment, inadvertently exposes a network service vulnerable to unauthenticated command injection. Attackers can leverage this vulnerability to remotely execute commands with elevated privileges, potentially compromising the device and its connected network.
To mitigate the risk posed by this vulnerability, users are strongly advised to upgrade their devices to version 1_1.1.7. TP-Link has implemented fixes to prevent command injection through shell meta-characters, thereby enhancing the security posture of affected devices. However, users must remain vigilant and proactive in ensuring their devices are up to date with the latest firmware releases to safeguard against emerging threats.
Source: TP-Link[/caption]
Central to this TP-Link Archer C5400X vulnerability is the rftest binary, launched during the device's initialization sequence. This binary, responsible for wireless interface self-assessment, inadvertently exposes a network service vulnerable to unauthenticated command injection. Attackers can leverage this vulnerability to remotely execute commands with elevated privileges, potentially compromising the device and its connected network.
To mitigate the risk posed by this vulnerability, users are strongly advised to upgrade their devices to version 1_1.1.7. TP-Link has implemented fixes to prevent command injection through shell meta-characters, thereby enhancing the security posture of affected devices. However, users must remain vigilant and proactive in ensuring their devices are up to date with the latest firmware releases to safeguard against emerging threats.
In recent cybersecurity news, Google has swiftly addressed a critical security concern by releasing an emergency update for its Chrome browser. This update targets the third zero-day vulnerability detected in less than a week. Let’s have a look at the details of this Google Chrome zero-day patch and understand its implications for user safety. […]
The post Alert: Google Chrome Zero-Day Patch Fixes Critical Flaw appeared first on TuxCare.
The post Alert: Google Chrome Zero-Day Patch Fixes Critical Flaw appeared first on Security Boulevard.

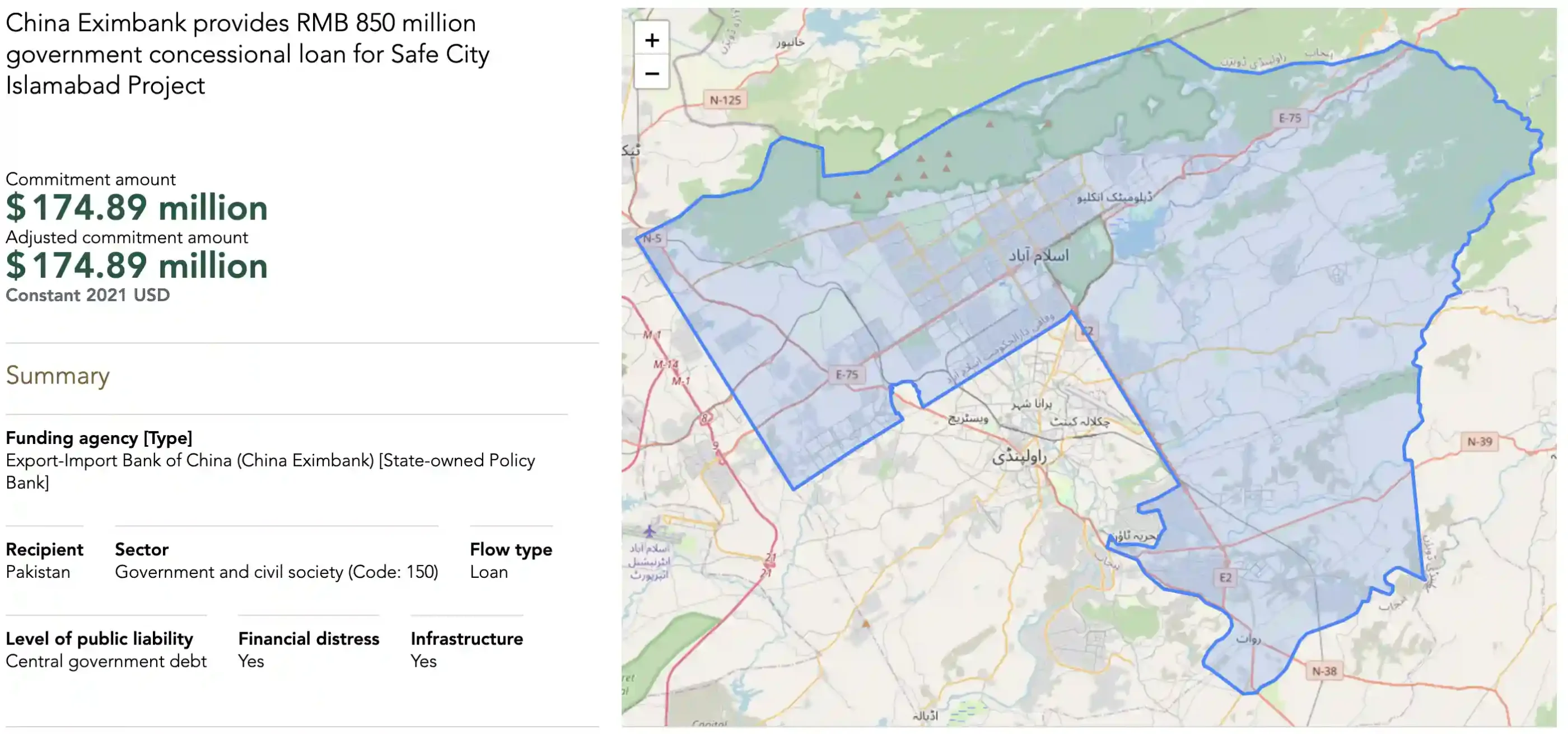 Source: china.aiddata.org[/caption]
The compromise of these systems impacted several critical services tied to the Safe City initiative. This includes mobile applications, smart police vehicle records, police station data, video analytics, Islamabad Traffic Police, e-challan systems, and records from the operations division. Approximately 13 to 15 servers provided by the police facilitation center F-6 were also affected.
An officer highlighted to Dawn, Pakistan's largest English newspaper, that this incident was not a typical hacking scenario involving stolen login credentials. Instead, the system's vulnerability stemmed from the use of simple and common login IDs and passwords by officials, making it easier for hackers to gain access. Additionally, many of the software and applications were found to be outdated or with expired licenses, further compromising the system's security.
Despite the breach of several systems, the Safe City cameras' management system that operated independently through offline direct lines, remained secure, demonstrating the effectiveness of isolated systems in safeguarding against such attacks.
Police spokesperson Taqi Jawad confirmed the intrusion as an attempted breach that triggered the firewall's alarm but stated that appropriate precautionary measures had been taken. "All logins have been closed for the past two days to change them, including those of police stations and officers at various ranks," he stated.
