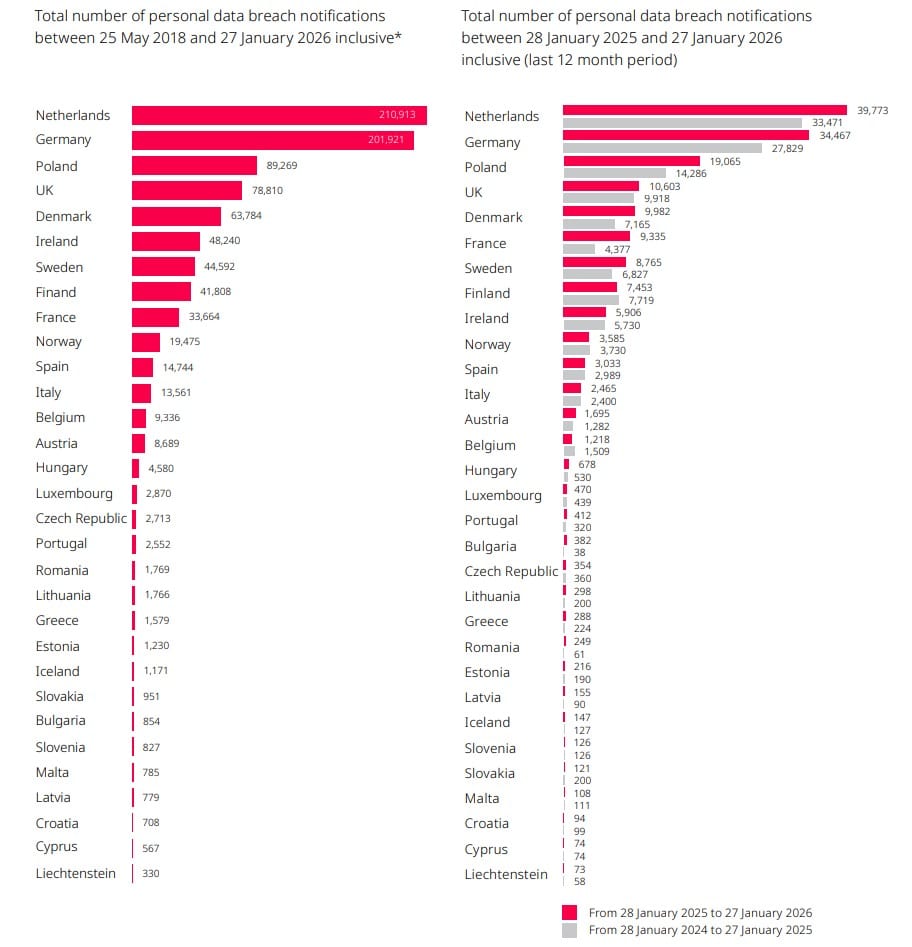
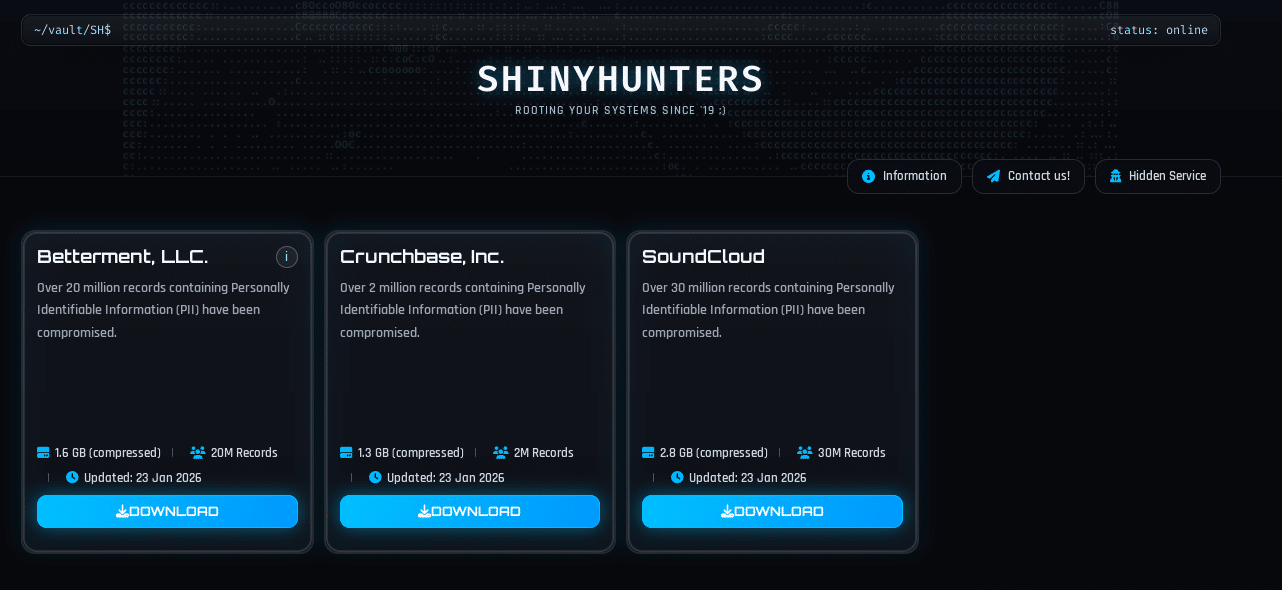
The Cyber Express Weekly Roundup: Escalating Breaches, Regulatory Crackdowns, and Global Cybercrime Developments




