Researchers have found another method used in the spirit of ClickFix: CrashFix.
ClickFix campaigns use convincing lures—historically “Human Verification” screens—to trick the user into pasting a command from the clipboard. After fake Windows update screens, video tutorials for Mac users, and many other variants, attackers have now introduced a browser extension that crashes your browser on purpose.
Researchers found a rip-off of a well-known ad blocker and managed to get it into the official Chrome Web Store under the name “NexShield – Advanced Web Protection.” Strictly speaking, crashing the browser does provide some level of protection, but it’s not what users are typically looking for.
If users install the browser extension, it phones home to nexsnield[.]com (note the misspelling) to track installs, updates, and uninstalls. The extension uses Chrome’s built-in Alarms API (application programming interface) to wait 60 minutes before starting its malicious behavior. This delay makes it less likely that users will immediately connect the dots between the installation and the following crash.
After that pause, the extension starts a denial-of-service loop that repeatedly opens chrome.runtime port connections, exhausting the device’s resources until the browser becomes unresponsive and crashes.
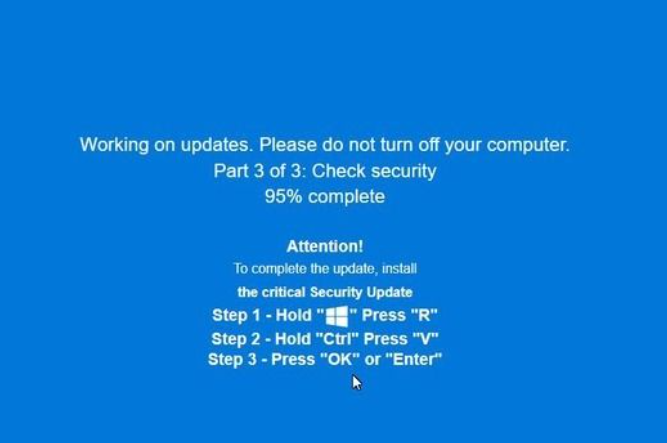
After restarting the browser, users see a pop-up telling them the browser stopped abnormally—which is true but not unexpected— and offering instructions on how to prevent it from happening in the future.
It presents the user with the now classic instructions to open Win+R, press Ctrl+V, and hit Enter to “fix” the problem. This is the typical ClickFix behavior. The extension has already placed a malicious PowerShell or cmd command on the clipboard. By following the instructions, the user executes that malicious command and effetively infects their own computer.
Based on fingerprinting checks to see whether the device is domain-joined, there are currently two possible outcomes.
If the machine is joined to a domain, it is treated as a corporate device and infected with a Python remote access trojan (RAT) dubbed ModeloRAT. On non-domain-joined machines, the payload is currently unknown as the researchers received only a “TEST PAYLOAD!!!!” response. This could imply ongoing development or other fingerprinting which made the test machine unsuitable.
How to stay safe
The extension was no longer available in the Chrome Web Store at the time of writing, but it will undoubtedly resurface with an other name. So here are a few tips to stay safe:
- If you’re looking for an ad blocker or other useful browser extensions, make sure you are installing the real deal. Cybercriminals love to impersonate trusted software.
- Never run code or commands copied from websites, emails, or messages unless you trust the source and understand the action’s purpose. Verify instructions independently. If a website tells you to execute a command or perform a technical action, check through official documentation or contact support before proceeding.
- Secure your devices. Use an up-to-date real-time anti-malware solution with a web protection component.
- Educate yourself on evolving attack techniques. Understanding that attacks may come from unexpected vectors and evolve helps maintain vigilance. Keep reading our blog!
Pro tip: the free Malwarebytes Browser Guard extension is a very effective ad blocker and protects you from malicious websites. It also warns you when a website copies something to your clipboard and adds a small snippet to render any commands useless.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.