A new paper gives an insider’s perspective into CISA’s Known Exploited Vulnerability catalog – and also offers a free tool to help security teams use the CISA KEV catalog more effectively.
The
paper, by former CISA KEV Section Chief and current runZero VP of Security Research Tod Beardsley, applies commonly used enrichment signals like CVSS, EPSS and SSVC, public exploit tooling from Metasploit and Nuclei, MITRE ATT&CK mappings, and “time-sequenced relationships” to help security teams prioritize vulnerabilities based on urgency.
The paper’s findings led to the development of
KEV Collider, a web application and dataset “that encourages readers to explore, recombine, and validate KEV enrichment data to better leverage the KEV in their daily operations,” the paper said.
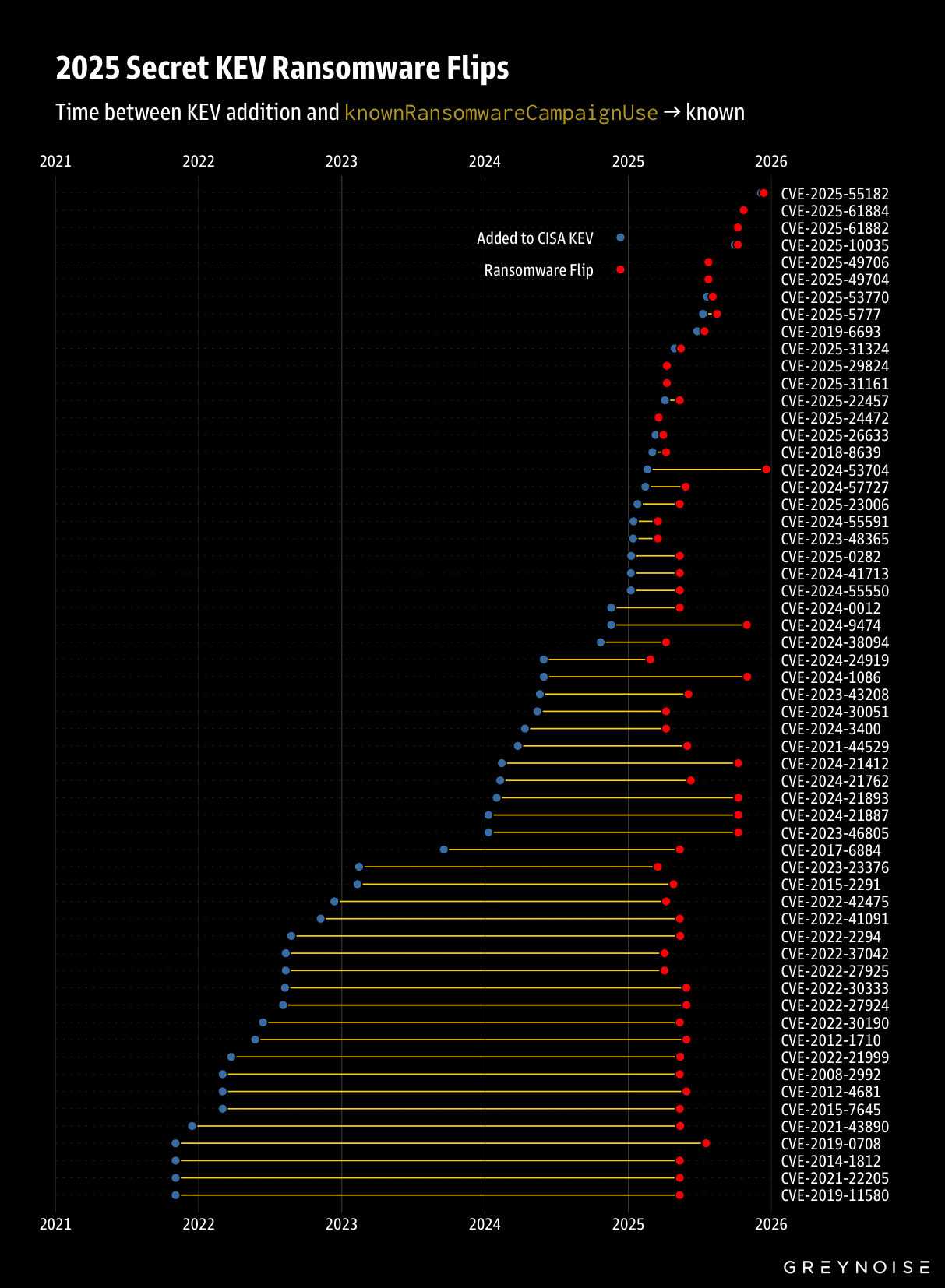
One interesting finding in the paper is that only 32% of CISA KEV
vulnerabilities are “immediately exploitable for initial access.”