 Image Source: X[/caption]
Image Source: X[/caption]





Data accessed in October 2025 went undetected until February, affecting subscribers across the newsletter platform with no evidence of misuse yet identified.
Substack disclosed a security breach that exposed user email addresses, phone numbers and internal metadata to unauthorized third parties, revealing the incident occurred four months before the company detected the compromise. CEO Chris Best notified users Tuesday that attackers accessed the data in October 2025, though Substack only identified evidence of the breach on February 3.
"I'm incredibly sorry this happened. We take our responsibility to protect your data and your privacy seriously, and we came up short here," Best wrote in the notification sent to affected users.

The breach allowed an unauthorized third party to access limited user data without permission through a vulnerability in Substack's systems. The company confirmed that credit card numbers, passwords and financial information were not accessed during the incident, limiting exposure to contact information and unspecified internal metadata.
The four-month detection gap raises questions about Substack's security monitoring capabilities and incident response procedures. Modern security frameworks typically emphasize rapid threat detection, with leading organizations aiming to identify breaches within days or hours rather than months. The extended dwell time—the period attackers maintained access before detection—gave threat actors ample opportunity to exfiltrate data undetected.
Substack claims it has fixed the vulnerability that enabled the breach but provided no technical details about the nature of the flaw or how attackers exploited it. The company stated it is conducting a full investigation and taking steps to improve systems and processes to prevent future incidents.
Best urged users to exercise caution with emails or text messages they receive, warning that exposed contact information could enable phishing attacks or social engineering campaigns. While Substack claims no evidence of data misuse exists, the four-month gap between compromise and detection means attackers had significant time to leverage stolen information.
The notification's vague language about "other internal metadata" leaves users uncertain about the full scope of exposed information. Internal metadata could include account creation dates, IP addresses, subscription lists, payment history or other details that, when combined with email addresses and phone numbers, create comprehensive user profiles valuable to attackers.
Newsletter platforms like Substack represent attractive targets for threat actors because they aggregate contact information for engaged audiences across diverse topics. Compromised email lists enable targeted phishing campaigns, while phone numbers facilitate smishing attacks—phishing via text message—that many users find less suspicious than email-based attempts.
The breach affects Substack's reputation as the platform competes for writers and subscribers against established players and emerging alternatives. Trust forms the foundation of newsletter platforms, where creators depend on reliable infrastructure to maintain relationships with paying subscribers.
Substack has not disclosed how many users were affected, whether the company will offer identity protection services, or if it has notified law enforcement about the breach. The company also has not confirmed whether it will face regulatory scrutiny under data protection laws in jurisdictions where affected users reside.
Users should remain vigilant for suspicious communications, enable two-factor authentication where available, and monitor accounts for unauthorized activity following the disclosure.