Jawad refrained from sharing further specifics on the server shutdowns as he stated they were still pending technical feedback
Source: china.aiddata.org[/caption]
The compromise of these systems impacted several critical services tied to the Safe City initiative. This includes mobile applications, smart police vehicle records, police station data, video analytics, Islamabad Traffic Police, e-challan systems, and records from the operations division. Approximately 13 to 15 servers provided by the police facilitation center F-6 were also affected.
An officer highlighted to Dawn, Pakistan's largest English newspaper, that this incident was not a typical hacking scenario involving stolen login credentials. Instead, the system's vulnerability stemmed from the use of simple and common login IDs and passwords by officials, making it easier for hackers to gain access. Additionally, many of the software and applications were found to be outdated or with expired licenses, further compromising the system's security.
Despite the breach of several systems, the Safe City cameras' management system that operated independently through offline direct lines, remained secure, demonstrating the effectiveness of isolated systems in safeguarding against such attacks.
Police spokesperson Taqi Jawad confirmed the intrusion as an attempted breach that triggered the firewall's alarm but stated that appropriate precautionary measures had been taken. "All logins have been closed for the past two days to change them, including those of police stations and officers at various ranks," he stated.
Jawad refrained from sharing further specifics on the server shutdowns as he stated they were still pending technical feedback

 Source: www.optus.com.au/support/cyberresponse[/caption]
The company commissioned an independent external forensic review of the cyberattack from Deloitte over its security systems, controls and processes under the advise of the then CEO Kelly Bayer Rosmarin and the approval of its board. Bayer made the following statement over the decision:
Source: www.optus.com.au/support/cyberresponse[/caption]
The company commissioned an independent external forensic review of the cyberattack from Deloitte over its security systems, controls and processes under the advise of the then CEO Kelly Bayer Rosmarin and the approval of its board. Bayer made the following statement over the decision:
“This review will help ensure we understand how it occurred and how we can prevent it from occurring again. It will help inform the response to the incident for Optus. This may also help others in the private and public sector where sensitive data is held and risk of cyberattack exists.Kelly, later resigned over the incident with Optus now being led by a new CEO, who is working to rebuild trust with customers in a 'challenging' market. Despite the efforts of the company to deal with the data breach, the recent court decision comes after Optus appealed an earlier ruling that it must hand over the report to Slater & Gordon, the law firm pursuing a class action against the company for allegedly failing to protect its customers' personal information. Optus has not yet made a public statement regarding the Federal Court's decision. However, the company had previously argued that the Deloitte report was commissioned to provide legal advice and therefore it was privileged. The court, however, decided that Optus had failed to prove that the dominant purpose of the report was for legal advice.
