Rapid7 Helps Lower Your Cost to Assurance for HITRUST
Organizations across regulated sectors are under growing pressure to prove their security readiness. At the same time, traditional assurance approaches rely on periodic audits and manual evidence collection. These activities take time, strain staff, and often fall out of date as environments evolve.
To help close this gap, Rapid7 has partnered with HITRUST to bring automated evidence collection and continuous validation of security controls to customers who follow HITRUST frameworks. This partnership builds on existing capabilities in the Rapid7 Command Platform and creates a more efficient path for organizations that need to demonstrate strong and reliable assurance.
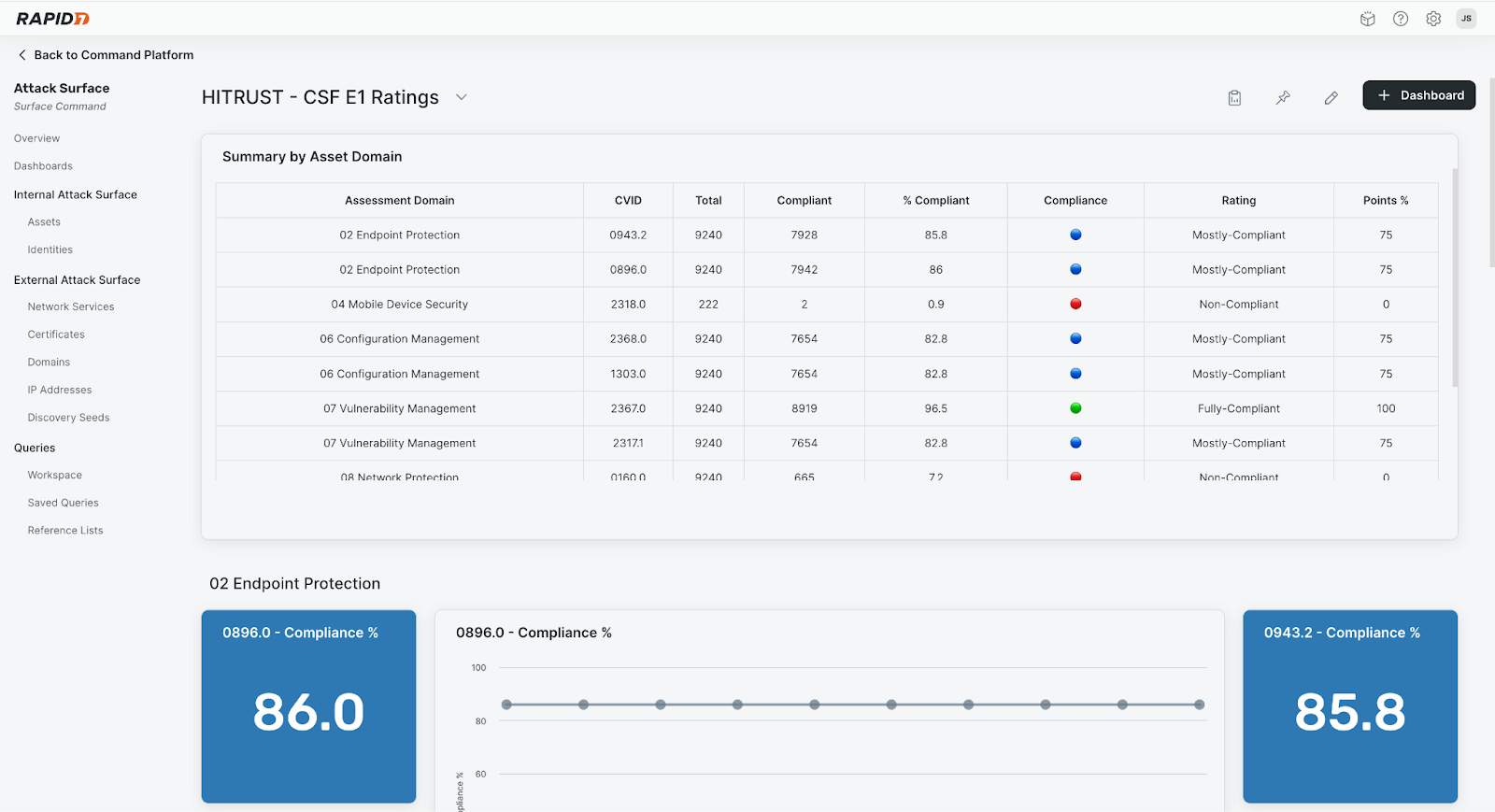
Rapid7 achieves this by leveraging our native telemetry and extensive support for third-party data sources; the Rapid7 Command Platform has visibility into vulnerabilities, exposures, configurations, identities, threat detections, IT context and more, the very same datasets that make up the evidence of technical compliance controls. Meaning that Rapid7 as a Security Operations platform, not only implements those very controls but can also help customers to prove those controls to lower their cost to certification. This is accomplished through automated evidence collection and continuous controls monitoring from Surface Command to detect things like compliance drift.