CISA KEV Is Not a List of the Worst Vulnerabilities
CISA KEV is not a list of the worst vulnerabilities, and the criteria for inclusion in the KEV catalog is perhaps surprisingly narrow.
“The KEV is often misunderstood as a government-curated list of the most severe vulnerabilities ever discovered, or as a catalog of hyper-critical remote code execution flaws actively being used by foreign adversaries against U.S. government systems,” the paper said. “This casual interpretation is incorrect on several counts. While KEV-listed vulnerabilities do represent confirmed exploitation, the catalog exists primarily as an operational prioritization tool rather than as a comprehensive inventory of exploited vulnerabilities.”
Inclusion in the KEV Catalog is limited to vulnerabilities that meet four conditions:
- The vulnerability must have an assigned Common Vulnerabilities and Exposures (CVE) identifier.
- There must be a reasonable mitigation. “This means that vulnerabilities with no realistic path to mitigation will not reach the KEV,” the paper said. The lack of a straightforward fix has kept CVE-2022-21894, aka “BlackLotus,” off the list even though the NSA has provided mitigation guidance.
- There must be evidence of exploitation. “This exploitation must be observed by CISA, either directly or through trusted reporting channels,” the paper said.
- The vulnerability must be relevant to the U.S. Federal Civilian Executive Branch (FCEB).
CISA KEV is not the only list of known exploited vulnerabilities, the paper said. Another is the
VulnCheck KEV, which is three times bigger than CISA KEV. “It often adds vulnerabilities to its KEV in closer-to-real-time as exploitation evidence surfaces, sometimes beating the CISA KEV as first to publish exploitation notifications,” the paper said – and would also be an interesting place to apply the paper’s criteria.
CISA KEV isn’t a list of the most severe vulnerabilities: “the vulnerabilities there are not all unauthenticated, remotely exploitable, initial intrusion vulnerabilities,” the paper said.
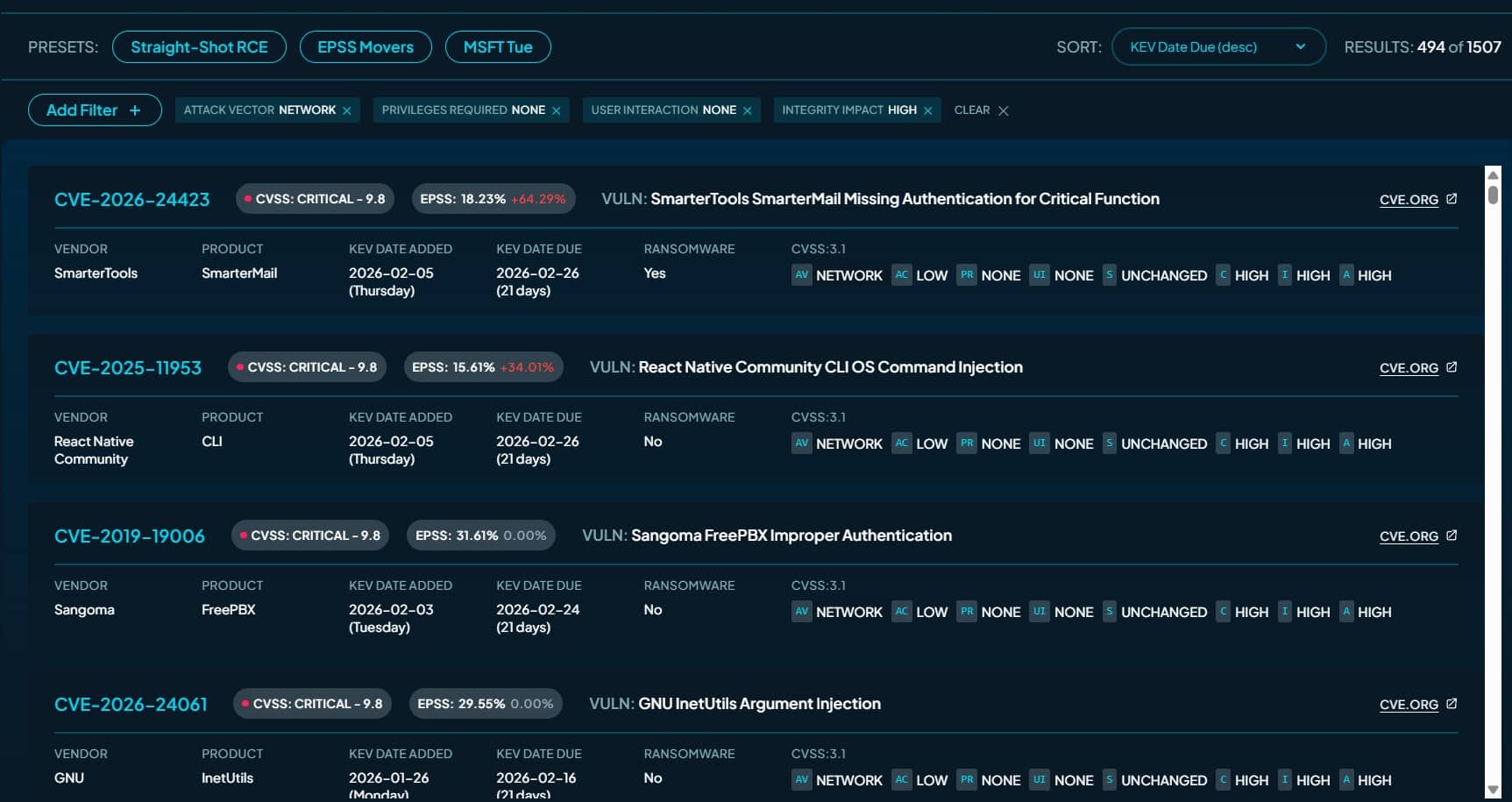
Looking at just the last 12 vulnerabilities added to the KEV catalog in December, only four met the criteria for a “straight shot RCE bug.” Those criteria are:
- Access Vector of “Network” (as opposed to “Adjacent,” “Local,” or “Physical”)
- Privileges Required of “None” (as opposed to “Low” or “High”)
- User Interaction of “None” (as opposed to “Required”)
- Integrity Impact of “High” (as opposed to “None” or “Low”)
“These are the vulnerabilities that listen on an