a domestic violence victim who spent money that was intended for counselling for her children on increasing security measures around the house, including installing video cameras and extra locks on doors and windows
a former Optus customer who had previously been burgled and had his identity stolen who now suffers severe anxiety after learning his personal information had been shared online
a stalking victim who takes extreme measure to maintain her privacy, especially her address, who fears her life has genuinely been put in danger by the data breach
a woman who is now too fearful to answer the telephone after noticing an increase in scam phone calls following the Optus cyberattack, and
a retired police officer concerned that his home address may have been shared with criminals he was involved in the prosecution and incarceration of.

 (L-R: Beenu Arora, Co-Founder and CEO, Cyble Inc., Thomas Heuckeroth, SVP IT Infrastructure & Digital Platforms, Emirates Group and Jo Mikleus, Senior Vice President, Cyble Inc.)[/caption]
(L-R: Beenu Arora, Co-Founder and CEO, Cyble Inc., Thomas Heuckeroth, SVP IT Infrastructure & Digital Platforms, Emirates Group and Jo Mikleus, Senior Vice President, Cyble Inc.)[/caption]







 Source: Bitdefender[/caption]
The integration of Bitdefender’s Scamio with WhatsApp was a strategic response to the increasing use of artificial intelligence by malicious actors. Scammers were exploiting popular messaging apps and online services to steal money, credentials, and personal data. By integrating Scamio into WhatsApp, Bitdefender aimed to disrupt these criminal activities by offering a sophisticated tool capable of keeping pace with online scam tactics.
The enhanced accessibility provided by this feature aimed to provide an additional layer of security for Australians, who were disproportionately targeted by online fraudsters. Having Scamio available within WhatsApp streamlined the scam verification process for everyday users, reducing the time and effort required to identify potential scams.
Source: Bitdefender[/caption]
The integration of Bitdefender’s Scamio with WhatsApp was a strategic response to the increasing use of artificial intelligence by malicious actors. Scammers were exploiting popular messaging apps and online services to steal money, credentials, and personal data. By integrating Scamio into WhatsApp, Bitdefender aimed to disrupt these criminal activities by offering a sophisticated tool capable of keeping pace with online scam tactics.
The enhanced accessibility provided by this feature aimed to provide an additional layer of security for Australians, who were disproportionately targeted by online fraudsters. Having Scamio available within WhatsApp streamlined the scam verification process for everyday users, reducing the time and effort required to identify potential scams.
One of the most critical yet often overlooked aspects of cybersecurity is the timely patching of vulnerabilities. While much attention is given to sophisticated phishing attacks and the menace of password brute-forcing, the importance of addressing unpatched vulnerabilities cannot be overstated. These vulnerabilities represent low-hanging fruit for cybercriminals, offering a relatively straightforward path into systems. […]
The post The Importance of Patching Vulnerabilities in Cybersecurity appeared first on TuxCare.
The post The Importance of Patching Vulnerabilities in Cybersecurity appeared first on Security Boulevard.



“Recruitment suffers because cyber operations are not a top priority for any of the services, and incentives for new recruits vary wildly. The services do not coordinate to ensure that trainees acquire a consistent set of skills or that their skills correspond to the roles they will ultimately fulfill at CYBERCOM.”Promotion systems often hold back skilled cyber personnel because the systems were designed to evaluate service members who operate on land, at sea, or in the air, not in cyberspace. Retention rates for qualified personnel are low because of inconsistent policies, institutional cultures that do not value cyber expertise, and insufficient opportunities for advanced training. “Resolving these issues requires the creation of a new independent armed service – a U.S. Cyber Force – alongside the Army, Navy, Air Force, Marine Corps, and Space Force.” The FDD report concluded, “America’s cyber force generation system is clearly broken. Fixing it demands nothing less than the establishment of an independent cyber service.”

