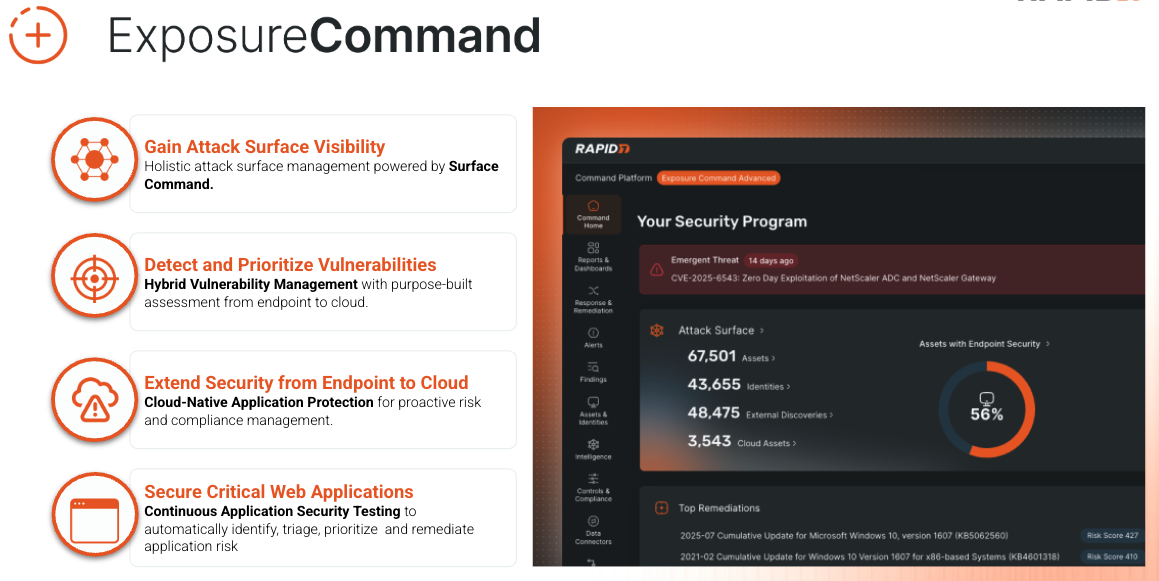
Dynamic EASM Discovery: Continuous Discovery for a Changing Attack Surface
Staying ahead of what’s exposed, automatically.
The modern enterprise doesn’t stand still. New domains are registered, acquisitions bring inherited infrastructure, cloud workloads spin up and down daily, and somewhere in the middle of it all, your visible footprint on the internet external attack surface keeps expanding.
For CISOs, this constant motion makes one CTEM step particularly difficult: discovery. You can’t validate what you can’t see and manual inventory updates can’t keep up with the pace of digital change.
That’s why Rapid7 is introducing dynamic EASM discovery for Surface Command, a new capability that automatically identifies and tracks every part of your external attack surface. By continuously ingesting known domain and IP information from your environment and related management tools, Surface Command ensures your visibility is always accurate, always current, and always ready for validation.
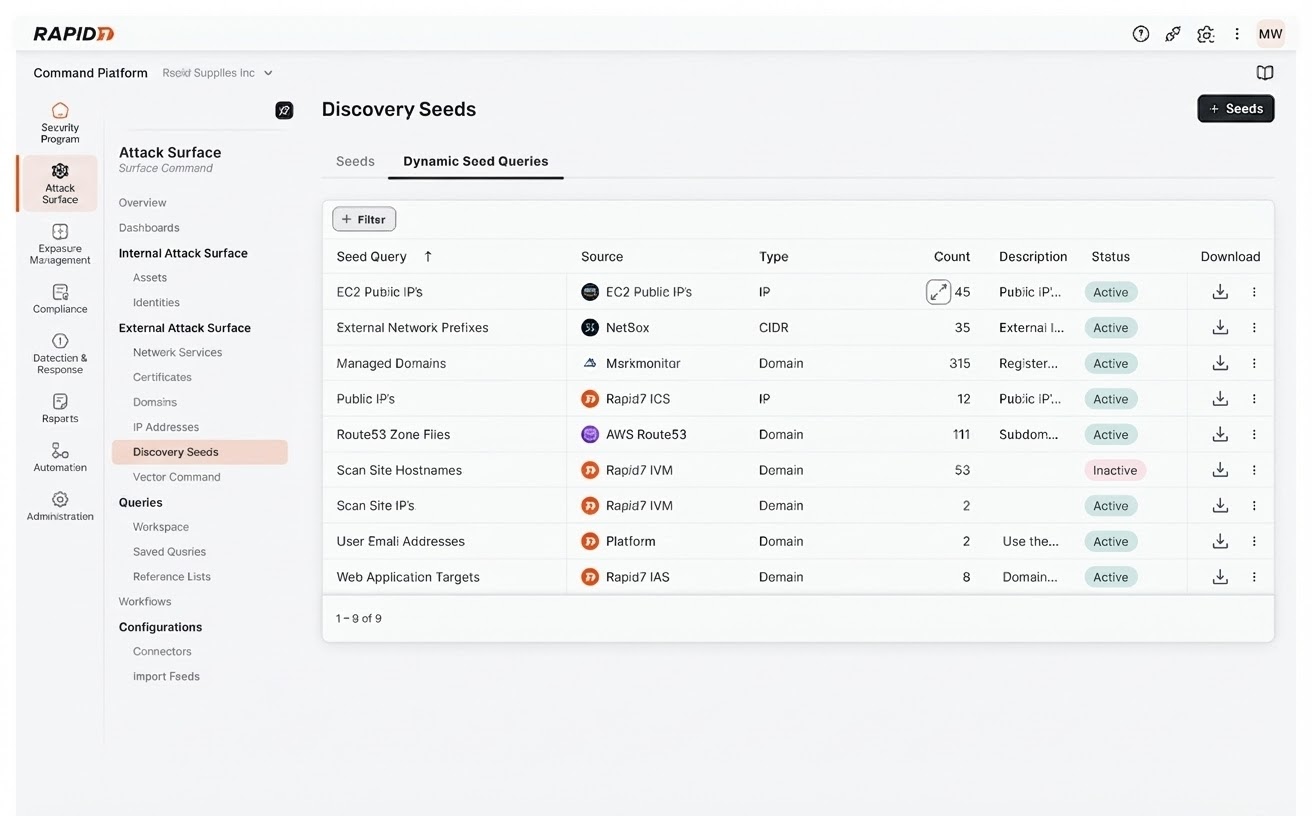
Figure 1: Dynamic Seeds feature in the Rapid7 Command Platform
From static inventories to continuous confidence
Traditional External Attack Surface Management (EASM) tools rely on static “seed lists”, known IPs, domains, or networks used to start discovery scans. But as organizations evolve, those seeds quickly become stale, leaving blind spots that attackers can exploit.