internet socket, don’t require a login, don’t require the victim to act, and the attacker ends up with total control over the affected system,” the paper said.
Interestingly, the four straight-shot RCE vulnerabilities are all rated Critical, while the rest are rated High or Medium.
Out of 1,488 KEV vulnerabilities as of January 14, 2026, only 483, or 32%, “are useful for immediate initial access,” the paper said. Using the
Straight-Shot RCE filter in KEV Collider, 494 of 1,507 KEV vulnerabilities in the catalog as of Feb. 6 qualify, or 32.7
Looking at EPSS scores suggests that some of the vulnerabilities have a low probability of being exploited again in the future. There are 545 KEV vulnerabilities with very high EPSS scores – and 353 in the sub-10% category.
Examining Metasploit Framework exploits, 464 KEV vulnerabilities were associated with at least one Metasploit module. “This means that just about a third of all KEVs are trivially exploitable today, as Metasploit modules are free, easy to use, and well-understood by attackers and defenders alike,” the paper said.
There were 398
Nuclei templates “suitable for testing KEV vulnerabilities,” and 235 vulnerabilities with both Metasploit and Nuclei exploits.
The paper also looked at the correlation of MITRE ATT&CK mappings with Metasploit and Nuclei
exploit development and found that vulnerabilities associated with T1190 (Exploit Public-Facing Application) and T1059 (Command and Scripting Interpreter) “are more likely to attract the attention of public exploit developers.”
Also read: CISA Silently Updates Vulnerabilities Exploited by Ransomware Groups
Perfect Vulnerability Coverage ‘Unrealistic’
The paper noted that “perfect vulnerability coverage is an increasingly unrealistic goal, particularly when organizations are constrained by finite tooling, staffing, or budget. This is even true when the focus is narrowed to merely the CISA KEV catalog.”
“Many KEVs now affect assets that are difficult to inventory, difficult to scan, or difficult to patch using conventional enterprise tooling,” and can’t be covered by a single product.
The paper’s goal is to help
security practitioners “reason about uncertainty and prioritize effort when full coverage is unattainable. In practice, organizations must decide how to sequence remediation, where to apply detection and monitoring first, and when to escalate resource allocation to meet particularly aggressive deadlines.”
All source JSON files used by the KEV Collider application are available in a public
GitHub repository.