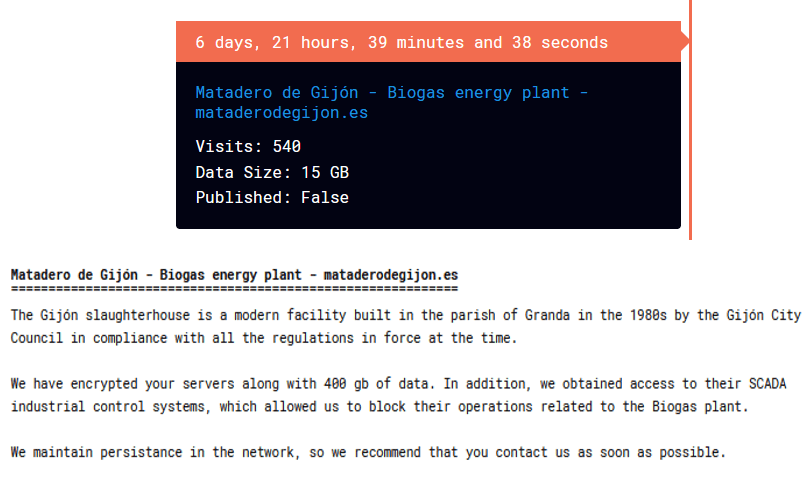 Ransomhub posts on their DLS.(Source: Cyble)[/caption]
The origins of Ransomhub trace back to February 2024 when it emerged as a Ransomware-as-a-Service (RaaS) on cybercrime forums. Employing sophisticated encryption techniques and targeting organizations predominantly in the IT & ITES sector, particularly in the United States, Ransomhub quickly garnered notoriety within the underground cyber community.
[caption id="attachment_69994" align="alignnone" width="728"]
Ransomhub posts on their DLS.(Source: Cyble)[/caption]
The origins of Ransomhub trace back to February 2024 when it emerged as a Ransomware-as-a-Service (RaaS) on cybercrime forums. Employing sophisticated encryption techniques and targeting organizations predominantly in the IT & ITES sector, particularly in the United States, Ransomhub quickly garnered notoriety within the underground cyber community.
[caption id="attachment_69994" align="alignnone" width="728"]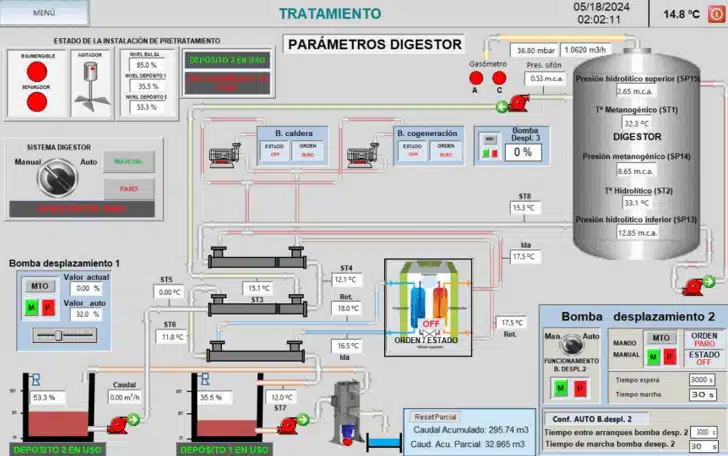 Alleged SCADA control of Gijón Bio-Energy Plant Digestor Tank (Source: Cyble)[/caption]
The group's aggressive recruitment of affiliates, coupled with attempts to exploit vulnerabilities in SCADA systems, signify a strategic shift towards targeting Operational Technology (OT) environments. This shift aligns with broader trends in the ransomware landscape, wherein malicious actors seek to exploit weaknesses in interconnected systems for maximum impact.
CRIL's investigation into Ransomhub's activities reveals a concerning association with Initial Access Brokers (IABs) on Russian-language forums, indicating a sophisticated network for procuring compromised access to victims' networks. Such alliances highligh the need for heightened vigilance and proactive defense mechanisms to thwart potential breaches.
Alleged SCADA control of Gijón Bio-Energy Plant Digestor Tank (Source: Cyble)[/caption]
The group's aggressive recruitment of affiliates, coupled with attempts to exploit vulnerabilities in SCADA systems, signify a strategic shift towards targeting Operational Technology (OT) environments. This shift aligns with broader trends in the ransomware landscape, wherein malicious actors seek to exploit weaknesses in interconnected systems for maximum impact.
CRIL's investigation into Ransomhub's activities reveals a concerning association with Initial Access Brokers (IABs) on Russian-language forums, indicating a sophisticated network for procuring compromised access to victims' networks. Such alliances highligh the need for heightened vigilance and proactive defense mechanisms to thwart potential breaches.