Dynamic EASM discovery replaces static inputs with live intelligence. Surface Command, Rapid7’s attack surface management (ASM) solution, now automatically gathers seed data from across your ecosystem, including DNS records, network services, and asset repositories and feeds it directly into the Rapid7 Command Platform. Asset, vulnerability, automation, control, threat, and enrichment data are ingested into our Command Platform through Connectors.
The result: a continuously updated, validated view of your internet-facing footprint.
No spreadsheets. No manual uploads. No surprises.
Why this matters for CTEM step 2: Discovery
Continuous threat exposure management (CTEM) is the discipline of constantly discovering, prioritizing, validating, and mobilizing against risk. Most organizations excel at discovery and prioritization but validation often lags behind.
Discovery is where confidence becomes measurable:
- Did the exposure we fixed actually disappear?
- Is our attack surface shrinking or just shifting?
- Are we making progress we can prove?
Dynamic EASM discovery strengthens step 2, discovery by ensuring your exposure data reflects the real, live environment. Every time a cloud resource changes or a new asset appears, Surface Command automatically revalidates what’s known versus what’s newly exposed.
That means your CTEM cycle is never out of sync with reality, and your reports to leadership reflect verified reductions in risk, not assumptions.
Connecting visibility to outcomes
Dynamic EASM discovery doesn’t just simplify inventory management, it accelerates progress across the CTEM lifecycle:
- Discovery: Continuously ingesting data expands your external visibility.
- Prioritization: Integrated context links assets to business impact and threat intelligence.
- Validation: Continuous seed refresh confirms exposures are resolved and risk is reducing.
- Mobilization: Validated insights flow into ITSM and automation workflows for closure.
For security leaders, this translates to clear, measurable progress: a smaller attack surface, shorter exposure windows, and data that executives can trust.
An attacker’s view you can trust
External visibility is only useful if it’s reliable. With dynamic EASM discovery, Surface Command provides a real-time, attacker’s-eye view of your organization’s public-facing assets, domains, subdomains, IPs, and network services; all validated against live data.
This level of automation gives CISOs three distinct advantages:
- Fewer blind spots - Automatically capture new and transient assets the moment they appear.
- Proven accuracy - Validate that remediation efforts have actually closed exposures.
- Faster decisions - Operate on verified intelligence instead of lagging asset data.
Validation becomes continuous, evidence-based, and defensible.
Executive clarity through proof
Boards don’t want more alerts, they want proof that investments in security are paying off. Dynamic EASM Discovery helps CISOs demonstrate that progress with concrete, validated metrics:
- Total external assets tracked over time
- Exposure reduction percentages by business unit
- Remediation velocity measured in real, verified outcomes
When the question comes, “are we actually reducing risk?”
Surface Command gives you evidence, not estimates.
Simplified operations, stronger security
Dynamic EASM discovery is built into Rapid7’s Command Platform, eliminating the manual effort that once slowed exposure management. Security and IT teams can focus on reducing risk instead of reconciling data sources, while automation keeps inventories and dashboards perpetually up to date.
In practice, that means:
- Reduced administrative overhead
- Elimination of stale or duplicate records
- Seamless integration with other Command Platform services for unified CTEM execution
What used to take hours of manual input now happens automatically, at the speed your business evolves.
Continuous validation made simple
Attack surface expansion doesn't stop, and neither should your visibility. With dynamic EASM discovery, Rapid7 ensures that the foundation of your CTEM program, discovery, is always grounded in current, accurate data.
It’s continuous assurance for a world that doesn’t stand still. This is in early access now, and generally available in January, 2026.
See how Dynamic EASM Discovery keeps your external visibility live, validated, and ready for action.
Contact your Rapid7 account team or click here to initiate a no commitment trial today.
Try the new dynamic EASM discovery self-guided product tour