⠀
⠀
To help understand how Rapid7 can help our customers to assure against HITRUST and its many levels of assurance, we will provide a brief background on HITRUST.
The importance of HITRUST
HITRUST offers one of the most comprehensive cybersecurity assurance programs for risk, security, and compliance. Its framework is informed by more than 60 standards and is continuously updated based on active threats and risk thresholds. This helps close the gap between traditional checkbox compliance and the realities of modern risk.
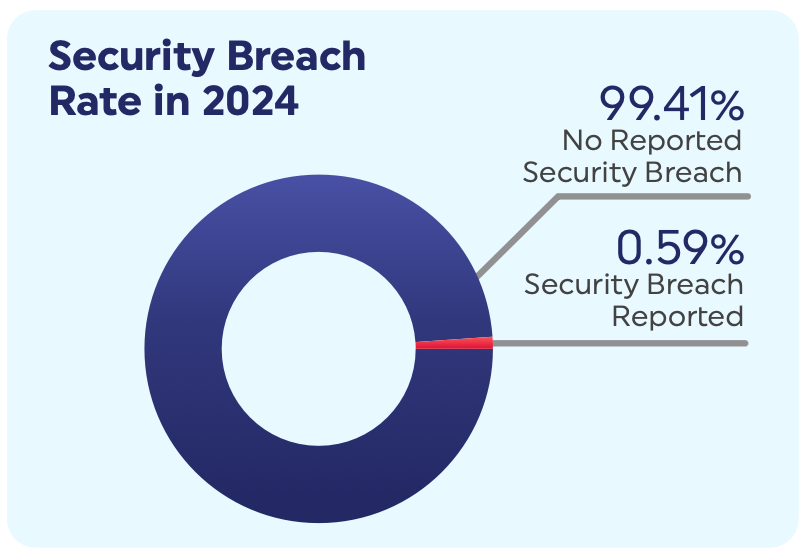
HITRUST has developed an all-encompassing compliance framework, a framework of frameworks, if you will. It’s the only compliance framework that is actively updated based on the latest attacker behavior and security threats, meaning it can further close the gap between checkbox compliance and actual risk reduction. It offers a portfolio of assessments and certifications that validate the security of systems, data and environment. They currently laude a 99.41% breach-free rate for organizations that have a HITRUST certification. This alone is a very compelling stat, yet there’s another area of differentiation that is worth mentioning. HITRUST assessors are entirely independent from the HITRUST organization. This independence provides organizations with a consistent and transparent way to validate their control performance. Achieving HITRUST assurance also extends coverage across several major frameworks, including ISO/IEC 27001, NIST CSF, HIPAA, and GDPR. This helps teams streamline overlapping requirements while working within a single, structured model.
⠀

⠀
What is HITRUST assurance?
Assurance, defined by HITRUST, is a token of trust that HITRUST designates to organizations that have been through the assurance process. There are two main requirements to be trustworthy:
The control set has to be relevant e.g. informed by latest attacker behavior
The control set has to be reliable, transparent and have an open scoring system and independent assessor network
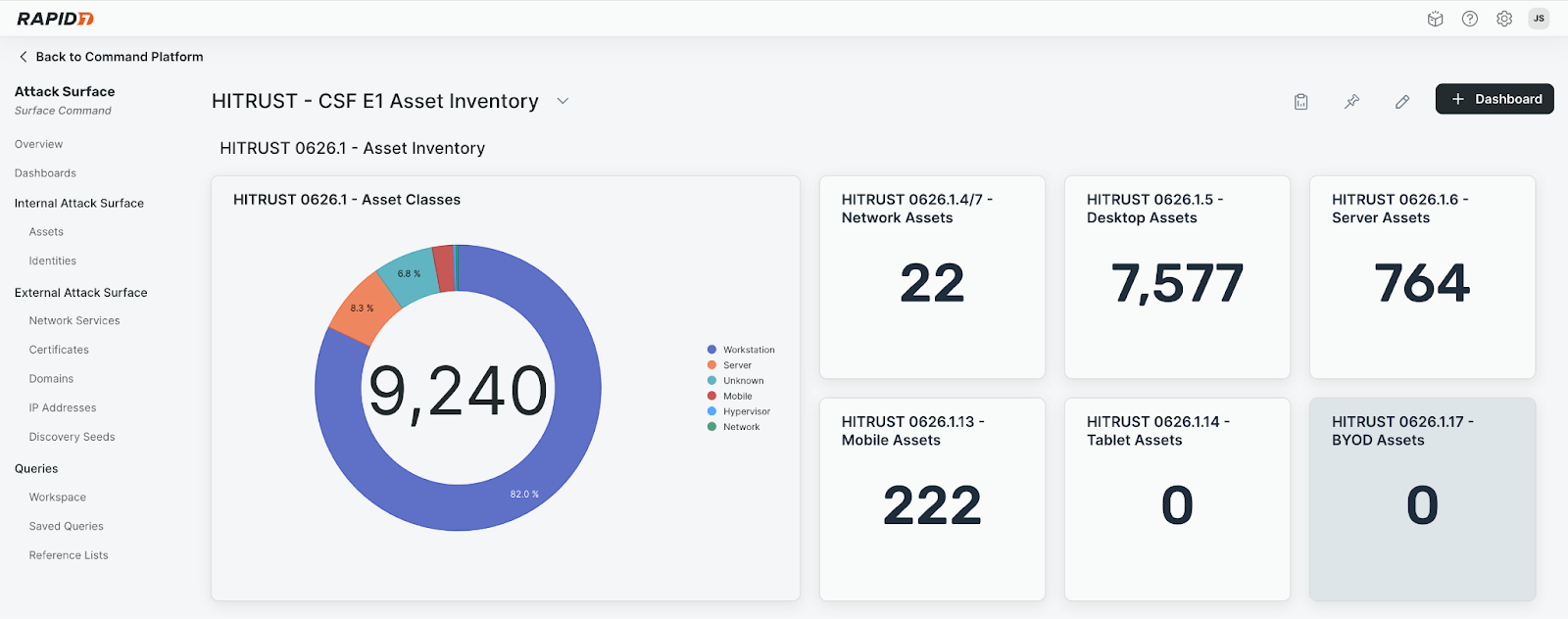
Customers are assessed by an independent network of HITRUST assessors (e.g audit firms) to evaluate if they meet the requirements of the HITRUST framework, which provides several levels of controls based on the size, sector, and risk profile of the organization. HITRUST provides a free CSF framework that has been downloaded by over 35,000 organizations. The r2 certification has been around the longest, for around 10 years and is the most rigorous. There is a newer certification called e1, which is an entry-level control set to help customers get started and is seeing the majority of adoption by new HITRUST customers.
The e1 currently has over 40 technical controls to adhere to, and the r2 is a combination of the control set from i1 (over 100 controls) with a per-customer set of controls based on the specific risk to that business. This means that no two r2 assessments are the same. Highlighting another key differentiator of HITRUST that goes beyond the check-the-box, minimal viable security approach to compliance.