“Our priority response to this event is protecting the information entrusted to us and maintaining continuity of critical public health services. By taking a proactive approach and engaging specialized expertise, we are working diligently to restore systems and keep our community informed.”The organization serves Peterborough city and county, Northumberland and Haliburton counties, Kawartha Lakes, and the First Nations communities of Curve Lake and Alderville. The cyberattack prompted a review of all systems that could potentially be affected, ensuring that any vulnerabilities are mitigated.
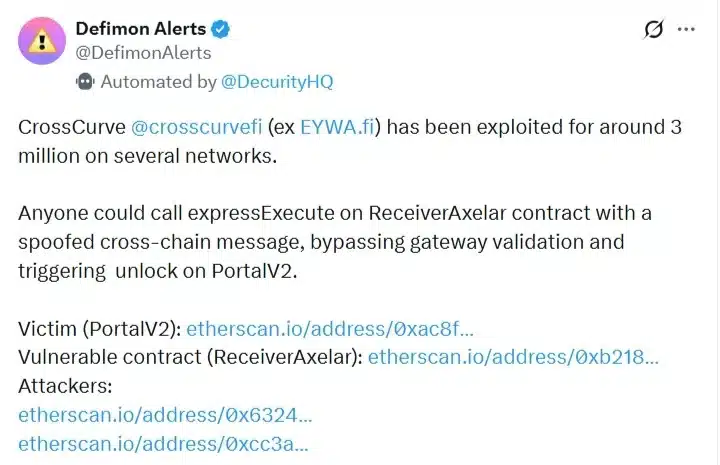 CrossCurve Exploit Details (Source: Defimon Alerts on X)[/caption]
By exploiting this flaw, attackers were able to bypass the intended gateway validation logic and trigger unauthorized token unlocks on the protocol’s PortalV2 contract. As a result, funds were drained without proper authorization. The exploit impacted the CrossCurve bridge across multiple networks, highlighting the risks associated with cross-chain messaging systems.
Data from Arkham Intelligence, shared by Defimon Alerts, shows that the PortalV2 contract’s balance dropped from roughly $3 million to nearly zero around January 31. Transaction data indicates that the exploit unfolded across several chains, rather than being confined to a single network.
CrossCurve Exploit Details (Source: Defimon Alerts on X)[/caption]
By exploiting this flaw, attackers were able to bypass the intended gateway validation logic and trigger unauthorized token unlocks on the protocol’s PortalV2 contract. As a result, funds were drained without proper authorization. The exploit impacted the CrossCurve bridge across multiple networks, highlighting the risks associated with cross-chain messaging systems.
Data from Arkham Intelligence, shared by Defimon Alerts, shows that the PortalV2 contract’s balance dropped from roughly $3 million to nearly zero around January 31. Transaction data indicates that the exploit unfolded across several chains, rather than being confined to a single network.






 Artificial intelligence further reshaped attacker operations. Cyble observed AI-assisted automation being embedded into multiple stages of the kill chain. Negotiation workflows were partially automated. Malware became more polymorphic. Intrusion paths were adapted in real time as defenses responded. These developments increased attack velocity while compressing dwell time, forcing defenders to operate with narrower margins for response.
Artificial intelligence further reshaped attacker operations. Cyble observed AI-assisted automation being embedded into multiple stages of the kill chain. Negotiation workflows were partially automated. Malware became more polymorphic. Intrusion paths were adapted in real time as defenses responded. These developments increased attack velocity while compressing dwell time, forcing defenders to operate with narrower margins for response.
 sectors and regions targeted by threat actors in 2025 (Source: Cyble)[/caption]
The breakdown of activity was heavily skewed toward monetized data exposure. 6,979 incidents involved breached datasets or compromised information advertised for sale. Another 2,059 incidents centered on the sale of unauthorized access, including credentials, VPN entry points, and administrative footholds. Government, law enforcement agencies (LEA), BFSI, IT & ITES, healthcare, education, telecommunications, and retail remained in the most consistently targeted sectors.
Geographic analysis showed a clear concentration of activity in Asia, where 2,650 incidents affected organizations through breaches, leaks, or access sales. North America followed with 1,823 incidents, while Europe and the United Kingdom recorded 1,779 incidents. At the country level, the United States, India, Indonesia, France, and Spain experienced the highest volume of targeting during the year.
sectors and regions targeted by threat actors in 2025 (Source: Cyble)[/caption]
The breakdown of activity was heavily skewed toward monetized data exposure. 6,979 incidents involved breached datasets or compromised information advertised for sale. Another 2,059 incidents centered on the sale of unauthorized access, including credentials, VPN entry points, and administrative footholds. Government, law enforcement agencies (LEA), BFSI, IT & ITES, healthcare, education, telecommunications, and retail remained in the most consistently targeted sectors.
Geographic analysis showed a clear concentration of activity in Asia, where 2,650 incidents affected organizations through breaches, leaks, or access sales. North America followed with 1,823 incidents, while Europe and the United Kingdom recorded 1,779 incidents. At the country level, the United States, India, Indonesia, France, and Spain experienced the highest volume of targeting during the year.
 Ransomware attack trends between 2020 and 2025 (Source: Cyble)[/caption]
This pattern reflected widespread affiliate mobility. Ransomware-as-a-Service operators shared affiliates who moved between platforms, relisted victims, and reused stolen data to sustain pressure. Groups such as Cl0p, Qilin, Lynx, INC Ransom, Play, LockBit, and Crypto24 repeatedly claimed overlapping victims during short timeframes.
Several new groups, including Devman and Securotrop, initially operated within established RaaS programs before developing independent tooling and infrastructure. This progression blurred the line between affiliate and operator and further decentralized the ransomware landscape.
Ransomware attack trends between 2020 and 2025 (Source: Cyble)[/caption]
This pattern reflected widespread affiliate mobility. Ransomware-as-a-Service operators shared affiliates who moved between platforms, relisted victims, and reused stolen data to sustain pressure. Groups such as Cl0p, Qilin, Lynx, INC Ransom, Play, LockBit, and Crypto24 repeatedly claimed overlapping victims during short timeframes.
Several new groups, including Devman and Securotrop, initially operated within established RaaS programs before developing independent tooling and infrastructure. This progression blurred the line between affiliate and operator and further decentralized the ransomware landscape.
 Rebranded ransomware groups reported in 2025 (Source: Cyble)[/caption]
The year also saw widespread rebranding. Hunters International became World Leaks. Royal re-emerged as Chaos. LockBit 3.0 evolved into LockBit 4.5 and later 5.0. HelloKitty resurfaced as Kraken. At the same time, numerous groups dissolved or ceased operations, including ALPHV/BlackCat, Phobos/8Base, Cactus, RansomHub, and CrazyHunter.
Rebranded ransomware groups reported in 2025 (Source: Cyble)[/caption]
The year also saw widespread rebranding. Hunters International became World Leaks. Royal re-emerged as Chaos. LockBit 3.0 evolved into LockBit 4.5 and later 5.0. HelloKitty resurfaced as Kraken. At the same time, numerous groups dissolved or ceased operations, including ALPHV/BlackCat, Phobos/8Base, Cactus, RansomHub, and CrazyHunter.