⠀

⠀
Lastly, HITRUST frameworks are typically updated quarterly leveraging the latest research on threats and industry best practices. While this can be challenging for customers to maintain that have not adopted automated evidence collection, it ensures that HITRUST is providing a high quality risk-informed framework that drives meaningful security outcomes.
How the Rapid7 partnership strengthens assurance programs
Rapid7’s Surface Command provides customers with a complete internal and external view of their attack surface, including vulnerabilities, misconfigurations, assets, and exposure data. With this new integration, the platform can now collect, map, and validate technical controls against HITRUST requirements using the same datasets security teams rely on for day-to-day operations.
This automated approach supports several outcomes featured in the press release:
Continuous compliance visibility: The Command Platform assesses environments for control drift based on HITRUST requirements, which are updated in response to emerging threats.
Proactive risk mitigation: Customers can connect vulnerability and exposure insights with HITRUST controls to address areas that matter most.
Lower audit burden: Continuous validation reduces manual evidence collection and helps narrow audit scope to the areas that require attention.
Support for cyber insurance: Demonstrating consistent control performance can help organizations show strong risk management practices to insurers.
Lower costs: By reducing manual work and helping teams focus on priority controls, organizations can minimize the resource-intensive process associated with traditional assurance cycles.
To summarize, Rapid7 Command Platform can map & monitor technical controls to HITRUST e1, i1 and r2, and then by sampling them continuously, Rapid7 can detect control drift to identify areas that need attention, lowering the need for an expensive, comprehensive assessment. We can now help customers focus on remediating what needs attention and enable their assessors to look for only those areas that need addressing, instead of the full scope, ultimately saving costs during the evidence collection and assurance process.
Moving from periodic audits to continuous assurance
Moving from periodic audits to continuous assurance with Surface Command, Rapid7’s attack surface management (ASM) solution, provides our customers with a unified, continuously updated view of all assets and exposures in their organization through a combination of Rapid7 and third-party security data. Today’s security programs need approaches that keep pace with real threats and regulatory expectations. By pairing Rapid7’s visibility into security controls with HITRUST’s structured and independently assessed framework, customers can shift from point-in-time checks to a continuous, evidence-based view of their cybersecurity posture.
This partnership helps teams maintain confidence in their control performance, reduce evidence decay, and communicate program health more effectively to leadership and stakeholders.
Learn more here.
⠀