 Image Source: X[/caption]
Image Source: X[/caption]

 Kyowon Group alerts users to a cyberattack on its systems (Source: Kyowon Group)[/caption]
A Kyowon Group representative confirmed the breach, stating, “We have confirmed indications of a breach,” while emphasizing that investigations were still underway. The representative added, “We are still investigating whether any personal information has been leaked.” The company also announced that it planned to release an official statement the following morning once more details were confirmed.
Kyowon Group alerts users to a cyberattack on its systems (Source: Kyowon Group)[/caption]
A Kyowon Group representative confirmed the breach, stating, “We have confirmed indications of a breach,” while emphasizing that investigations were still underway. The representative added, “We are still investigating whether any personal information has been leaked.” The company also announced that it planned to release an official statement the following morning once more details were confirmed.








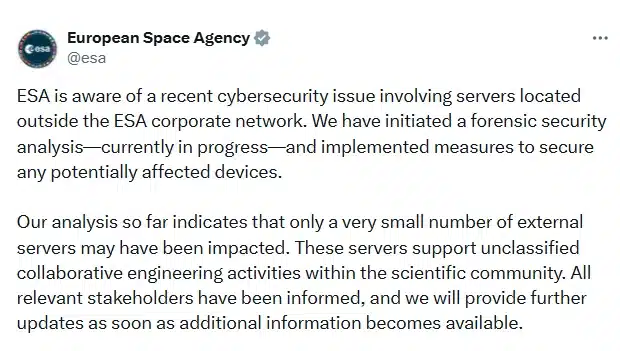 Source: ESA Twitter Handle[/caption]
ESA said it will provide further updates as additional details become available.
Source: ESA Twitter Handle[/caption]
ESA said it will provide further updates as additional details become available.
 Source: Data Breach Fourm[/caption]
ESA has not verified the authenticity or scope of the claims made by the threat actor.
So far, ESA has not disclosed which specific external servers were compromised or whether any credentials or development assets referenced by the threat actor were confirmed to be exposed.
Founded 50 years ago and headquartered in Paris, the European Space Agency is an intergovernmental organization that coordinates space activities across 23 member states.
Given ESA’s role in space exploration, satellite systems, and scientific research, cybersecurity incidents involving the agency carry heightened strategic and reputational significance.
Source: Data Breach Fourm[/caption]
ESA has not verified the authenticity or scope of the claims made by the threat actor.
So far, ESA has not disclosed which specific external servers were compromised or whether any credentials or development assets referenced by the threat actor were confirmed to be exposed.
Founded 50 years ago and headquartered in Paris, the European Space Agency is an intergovernmental organization that coordinates space activities across 23 member states.
Given ESA’s role in space exploration, satellite systems, and scientific research, cybersecurity incidents involving the agency carry heightened strategic and reputational significance.









 Source: French Interior Ministry[/caption]
Source: French Interior Ministry[/caption]











